Cybersecurity Analyst x Pentester

Security professionals, tasked with protecting the information assets of an organization, typically think of their responsibilities in three realms: confidentiality, integrity, and availability (CIA). The adversaries/attackers, seeking to disrupt an organization’s security, have three corresponding goals in mind: disclosure, alteration, and denial (DAD). These models, are known as the CIA and DAD Figure-1 triads and are used by many security professionals around the world.

The CIA and DAD triads are classic models of information security principles.
Cybersecurity professionals use a well-known model to describe the goals of information security. The CIA triad, show in Figure-1. Includes the three main characteristics of information that cybersecurity programs seek to protect.
- Confidentiality measures seek to prevent unauthorized access to information or systems.
- Integrity measures seek to prevent unauthorized modification of information or systems.
- Availability measures seek to ensure that legitimate use of information and systems remains possible.
Attackers or Pentester, and therefore penetration testers, seek to undermine these goals and achieve three corresponding goals of their own. The attacker’s goals are known as the DAD triad Figure-1.
When we talk about Cybersecurity Professionals is necessary to keep in mind that they need to have known of concepts about security, technicals, and tools that are used day by day to defense and attack. That professional need to have mind-set of an Attacker or Pentester, a knowledge advanced about many kind attacks, as well as SQL Injection, Cross-Site Scripting (XSS), Cross-Site Scripting (XSS) Stored, Man-In-The-Middle (MITM), Brute-Force, Remote Code Execution, File Include, Directory or Path Traversal, Code Obfuscation, and more others concepts. The difference between that actors is the role that each one runs in an environment..
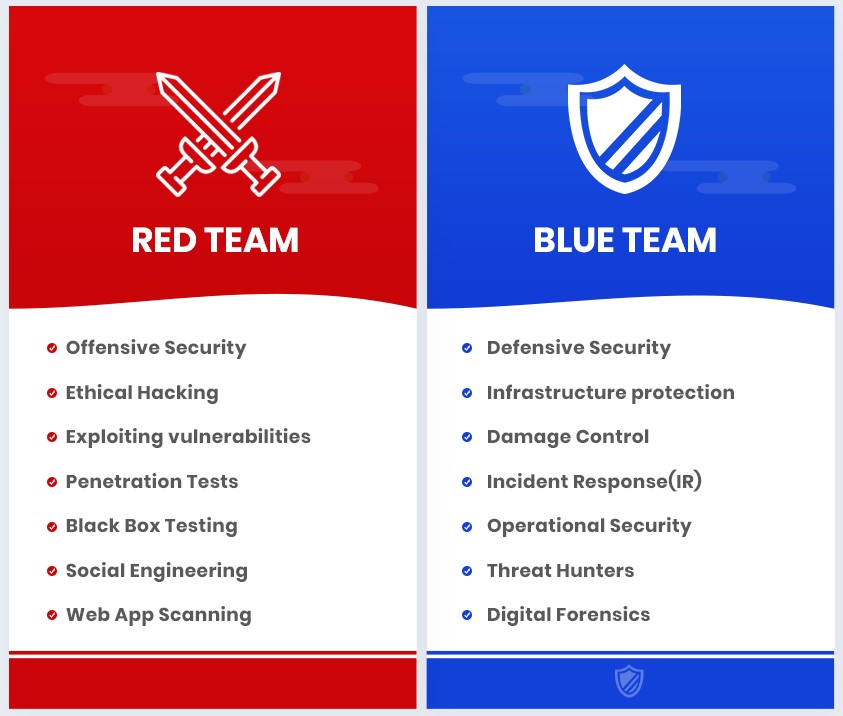
The infographics below show some roles of each team.
Below have some tools used to both professionals:-
Scanners
- Nikto
- OpenVAS
- SQLmap
- Nessus
- Nmap
OSINT
- WHOIS
- Nslookup
- FOCA
- theHarvester
- Shodan
- Maltego
- Recon-ng
- Censys
Remote Access Tools
- Secure Shell (SSH)
- Ncat
- Netcat
- Proxychains
Credential Testing Tools
- Hashcat
- Medusa
- Hydra
- CeWL
- John the Ripper
- Cain and Abel
- Mimikatz
- Patator
- DirBuster
- W3AF
Wireless
- Aircrack-ng
- Kismet
- WiFite
Networking Tools
- Wireshark
- Hping
Debuggers
- OllyDbg
- Immunity Debugger
- GDB
- WinDbg
- IDA
Web Proxies
- OWASP ZAP
- Burp Suite
Mobile Tools
- Drozer
- APKX
- APK Studio
Software Assurance
- FindBugs/find-sec-bugs
- Peach
- AFL
- SonarQube
- YASCA
Social Engineering Tools
- SET
- BeEF
Miscellaneous Tools
- SearchSploit
- PowerSploit
- Responder
- Impacket
- Empire
- Metasploit framework
Script Language
- Bash
- Powershell
- Python
- Ruby



 1800-843-7890 (India)
1800-843-7890 (India) 
