Exploring Module 01 of EC Council’s CEH: Introduction to Ethical Hacking
The EC-Council’s Certified Ethical Hacker (CEH) certification is a prestigious credential in the field of information security, specifically focusing on ethical hacking. This certification program aims to offer an in-depth knowledge of identifying weaknesses and vulnerabilities in IT systems, adopting the viewpoint of a malicious hacker, yet doing it legally and legitimately.

This certification program trains individuals in the advanced step-by-step methodologies that hackers use, such as writing virus codes and reverse engineering, to better protect corporate infrastructure from data breaches. Held in high regard in the IT security industry, the CEH certification encompasses various modules, each focusing on different aspects of information security.
Module 01 of EC Council’s CEH : Introduction to Ethical Hacking
Module 2 of EC Council’s CEH: Footprinting and Reconnaissance
Table of Contents
Module 1: Introduction to Ethical Hacking
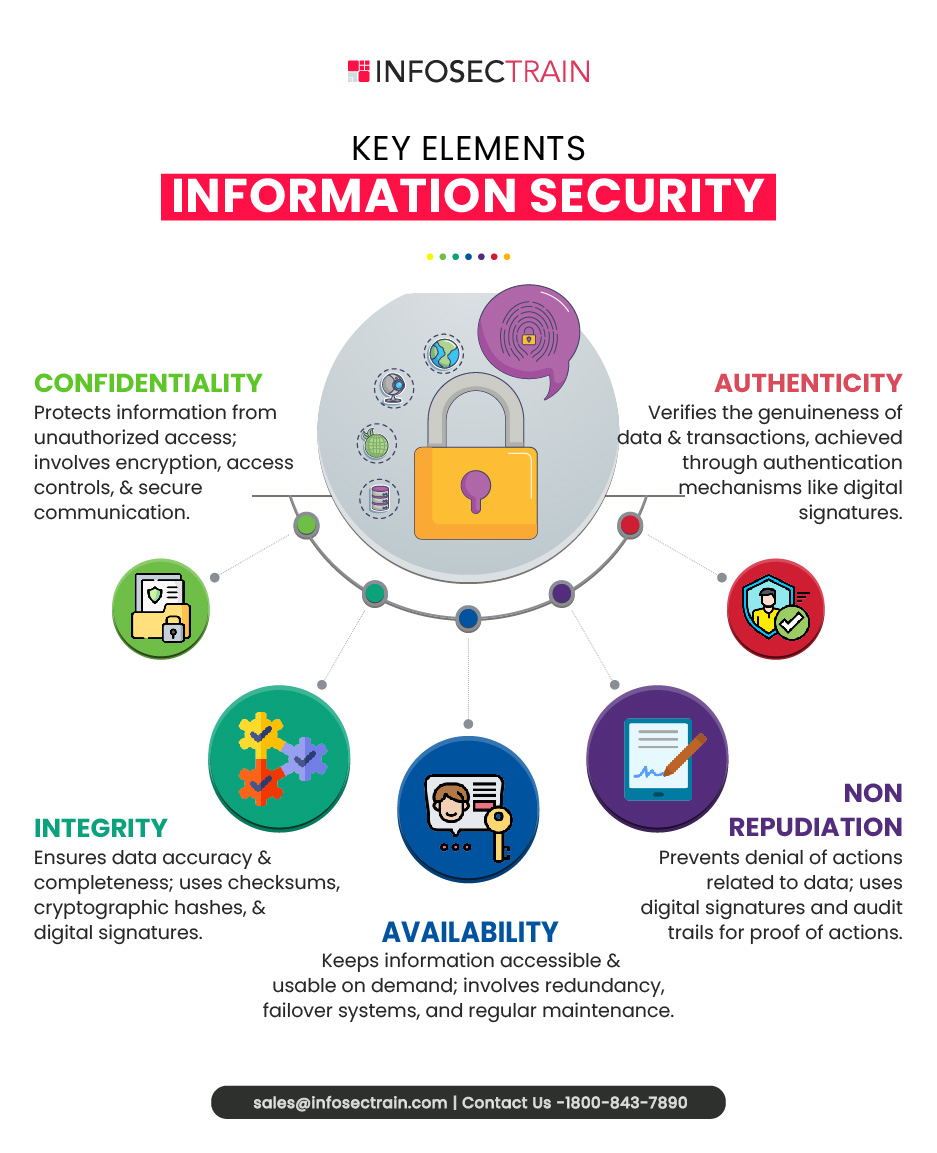
An Overview of Information Security and Its Elements
Ethical Hacking Methodologies and Frameworks
Cyber Kill Chain Methodology
MITRE ATT&CK Framework
Diamond Model of Intrusion Analysis
What is Ethical Hacking?
Who is a Hacker?
Information Assurance (IA)
Cyber Threat Intelligence
Threat Modeling
Information Laws and Standards
A pivotal part of this certification program is the first module, “Introduction to Ethical Hacking.” This article explores the key topics addressed in Module 1 of the CEH certification exam, providing insight into its importance and scope within the broader context of ethical hacking and cybersecurity.
Module 1: Introduction to Ethical Hacking
Let us start exploring the first module, “Introduction to Ethical Hacking” of the CEH certification exam by examining the contents of this module.
An Overview of Information Security and Its Elements
Ensuring the security of information is a vital responsibility for organizations. It is a broad domain within the field of cybersecurity that focuses on protecting information from unauthorized access, use, disclosure, disruption, modification, inspection, recording, or destruction. It includes a variety of practices, technologies, and procedures aimed at protecting data, whether it’s being transferred, actively used, or stored. Essential elements of information security involve:
Ethical Hacking Methodologies and Frameworks
The Certified Ethical Hacker (CEH) methodology is a structured approach to identifying and exploiting computer systems and network vulnerabilities.
- OWASP (Open Web Application Security Project): Guidelines for web application security vulnerabilities
- PTES (Penetration Testing Execution Standard): Comprehensive, multi-phase framework for penetration testing
- OSSTMM (Open Source Security Testing Methodology Manual): Peer-reviewed methodology focusing on operational security
- NIST (National Institute of Standards and Technology) Guidelines: Standards and practices for cybersecurity and penetration testing
- MITRE ATT&CK Framework: Database of real-world adversary tactics and techniques
- Cyber Kill Chain: Framework for identifying and disrupting cyber intrusions
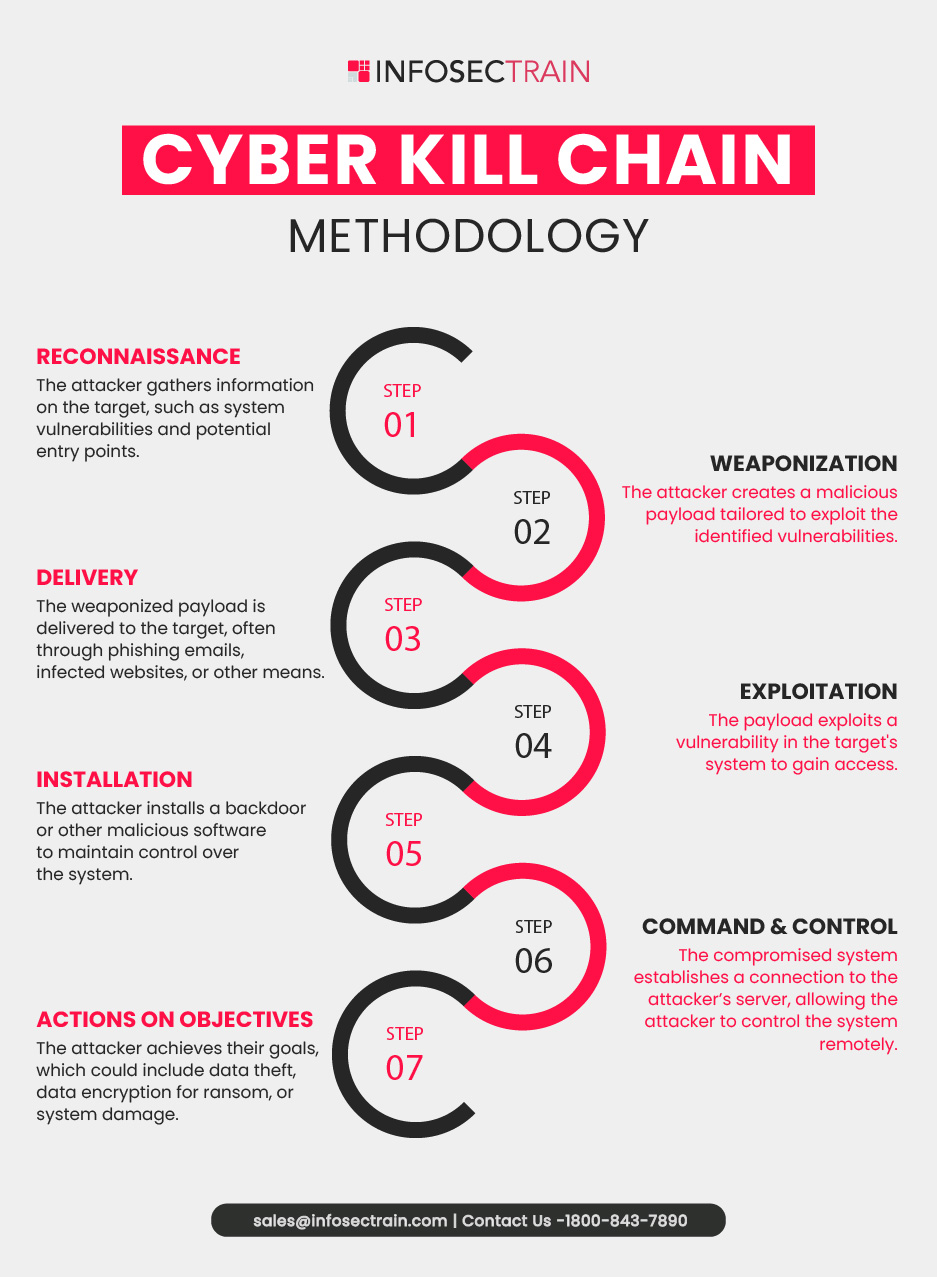
Cyber Kill Chain Methodology
The Cyber Kill Chain methodology is a concept developed by Lockheed Martin to describe the stages of a cyber attack, from the early reconnaissance stages to the final data exfiltration or system compromise. It’s used to understand and prevent cyber intrusions. The methodology breaks down an attack into distinct phases, allowing defenders to recognize and counter attacks more effectively. The cyber kill chain model is the “F2T2EA” (previous terminology) which includes the following phases:
- Find: Determine a potential target by searching through surveillance, reconnaissance, or intelligence.
- Fix: Ascertain the target’s exact location, using available information or gathering new data if necessary.
- Track: Continuously watch the target’s movements, waiting for the decision to either abandon or proceed with an engagement.
- Target: Decide on the most suitable method or instrument to achieve the desired impact on the target, considering the command’s strategic goals and available resources.
- Engage: Implement the chosen method to engage the target.
- Assess: Analyze the outcome of the engagement, considering the impact and any new intelligence collected from the site.
The stages (new terminology) are:
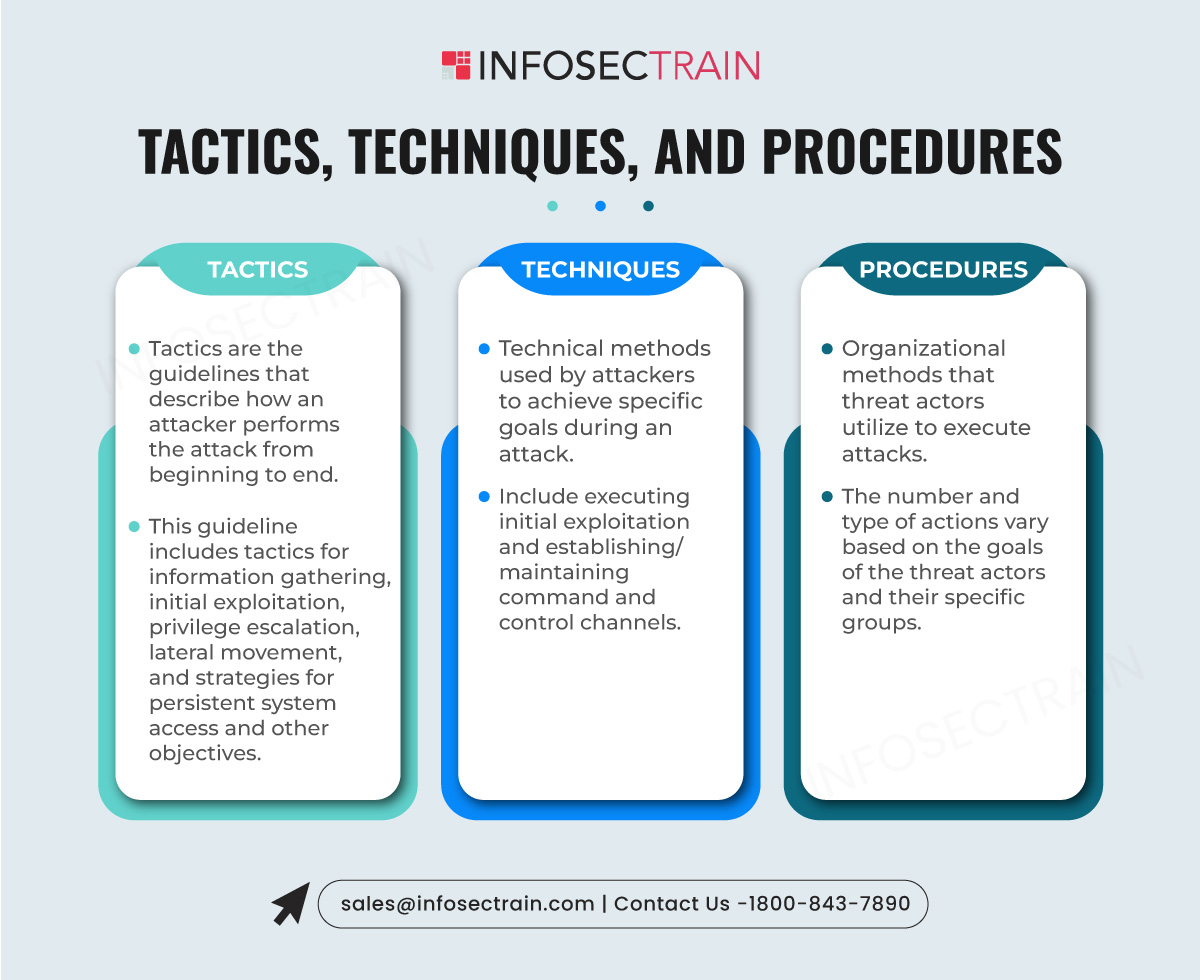
Tactics, Techniques, and Procedures
The phrase “Tactics, Techniques, and Procedures” (TTPs) describes the consistent behavior and methodologies used by specific threat actors or groups involved in cyber threats.
For example, a hacker group known for phishing might repeatedly use the same method of sending emails that appear to be from a trusted source to trick individuals into giving away sensitive information. This signature method of operating—using deceptive emails—is their known TTP.
MITRE ATT&CK Framework
The MITRE ATT&CK Framework is a comprehensive knowledge base widely used in cybersecurity to understand and analyze adversary tactics and techniques. Developed by MITRE, a not-for-profit organization, the framework provides detailed information on how adversaries operate based on real-world observations. It includes a matrix of tactics, each representing a stage in an adversary’s attack lifecycle and the techniques they use at each stage.
For example, if a cybersecurity team notices a breach, they might use the MITRE ATT&CK Framework to identify that the attackers first gained access through a phishing email (initial access tactic), then escalated their privileges (privilege escalation tactic) and finally extracted sensitive data (exfiltration tactic). Each of these steps corresponds to different techniques in the framework that describe how the attackers achieved their objectives.
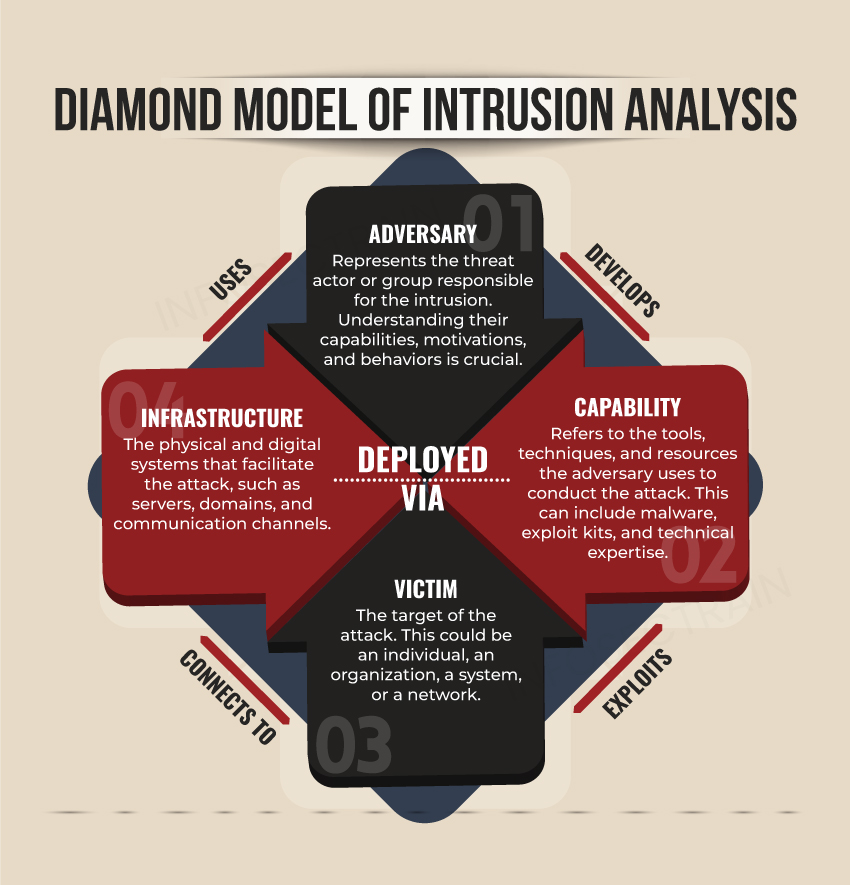
Diamond Model of Intrusion Analysis
The Diamond Model provides a structure for pinpointing groups of related events within an organization’s systems. It manages the automated aspects of any intrusion activity, known as the diamond event. It consists of four core interconnected components that form the shape of a diamond:
What is Ethical Hacking?
Ethical hacking, also known as white-hat hacking, involves employing hacking strategies to find and resolve security vulnerabilities in network systems and devices with the consent of the system owners. This form of hacking is legal and distinct from malicious hacking, as its primary goal is to enhance security.
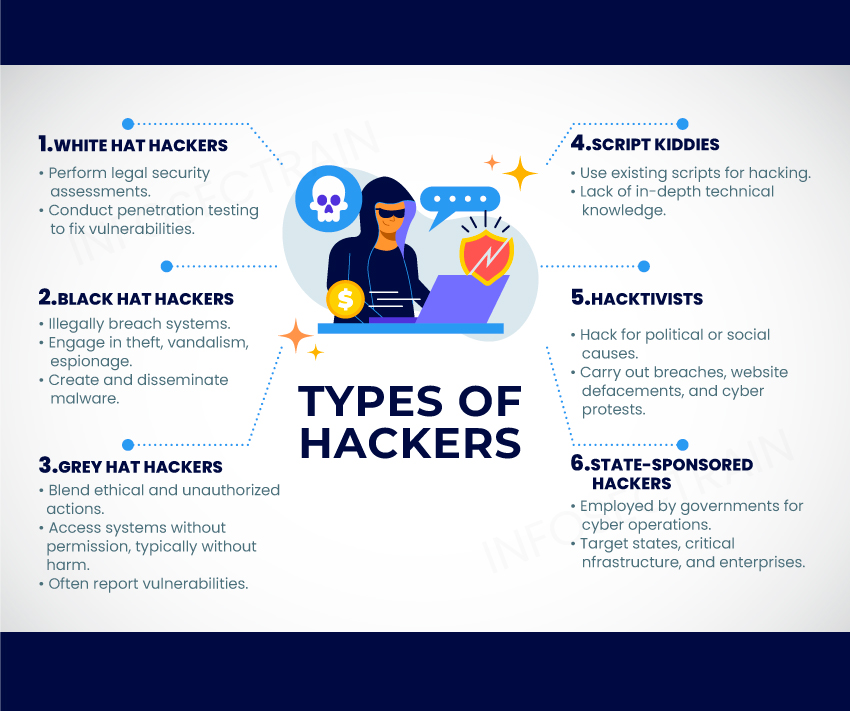
Who is a Hacker?
A hacker is an individual proficient in navigating and circumventing computer systems and networks. This term can encompass a range from a computer hobbyist to an expert programmer. However, it often denotes someone who accesses systems without authorization. Different types of hackers include:
Information Assurance (IA)
Information Assurance (IA) is the process of mitigating risks associated with handling, processing, storing, and transmitting information or data and the systems and processes utilized for these activities. Its objective is to safeguard and secure information and information systems, guaranteeing their confidentiality, integrity, and availability. It also focuses on preserving the authenticity and non-repudiation of the information.
For example, a bank implements strong encryption for data transmission, uses multi-factor authentication to protect user accounts, regularly updates and patches its systems, and maintains backup and recovery procedures. These actions ensure that customer data is confidential, unaltered, and accessible when needed, all of which are principles of Information Assurance.
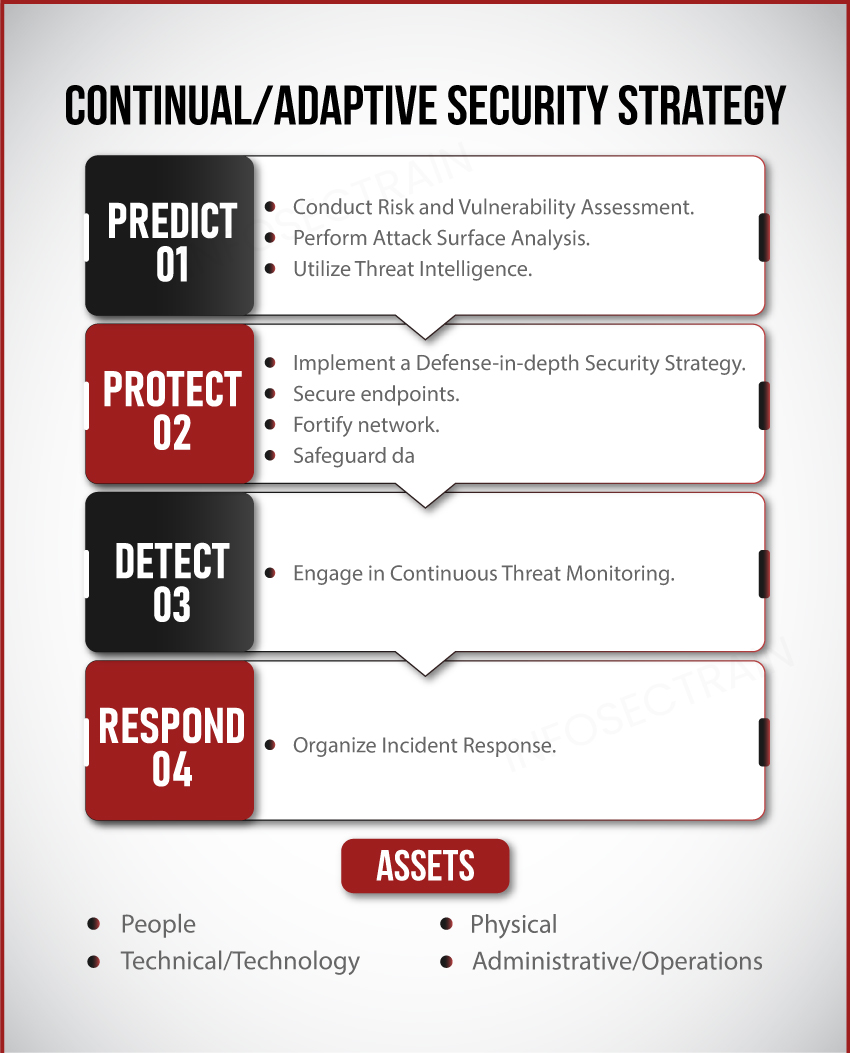
Continual/Adaptive Security Strategy
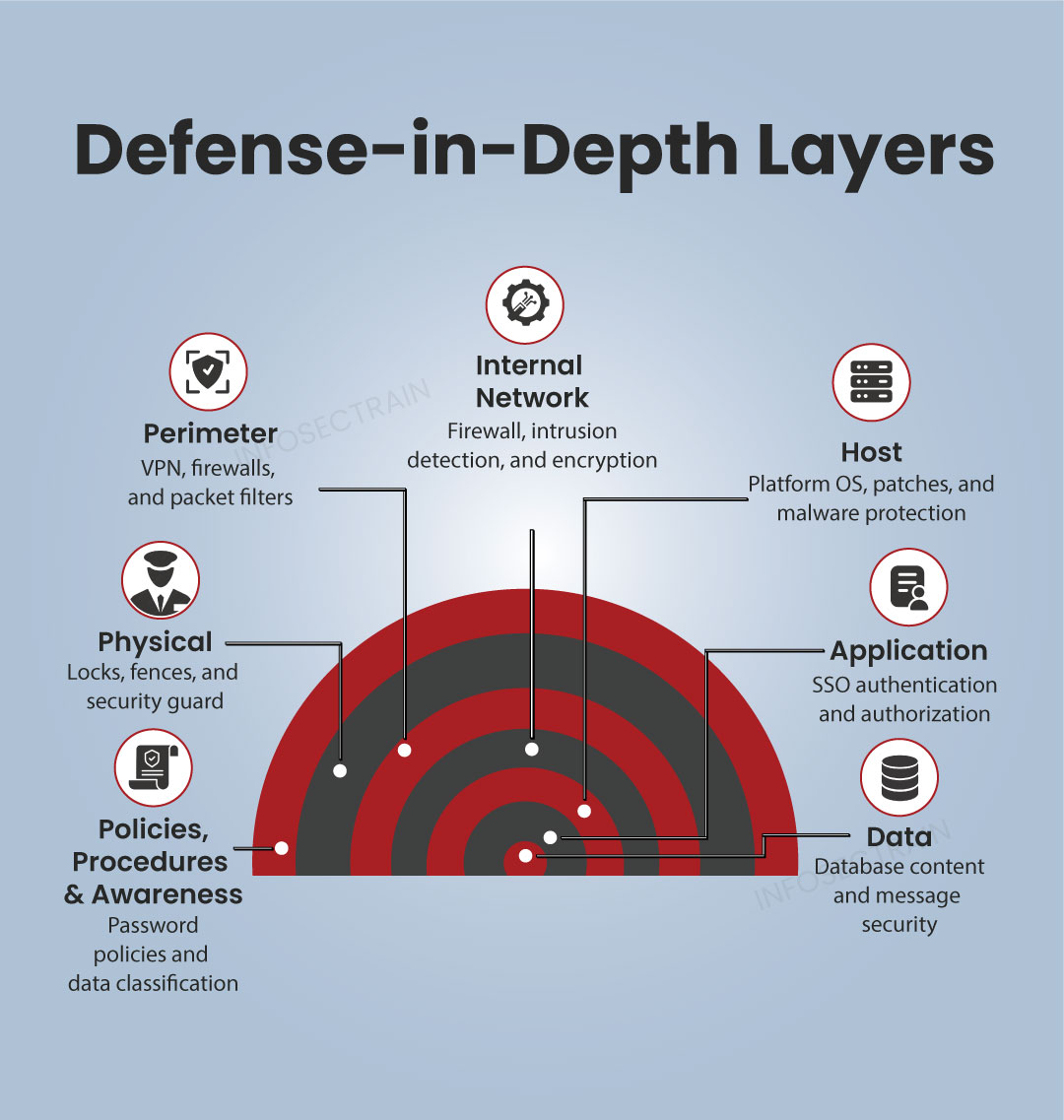
Defense-in-Depth
Risk Management
Risk management involves identifying, assessing, and prioritizing risks to an organization’s digital assets and implementing strategies to reduce these risks to an acceptable level. It’s a continuous process encompassing risk assessment, risk mitigation strategies, and ongoing risk monitoring. Risk management typically involves several key phases to effectively identify, assess, and mitigate risks. These phases are:

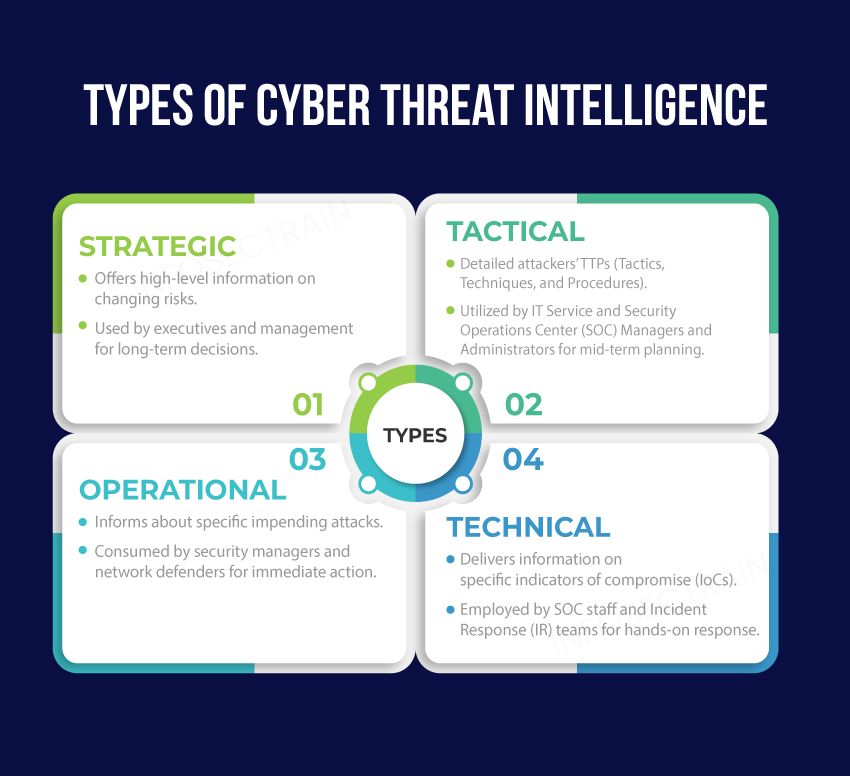
Cyber Threat Intelligence
The process of collecting and analyzing information about threats and adversaries to identify patterns, aiding in informed decision-making for preparedness, prevention, and response to cyber-attacks.
CTI assists organizations in identifying and mitigating business risks by transforming unknown threats into known threats, facilitating the development of advanced and proactive defense strategies.
Threat Modeling
Threat modeling is a systematic method to evaluate an application’s security through the comprehensive collection, organization, and analysis of information impacting application security.

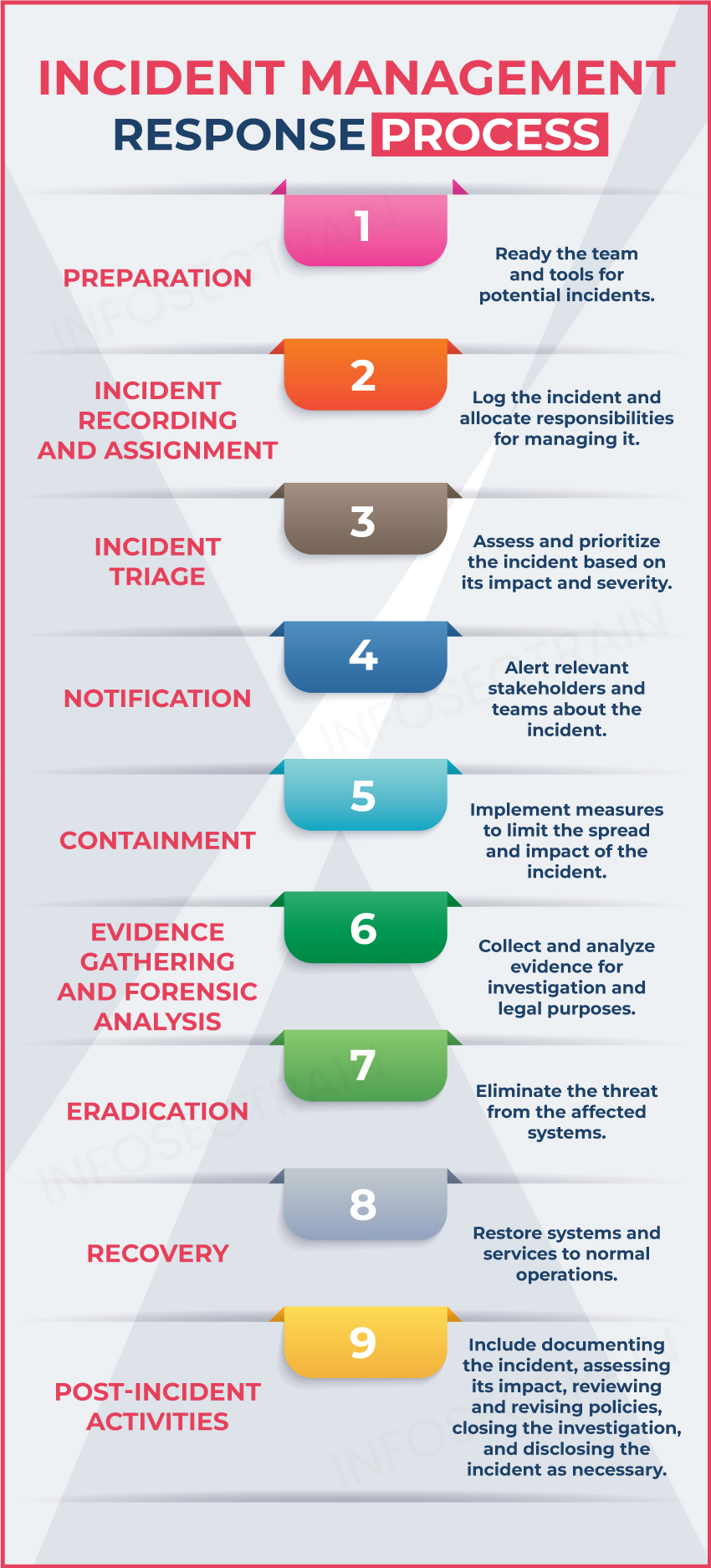
Incident Management
Incident management refers to an organization’s process to manage and resolve incidents affecting its IT services and infrastructure. An incident encompasses any occurrence that interrupts or has the potential to interrupt a service or operation, such as cyber attacks, system malfunctions, or data breaches. The key components of incident management include:
Information Laws and Standards
In information security, there are different information laws and standards that play a crucial role in governing how organizations manage and protect data:
- PCI DSS: PCI DSS is a mandatory security standard for all entities processing credit card data to protect cardholder information and reduce credit card fraud.
- HIPAA: A U.S. law ensuring the privacy and security of patients’ medical information, applicable to healthcare providers and insurers.
- SOX: U.S. legislation enforcing strict financial record keeping and transparency for public companies to prevent corporate fraud.
- GDPR: A regulation in the European Union that oversees data protection and privacy for residents of the EU, affecting international businesses that manage their data.
CEH with InfosecTrain
Ethical hacking is a complex and multi-phase process that requires deep knowledge and security certifications. Professionals can improve their security assessment and network architecture skills through ethical hacking courses, such as the Certified Ethical Hacker certification training provided by InfosecTrain. This training provides individuals with the essential skills and methods needed to perform sanctioned hacking into organizations.
TRAINING CALENDAR of Upcoming Batches For CEH v12
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 05-May-2024 | 22-Jun-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 02-Jun-2024 | 13-Jul-2024 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] |




 1800-843-7890 (India)
1800-843-7890 (India) 
