
Dec 8, 2023 |
Cyber Security, Information Security | 1378
Authentication and authorization are two fundamental components of information security that are used to safeguard systems and data. Authentication is the method by which a user or service's identity is confirmed. At the same time, authorization determines what actions or resources a user or service is permit...
read more
Nov 14, 2023 |
Information Security | 1162
Tools alone are rendered ineffective without proper training. The development of digital technologies and the rise of connected devices, networks, and applications create new risks to our information systems and put more emphasis on IT security training.
As the speed of technology increases, so does the ...
read more
Nov 14, 2023 |
Information Security | 2769
The growth of Artificial Intelligence in the digital age has paved the way for some remarkable innovations, but it also led to some alarming technological developments. One such development is Deepfake AI, a concept that has attracted much interest in recent times. Deepfake AI is a potent and disputed combina...
read more
Aug 17, 2023 |
Cloud Security, Information Security | 4352
As cyber-attacks are increasingly growing, the need for strong security measures to protect organizations is not deniable. A cyber-breach can cost the organization a lot of money. So, what can we do to stop these security vulnerabilities? This is where strong cyber security architecture comes in the scenario,...
read more
Aug 10, 2023 |
Information Security, ISO | 3162
Information security is crucial in today's digital world to guard against threats like unauthorized access, misuse, or data loss. The fundamental principles of information security form the basis of a robust security strategy, encompassing best practices, methodologies, and techniques to safeguard critical in...
read more
Jun 16, 2023 |
Information Security | 3904
Security professionals can use a lifecycle model throughout their daily work lives, similar to most IT industries. As a security expert, using a lifecycle model gives direction and ensures that improvements are being made to the enterprise's security posture. Security programs are something you can only set u...
read more
Apr 20, 2023 |
Information Security | 2364
As the company progresses in the field of networking every day, resources and devices develop tremendously, resulting in an ever-increasing risk of exposure. Nowadays, every company is putting all of its operational data on the cloud infrastructure, which is raising cyber risks and placing the firm's assets, ...
read more
Feb 14, 2023 |
Information Security | 3816
The ever-increasing use of technology in business operations of all sizes and orientations has made information security a critical consideration. In today's digital world, businesses rely heavily on technology and the internet to conduct their operations. The increasing use of technology increases the risk o...
read more
Nov 3, 2022 |
Information Security | 2173
With the demand for qualified information security professionals soaring, certification is a logical way for you to verify your skills and knowledge and to get your resume noticed. Therefore, earning a certification will surely boost your career to the next level.
Information security certificates teac...
read more
Sep 13, 2022 |
Information Security, ISO | 3851
Table of Contents
What is ISO 27001?
ISO 27001 Audit
Types of ISO Audit
What is ISO 27001?
The International Organization for Standardization developed ISO 27001 as a standard. It is the foundation for an organization's Information Security Management System (ISMS). The standard is divided into two...
read more
Jul 14, 2022 |
Information Security | 1893
Table of Contents
Information Security covers three objectives
Job description for an Information Security Specialist
Starting a career in Information Security
Consider obtaining a relevant degree
Get one or more relevant certifications
Unauthorized access is merely one aspect of Information Securit...
read more
Jul 13, 2022 |
Information Security, IT Services | 8104
Many people feel that Information Security is the same as Information Technology and that their I.T. man is in charge of their whole cybersecurity. This is a typical misunderstanding since Information Technology focuses on technology rather than security. The distinction among Information Technology and Infor...
read more
Jan 28, 2022 |
Information Security | 2439
A Security Consultant assesses risks, challenges, and solutions for security concerns for various businesses. A Physical Security Consultant or an IT Security Consultant who works with computers are two options for a person who desires to become a consultant. Whether you work as an IT Security or a Physical S...
read more
Jan 21, 2022 |
Information Security | 5923
Passwords are the foundation of security and are required for almost everything. It's now essential for your email, bank accounts, and digital gadgets, among other things. It might be terrible if your personal or private information fell into the wrong hands. Always remember your password is as valuable as yo...
read more
Jan 19, 2022 |
Cyber Security, Information Security | 3821
Even among those in the security field, the terms "cybersecurity" and "information security" are used interchangeably.
However, the two terms are not synonymous. Each of them addresses different kinds of security, and every organization investing in a proper security framework must understand each term, wh...
read more
Dec 28, 2021 |
Information Security | 2273
Log4j is a piece of code that helps software applications keep track of their previous activities. Developers often use Log4j while building new software instead of reinventing logging or record-keeping components. The Log4j program is designed to help programmers output log statements to various output targe...
read more
Dec 6, 2021 |
Information Security | 1350
Information has become very valuable for us over the last few years, whether it be the messages we send, files in our systems, or complete data of an organization. It is and will be one of the essential parts of our personal and professional lives. So, it is imperative to protect the information from unauthor...
read more
May 28, 2021 |
Information Security | 3566
There is only one place to go if you want to visit a website that is illegal under federal law, and that is the darknet anonymous markets. Since these pages are located in a secret section of the internet known as Tor hidden services, you won't be able to access them using a standard browser like Chrome or Ed...
read more
Oct 6, 2020 |
Information Security | 1943
With privacy becoming an integral part of every organization today, a much more robust approach is needed to handle it. This has resulted in the creation of the ‘Privacy management program,’ which is a much more holistic and unified approach for handling privacy that can be adopted by all organizations, c...
read more
Sep 24, 2020 |
Information Security | 2334
The cybersecurity industry has been home to various job roles, and one of them is the 'cybersecurity consultancy.' A cybersecurity consultant builds a secure environment for any organization by being the mind of their security team. If you are someone planning to have a career down this path, here is an overv...
read more
Sep 23, 2020 |
Information Security | 1408
The recent digital revolution has brought a significant change to our lifestyle by meeting all our needs at just one click. Cybersecurity is the backbone of this industrial transformation. The surge in the use of smart devices and social media interactions have unveiled many loopholes and vulnerabilities in t...
read more
Aug 20, 2020 |
Information Security | 2248
In today's digital world, cyber-attacks are an absolute certainty. While the basic types of attacks are still prevalent, new types of attacks have also metamorphosized, creating more monetary and physical destruction. Here are the Top 10 Cyber Security Attacks that are highly prevalent today.
Brute...
read more
Aug 3, 2020 |
Information Security | 1844
With the intention of performing a Bitcoin scam, the twitter handles of 130 high profile people were hacked.
The proceedings of the event began on 15th July 2020 at around 16:00 Hours in the US when attackers hacked and took over control of many high profiles and mostly verified Twitter accounts of those l...
read more
Jul 21, 2020 |
Information Security | 1926
The internet and mobile technology rule the world presently. It is practically impossible to achieve any task without the use of these. However, technological advancements always bring some setbacks in the form of security threats. As the number and varieties of cyber security threats increase every day, the ...
read more
Jul 12, 2020 |
Information Security | 1572
What is OWASP?
OWASP is the abbreviation of Open Web Application Security Project. It is an online forum which publishes articles, documentations, technologies and tools pertaining to web application security.
How to define OWASP Top 10?
OWASP Top 10 is the most looked up to a list of the top 10 most...
read more
Jun 15, 2020 |
Information Security | 1724
‘Endpoint security’, ‘Perimeter security’, ‘Security by obscurity’, ‘Layered security’ – these are some approaches that are present till date to safeguard business and personal networks. In spite of the different approaches, data breaches, ransomware attacks and other novel ways to gain pers...
read more
May 3, 2020 |
Information Security | 1373
During these testing times of the COVID-19 pandemic, the international advisory has been issued that asks employees to work from home. This opens the door for possible cyber security threats as lakhs of employees are now working from home due to the lockdown.
Various industry experts have suggested tha...
read more
Apr 21, 2020 |
Information Security | 3438
With the Coronovirus pandemic locking almost every state, city and country in the world, professionals from every sector are working from home to achieve their business objectives. ‘Zoom’ the video conferencing software, has been the leader in powering most businesses in this difficult time. ‘Zoom’ ...
read more
Mar 18, 2020 |
Information Security | 1186
The outbreak of COVID 19 has made the world standstill. We are all in this together and doing everything possible to get over this situation and stop the further spread of this deadly virus. Organizations around the globe are being sensitive to this situation and therefore, are allowing the employees/students...
read more
Mar 16, 2020 |
Information Security | 3246
The world is in the midst of the deadliest Coronavirus pandemic and we can see business slowing, transportation disruptions, schedules being uprooted, educational institutions closing and many other changes in our lives. Even as the nature of crisis is magnanimous and dangerous, there are quite a few who ...
read more
Mar 15, 2020 |
Information Security | 1405
Hey guys, I always write articles, share posts from some sites that I follow and find relevant. Among these various experiences that I have been exchanging with professional friends, the question that always comes to mind is:
"Where do I start studying to migrate to safety?"
I decided to write how I...
read more
Jan 25, 2020 |
Information Security | 1508
iPhones are more secure than Android phones? Think again… Jeff Bezos, the founder, President and Chief Executive officer of Amazon had his iPhone 10 hacked in 2018 and the details are still being revealed.
Any connected device is vulnerable to a variety of hacks and attacks. With smart phones storing...
read more
Jan 7, 2020 |
Information Security | 1257
The New Year is already upon us but who can forget the Capital Data breach, the Canva hack and the various ransomware incidents that shook the various organizations the past year? With so many hacks and attacks in 2019, what can we expect from 2020? Read on to see some of our predictions!
Ransomware ...
read more
Nov 20, 2019 |
Information Security | 1262
Close on the heels of the ‘Pegasus’ spyware, the Internet was again abuzz with yet another Whatsapp vulnerability on Monday, 18th November 2019. This time:
Hackers send a specially crafted .mp4 file to a Whatsapp user which could trigger a stack based buffer overflow.
This could enable the hac...
read more
Nov 5, 2019 |
Information Security | 1405
It did happen again. Even as most of us were touting Whatsapp to be the most secure messaging platform, another attack on the world’s most popular messanging platform shook everybody…again!
As an introduction, Whatsapp is end-to-end encrypted messaging platform that was supposedly the most secure commu...
read more
Oct 12, 2019 |
Information Security | 3902
Security professionals, tasked with protecting the information assets of an organization, typically think of their responsibilities in three realms: confidentiality, integrity, and availability (CIA). The adversaries/attackers, seeking to disrupt an organization’s security, have three corresponding goal...
read more
Sep 29, 2019 |
Information Security | 5910
DOS Attack: A Denial-of-Service (DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic, or sending it information that triggers a crash. In both instances, the DoS attack deprives legitima...
read more
Aug 20, 2019 |
Information Security | 1461
With almost all businesses moving online, what would happen if it was unavailable even for a few hours in a day? Business would slump, leads would be lost, new business relationships cannot be forged, profits would fall and this may lead to other disasters within the organization as well. This is exactly what...
read more
Jul 18, 2019 |
CCSP, CISA, CISSP, CompTIA, Information Security | 1595
Imagine what happens when you use an app for fun and it turns out to be saving all your data silently? Even this thought of being vulnerable on this online space gives us a chill. But this is what has been actually discovered being done by the viral Faceapp. Yes! you read it right!
Faceapp is one of the mo...
read more
Jul 18, 2019 |
Information Security | 2006
‘Federated identity management’ has its origins in the concepts of ‘Single sign on’ and ‘Identity management’. In order to completely understand ‘Federated identity management’ we have to skim through these concepts first.
‘Identity management’ is authenticating and authorizing differen...
read more
Jul 9, 2019 |
Information Security | 1776
Have you ever stopped to think about what it would be like to get home and discover had your property invaded? or you leave your car in a parking lot and upon returning to search you find out that it was broken into? This type of concern also occurs in information technology environments. Nowadays independent...
read more
Jun 25, 2019 |
CompTIA, Information Security | 1466
CompTIA Security+ certification is an assurance that a professional has mastered the latest skills and concepts that are the foundation to start a career in cybersecurity. IT professionals with Security+ certification are better prepared to sort out multiple issues when securing and fencing networks against c...
read more
May 17, 2019 |
Information Security | 1232
As most of us may be aware, Whatsapp is a free, popular cross-platform messaging service by means of which one can send text messages, voice messages, images, documents and make video calls. It is owned by Facebook and is currently used by over 1.5 billion people worldwide. The conversations that take place o...
read more
May 8, 2019 |
Information Security | 1203
Learning new skills and enhancing your knowledge is the key for the growth of a career in any domain. Since Cybersecurity is one of those fields where new challenges keep rising on the regular basis, being a consistent learner is the only option which will help you to stay for long. So, if you are an IT profe...
read more
Apr 11, 2019 |
Information Security | 1409
Efficient Cybersecurity is the concern of the organization around the globe. Attackers are getting smarter day by day which compels the cybersecurity professionals to update their skillset on a regular basis. CompTIA Cybersecurity Analyst (CySA+) Certification is one such opportunity for the IT Professionals ...
read more
Feb 23, 2019 |
Information Security | 1566
The launch of COBIT 2019 has created ripples in IT service management. Every organization irrespective of their turnover and size is talking about this upgraded version of COBIT 5. There is a mixed reaction to this upgradation from ISACA. Some believe that this new version was much needed in the present time ...
read more
Dec 27, 2018 |
Information Security | 1119
Social media, the restaurant industry, credit reporting agencies – it looks like none of the industries were spared the impact of breaches in 2018. With the year reporting lesser breaches than 2017, it was still a whopping 945 breaches that led to a leakage of 4.5 billion records in the first half of 2018. ...
read more
Dec 21, 2018 |
EC Council, Information Security | 1975
‘Social Engineering’ in the context of information security, refers to the manipulation of people to execute an action or to release confidential information. It can be called a ‘method attack’, where one makes use of persuasion, sometimes abusing the user’s trust, to get information that can be u...
read more
Nov 25, 2018 |
Information Security | 1351
We all would agree to the fact that internet today has become an inseparable part of our lives. At the same time we are also aware that the convenience of the internet, along with itself has brought a threat to cyber security. The news of personal datas getting hacked doesn’t even surprise us anymore. Even ...
read more
Jul 10, 2018 |
CISSP, Information Security | 1484
A critical element of cryptocurrencies such as Bitcoin is Blockchain technology. A blockchain is a digitized, decentralized, public ledger of all cryptocurrency transactions. Its foundational element, the block, records some or all of the recent transactions. A block goes into the blockchain as a pe...
read more
Jul 10, 2018 |
Information Security | 1066
Ransomware was biggest online threat of 2017, overshadowing all other forms of cybercrime. It is a form of malicious software (or malware) that takes over your computer and threatens you with harm by encrypting all the personal data and documents and denying you the access. T...
read more
Jun 25, 2018 |
Information Security | 1297
A very important aspect of IT certification in Information security is to provide an in-depth knowledge to the professionals such that they recognize the need of highly skilled security experts to prevent ethical hacking and secure the network of an organization.
Why is Pentest + the next best cer...
read more
May 9, 2018 |
General, Information Security | 1307
Bitcoin was a nonexistent term in the past but now it is catching up really fast and grabbing everyone’s interest. Bitcoin is a cryptocurrency, well what is that? It is virtual money based on the technique of cryptography, not owned by any individual, corporation or government. It simplifies payments, m...
read more May 9, 2018 |
CISSP, General, Information Security | 2510
Although Certified Information Systems Security Professional certification is a instant enhancement to a person’s resume, there are other CISSP concentrations as well which equip professionals in a better and more encompassing way. They not only provide better salaried jobs but also with lot more responsibi...
read more
May 9, 2018 |
General, Information Security | 1283
Data protection the more passionate companies are towards protecting their data, the more determined hackers are in invading your space, your priority files and your chances of success. There are various anti-hacking techniques at work, but these don’t deter the hackers but that is because it is importa...
read more
Mar 21, 2018 |
Information Security | 1519
Kali is a complete re-build of BackTrack Linux, adhering completely to Debian development standards. All-new infrastructure has been put in place, all tools were reviewed and packaged, and we use Git for our VCS.
More than 300 penetration testing tools: After reviewing every tool that was included in Ba...
read more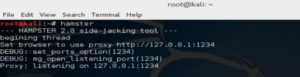
Mar 21, 2018 |
Information Security | 3013
You know that everything sent over Wi-Fi is vulnerable to eavesdropping. A handful of hotspots now encrypt user data—usually with WPA—but the vast majority still expect customers to protect themselves. Sadly, many users continue to ignore even this simple threat. Those who know better often defend their d...
read more














































































 Certified & Experienced Instructors
Certified & Experienced Instructors Post Training Support
Post Training Support Customized Training
Customized Training Flexible Schedule
Flexible Schedule Access to Recorded Sessions
Access to Recorded Sessions 
















 1800-843-7890 (India)
1800-843-7890 (India) 
