CERTIFIED SOC ANALYST (CSA) Certification Training
 Read Reviews
Read Reviews
Certified Security Analyst Certification will help you to start your journey towards joining a security operations centre (SOC).SOC Analyst Certification aims at offering proficiency in performing entry-level and intermediate-level operations and therefore, it is helpful for both already existing as well as aspiring Tier I and Tier II SOC analysts





 5th Sep: Weekend
5th Sep: Weekend 


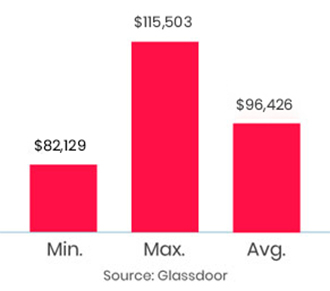

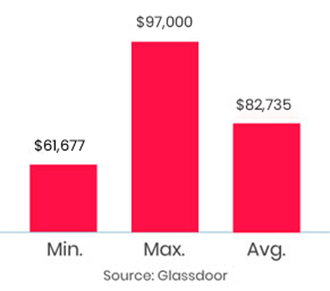

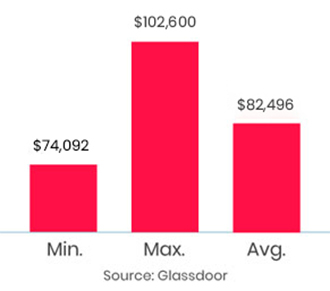


 It was a great experience,got opportunity to explore many new things and able to sort out doubts logically.
It was a great experience,got opportunity to explore many new things and able to sort out doubts logically.




 Certified & Experienced Instructors
Certified & Experienced Instructors Post Training Support
Post Training Support Customized Training
Customized Training Flexible Schedule
Flexible Schedule Access to Recorded Sessions
Access to Recorded Sessions 




 1800-843-7890 (India)
1800-843-7890 (India) 
