Advanced Penetration Testing Online Training Course
 Read Reviews
Read Reviews
Advanced Penetration Testing training course by Infosectrain focuses on demonstrating advanced techniques to perform penetration testing. The APT online course will not only train you to perform professional security but will also teach about the next most important thing which is the findings and the report making. This training will help you to prepare for the OSCP, LPT Master Certification & many more.






 5th Sep: Weekend
5th Sep: Weekend 



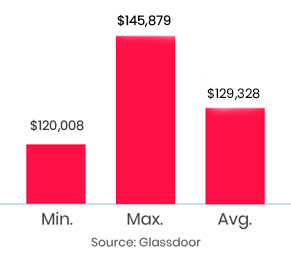

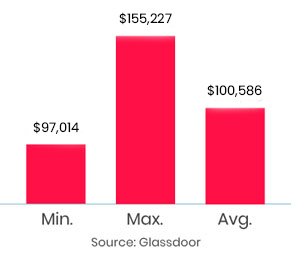

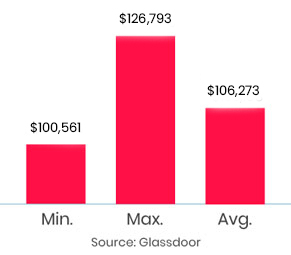



 The APT course was great. I would like to thank InfosecTrain for the valuable course with experience and skills from the trainer. It was a very well-structured course. I learned very professional tools in the cyber security field through this course. The
The APT course was great. I would like to thank InfosecTrain for the valuable course with experience and skills from the trainer. It was a very well-structured course. I learned very professional tools in the cyber security field through this course. The 


 Certified & Experienced Instructors
Certified & Experienced Instructors Post Training Support
Post Training Support Customized Training
Customized Training Flexible Schedule
Flexible Schedule Access to Recorded Sessions
Access to Recorded Sessions 



 1800-843-7890 (India)
1800-843-7890 (India) 
