The Twitter Hack
With the intention of performing a Bitcoin scam, the twitter handles of 130 high profile people were hacked.
The proceedings of the event began on 15th July 2020 at around 16:00 Hours in the US when attackers hacked and took over control of many high profiles and mostly verified Twitter accounts of those like former US president Barack Obama, Bill Gates, Jeff Bezos, Elon Musk, etc. Upon gaining access to these trustworthy accounts, the attackers tweeted with a message which stated that any bitcoin link that was sent to that particular account would be doubled and sent back.

The counterfeit tweets proposed $200 for every $100 sent to a Bitcoin address. After a while, the hackers deleted these tweets and retweeted fake tweets when people began demanding for the doubled value. Upon noticing such bizarre happenings, the Twitter support team immediately obstructed the activities of these hacked accounts.
Twitter’s effort in deleting these Tweets went unsuccessful when few of the hacked handles being posting the carbon-copied messages again.
Who were the ones affected by the hack?
Twitter accounts of vital US politicians, celebrities, and high-profile personalities were hacked. Certain names of hacked accounts highlighted were Barack Obama, Elon Musk, Joe Biden, Apple, Uber, Kanye West, Kim Kardashian, and many others.
Many Twitter users duped the whole situation as “Digital Money Heist.” However, unfortunately, some of the users found these tweets legitimate and hence fell prey to the hack and ended up giving away their bitcoins as part of the scam, and this resulted in thousands of people being a victim of the scam.
Reportedly, the message of this tweet reached around 350 Million users with the favor of Twitter’s internal systems. The hackers behind this mass breach were able to sham bitcoin worth $120,000 through at least 300 transactions, which can also be referred to as the easiest bitcoin mining so far.
However, a brief about the incident was demanded from Twitter by the US Senate Commerce Committee. According to Twitter, this was a very well-coordinated attack that targeted employees of Twitter who had access y8to the internal portals, tools, and systems. Currently, Twitter has blocked all its users from tweeting addresses containing details bitcoin wallet.
It was Kayvon Beykpour, Twitter’s product lead who took it to Twitter to communicate the incident. This was trailed by a series of tweets from the Twitter Support team.
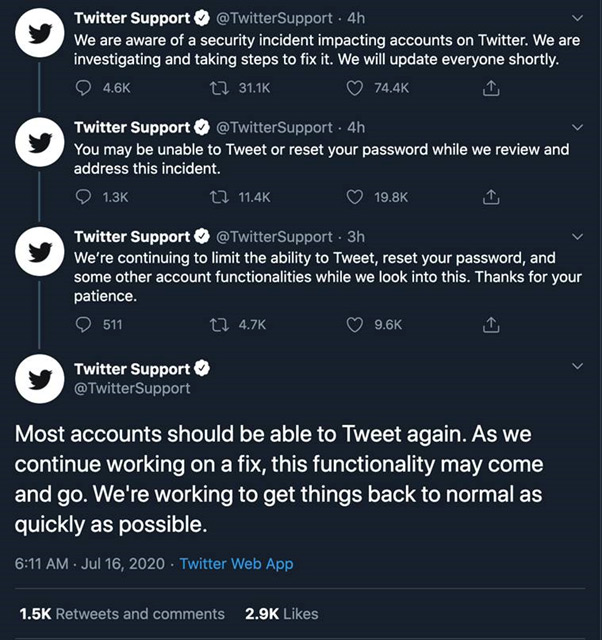
Image Source: https://indianexpress.com/
How did the events of the hack take place?
The rationale behind this co-ordinated Twitter hack was because of an employee from Twitter itself, although the investigation is still going on. One of the hackers expressed that they aided from a representative who did all the work for the hackers during the compromise. On the contrary, another one mouthed that they paid an insider to get the job done.
It has been delineated that the internal tool was used as part of the compromise to reset the correlated email addresses of all the hacked accounts to make it nearly impossible for the original account holders to repossess control. Preceding this, the scammers pushed a cryptocurrency scam and, lastly, launched the attack.
Even before the attack was launched, Twitter mentioned that the hackers had manipulated many of their employees (using the social engineering technique) into giving up sensitive information like the credentials of their internal tools and systems. Initially, Twitter’s analysis indicated that the DM’s of none of the compromised accounts were accessed. However, it was found out that the DM inbox of 36 users was accessed.
The scammers even managed to reset the passwords for 45 users, whilst downloading the entire data including the private messages of 7 users (earlier, it was mentioned that 8 users’ data was downloaded, perhaps the download was not finished for 1 user). It was even mentioned that these hackers might have tried to sell off the usernames of a few of the compromised accounts.
Twitter mentioned that the “phone spear-phishing attack” technique was used to gain access to the internal network. They have not yet confirmed as to how many of their employees have access to the internal network, also, yet to throw light on what kind of “phone spear-phishing attack” was used.
A tensed buzz was raised amongst individuals when it was highlighted that the Twitter accounts of US politicians were compromised due to the US elections coming up in November 2020. As the platform was blocked for hours long, this prevented many prominent users from posting.
The possible information about hackers?
As of 31st July 2020, 2 teens and 1 other, namely; Graham Ivan Clark (17), the alleged “mastermind” behind this hack, Mason Sheppard (19) of United Kingdom and Nima Fazeli (22) from Orlando have been arrested. More information of them can be found here:Masterminds behind Twitter Breach
How could the attack have been prevented?
This incident has triggered an urgent need amongst all social media platforms to cross-check their security measures. Based on the latest update as to how the credentials were extracted from the employees using the spear-phishing technique, without a doubt, it can be acknowledged that the weakest link in the “User.”
It does not matter if having the most scrutinized endpoint monitoring systems deployed in the systems unless organizations provide the basic and proper security awareness training to its employees. Credentials with least privilege practices need to be followed. Multi-Factor Authentication must be in place for all users. Organizations need to keep a watch out on the dark web and darknet for malicious behaviors related to accounts. Backdoors (admin/super admin) need to have the least privilege possible with additional critical security monitoring in place. Stressing the aforementioned point again, one must never forget the 8th layer of the OSI model, the Human Layer. The best possible investment in terms of increasing security in any organization is to invest in the Human Layer by providing as much cybersecurity awareness as possible. Educate! Educate! Educate! The User!
InfosecTrain is one of the finest Security and Technology Training and Consulting organization, focusing on a range of IT Security Trainings and Information Security Services. InfosecTrain offers various Training & Certification. To know more about courses and other trainings we conduct, Click Here



 1800-843-7890 (India)
1800-843-7890 (India) 
