What is Firewall
Have you ever stopped to think about what it would be like to get home and discover had your property invaded? or you leave your car in a parking lot and upon returning to search you find out that it was broken into? This type of concern also occurs in information technology environments. Nowadays independently of the branch in which one works the use of the technology of information is fundamental, for example, information storage of clients, generation of invoices, sending of data or budget. These are some of the many situations that we can mention to exemplify the use of technology in the human being’s daily life. Most companies have a proprietary data center or cloud to maintain and support servers that publish applications, store database, and provide some kind of online service. There is usually great concern about the integrity, confidentiality, and availability of this data. Depending on the industry, any loss or leakage of data can trigger a negative reputation on the companies and revenue.

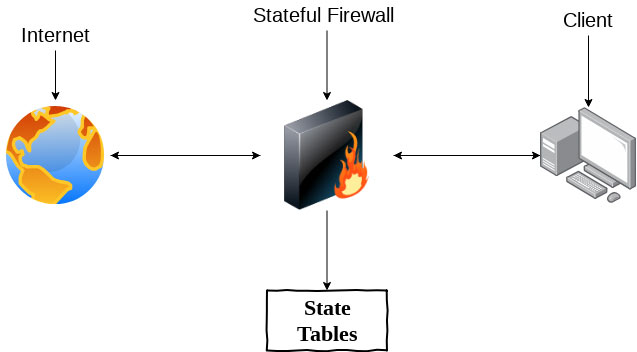
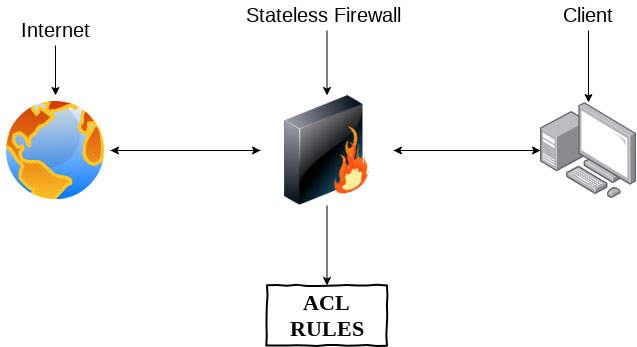
At some point in your life, you may have wondered what tools these companies use to try to keep their customers’ environment, servers, and data protected from theft. In the early days of information technology, we had as the initial basis of an environment what we call a firewall. This tool went through three generations. The first one came in the 1980s and was based on packet data filtering, with a simple methodology, limited but with a relevant level of security. Working with header analysis with has much information about the package, such as source/destination IP address, size, type of service and other characteristics. Based on this header information and with the established rules, the package is released (for outgoing or incoming network), these actions or attempts can also be registered in a file that we call log. The second generation was developed in the ’90s and had the premise of the session state analysis because the TCP transport protocol was oriented by a state table of connections, the packet filters were not effective enough if they did not observe these characteristics. Also known as a stateful firewall, it works by storing the state of connections and filters based on that state. There are three states for a connection: new (new connections), established (established connections), and related connections.
Example Stateful Firewall:
Example: Stateless Firewall:
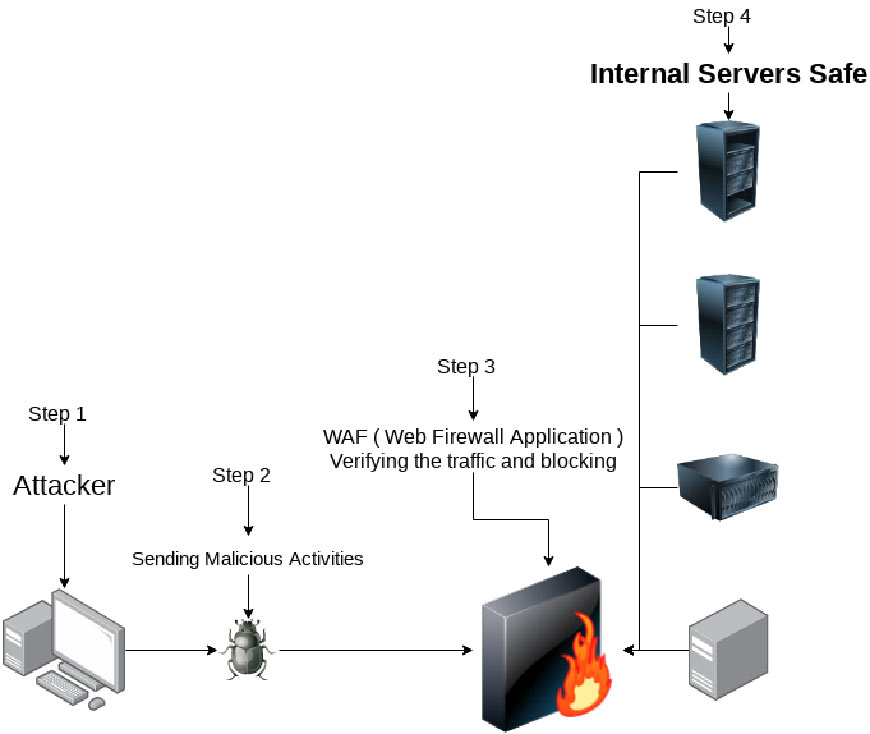
The third-generation firewall based on the work of Gene Spafford (co-author of Practical Unix and Internet Security), Marcos Ranum (founder of TIS) and Bill Cheswick. Also known as an application firewall. With the diversity of services offered through the internet, the HTTP protocol has become the basis for many applications such as portals and e-commerce. The HTTP protocol was responsible for a significant number of applications, opening space up for new applications to be developed using their own protocols and communication ports. The truth is that the internet has grown so much that it has become a great hub of communication and business platform. This way, the services offered by the internet, which are quite representative, tended to grow. As a consequence of these developments, controlling access by addresses, ports, and protocols, no longer met the needs of some security policies. This type of firewall brought the concept of layer 7 analysis (application), where the solutions were able to identify behavior patterns, not only in the headers but also in the data area of the packages, and to establish which type of application is linked.
A Simple example of the topology of a Web Application Firewall



 1800-843-7890 (India)
1800-843-7890 (India) 
