Exploring Module 02 of EC Council’s CEH: Footprinting and Reconnaissance
Footprinting serves as the initial phase in assessing the security status of a target organization’s IT infrastructure. Engaging in footprinting and reconnaissance activities can collect extensive information about a computer system, network, and any connected devices. Footprinting creates a detailed security profile for an organization and should be carried out systematically.

Module 01 of EC Council’s CEH : Introduction to Ethical Hacking
Module 2 of EC Council’s CEH: Footprinting and Reconnaissance introduces footprinting concepts and provides insights into the footprinting methodology.
What is Footprinting?
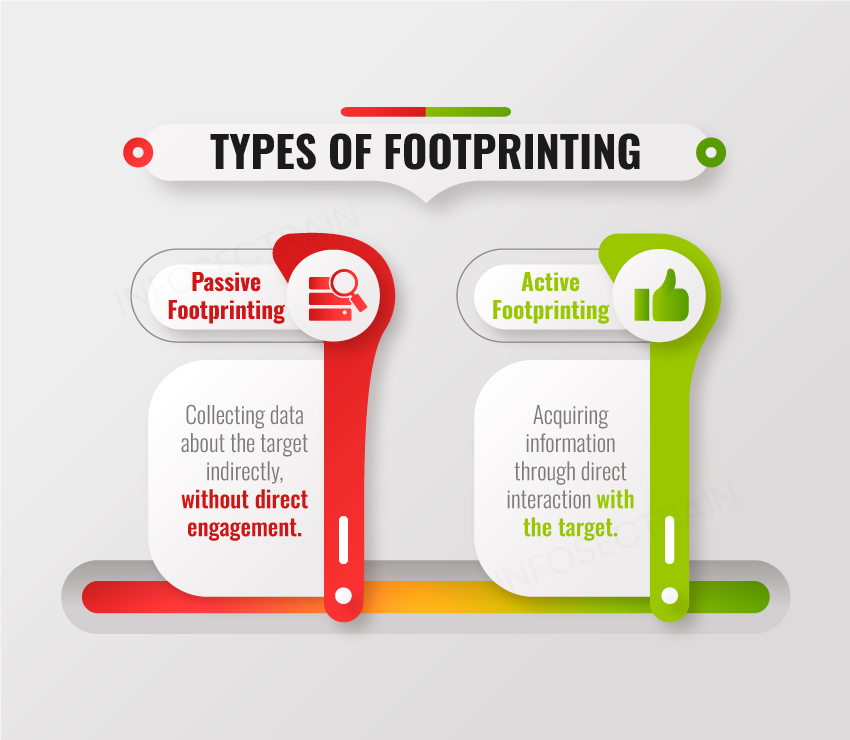
Footprinting is the first step of any attack on an information system in which attackers collect information about a target network to identify various ways to intrude into the system or network.
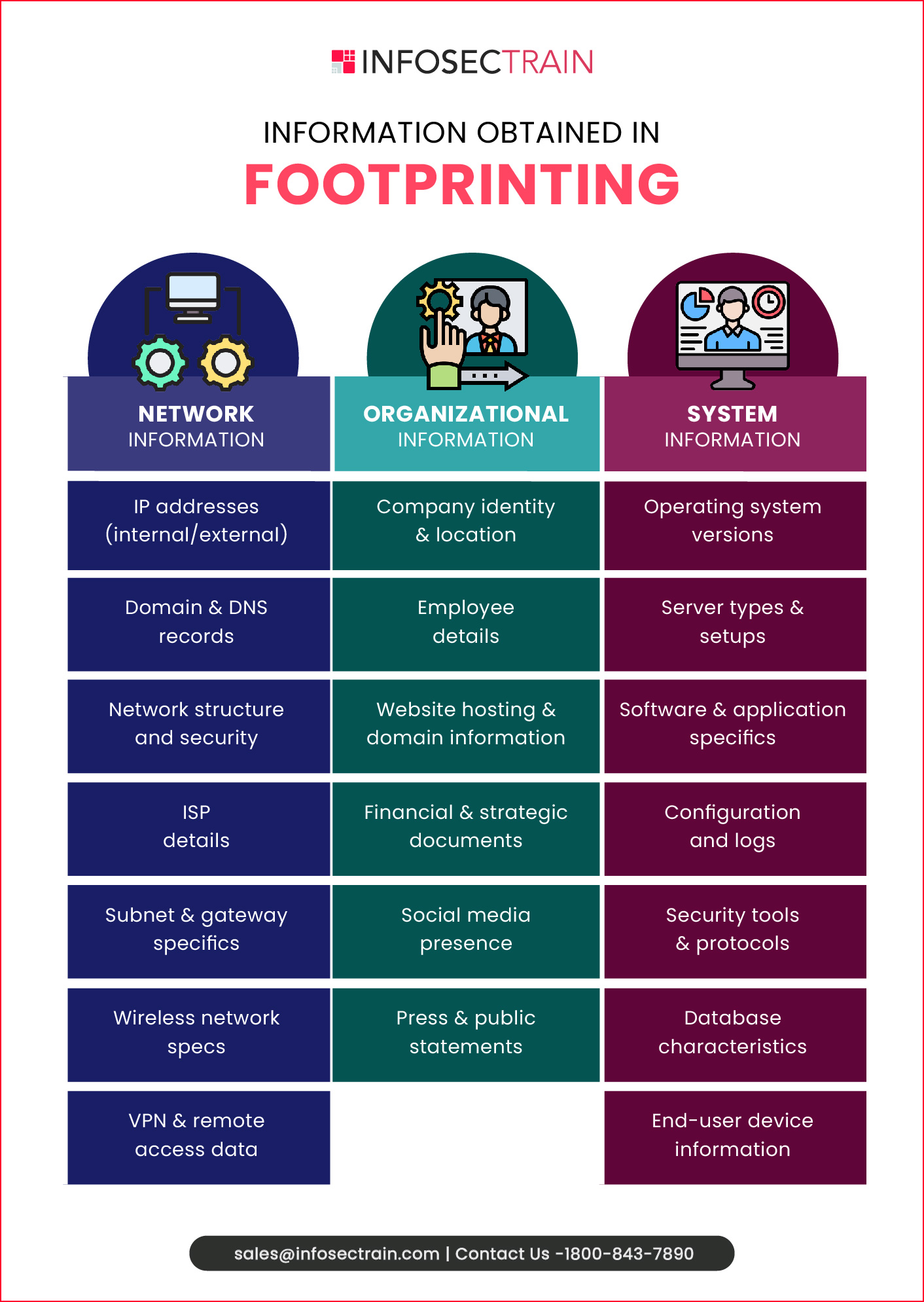
Information Obtained in Footprinting
Footprinting Methodology

Google Hacking Database
The Google Hacking Database (GHDB) is a comprehensive resource that contains a collection of advanced Google search queries, often referred to as Google Dorks. These queries are designed to find security loopholes and expose sensitive information accessible through Google searches.
Techniques for Footprinting through Search Engine
1. Advanced Search: Footprinting using advanced Google hacking techniques involves leveraging specific Google search queries to find sensitive information or security vulnerabilities within a target’s infrastructure. It’s a part of passive information gathering, as it doesn’t involve direct interaction with the target’s systems. Here’s how it’s typically done:
The syntax to use an advanced search operator is operator: search_term
Some of the popular Google advanced search operators include:
- site: Narrow the search results to a specific website or domain. site:example.com
- intitle: Finds pages with specific text in the title tag example: intitle:login page
- inurl: Locates URLs containing a specified keyword. Example: inurl:admin
- intext: Searches for pages containing certain text in their content. Example: intext:confidential
2. Advanced Image Search:
Description: Helps in finding images related to the target, including images of employees, infrastructure, or inadvertently uploaded documents.
Tools: Google Images (Advanced Search), Bing Images.
3. Reverse Image Search:
Description: Useful for identifying the source or additional occurrences of an image, aiding in locating where else a particular image is being used.
Tools: Google Images (Reverse Image Search), TinEye.
4. Meta Search Engine:
Description: Aggregates results from multiple search engines, broadening the search scope and providing a more comprehensive set of results.
Tools: Dogpile, Metacrawler.
5. Video Search Engine:
Description: Tailored for finding videos, useful for uncovering video content related to the target, like interviews and presentations.
Tools: Bing Video Search, DuckDuckGo Video Search.
6. FTP Search Engine:
Description: Aids in locating files on FTP servers, revealing downloadable data, software, or documents not indexed by standard web search engines.
Tools: Global File Search, Napalm FTP Indexer.
7. IoT Search Engine:
Description: Designed to find Internet of Things (IoT) devices, revealing information about a target’s IoT infrastructure, including potentially unsecured devices.
Tools: Shodan, Censys.
CEH with InfosecTrain
Ethical hacking is a complex and multi-phase process that requires deep knowledge and security certifications. Professionals can improve their security assessment and network architecture skills through ethical hacking courses, such as the Certified Ethical Hacker certification training provided by InfosecTrain. This training provides individuals with the essential skills and methods needed to perform sanctioned hacking into organizations.
TRAINING CALENDAR of Upcoming Batches For CEH v12
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 05-May-2024 | 22-Jun-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 02-Jun-2024 | 13-Jul-2024 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] |




 1800-843-7890 (India)
1800-843-7890 (India) 
