(ISC)² ® CSSLP Domain 1: Secure Software Concepts (10%)

Introduction to ISC2 CSSLP
The (ISC)² ® Certified Secure Software Lifecycle Professional (CSSLP) certification concentrates on web application security within the software development life cycle (SDLC). CSSLP Certification validates advanced application security expertise. It demonstrates to organizations and peers that you have the advanced technological skills and knowledge required for authentication, authorization, and auditing throughout the software development lifecycle (SDLC), employing best practices, policies, and procedures set by (ISC)² ® cybersecurity professionals.
The CSSLP certification demonstrates you as an application security specialist. CSSLP is a fantastic approach to expanding your security expertise, allowing you to maintain your skills. Because it is not product-specific, you can easily apply your abilities to various technologies and approaches. It teaches you how to defend your organization while safeguarding sensitive information.
Domains of (ISC)² ® CSSLP
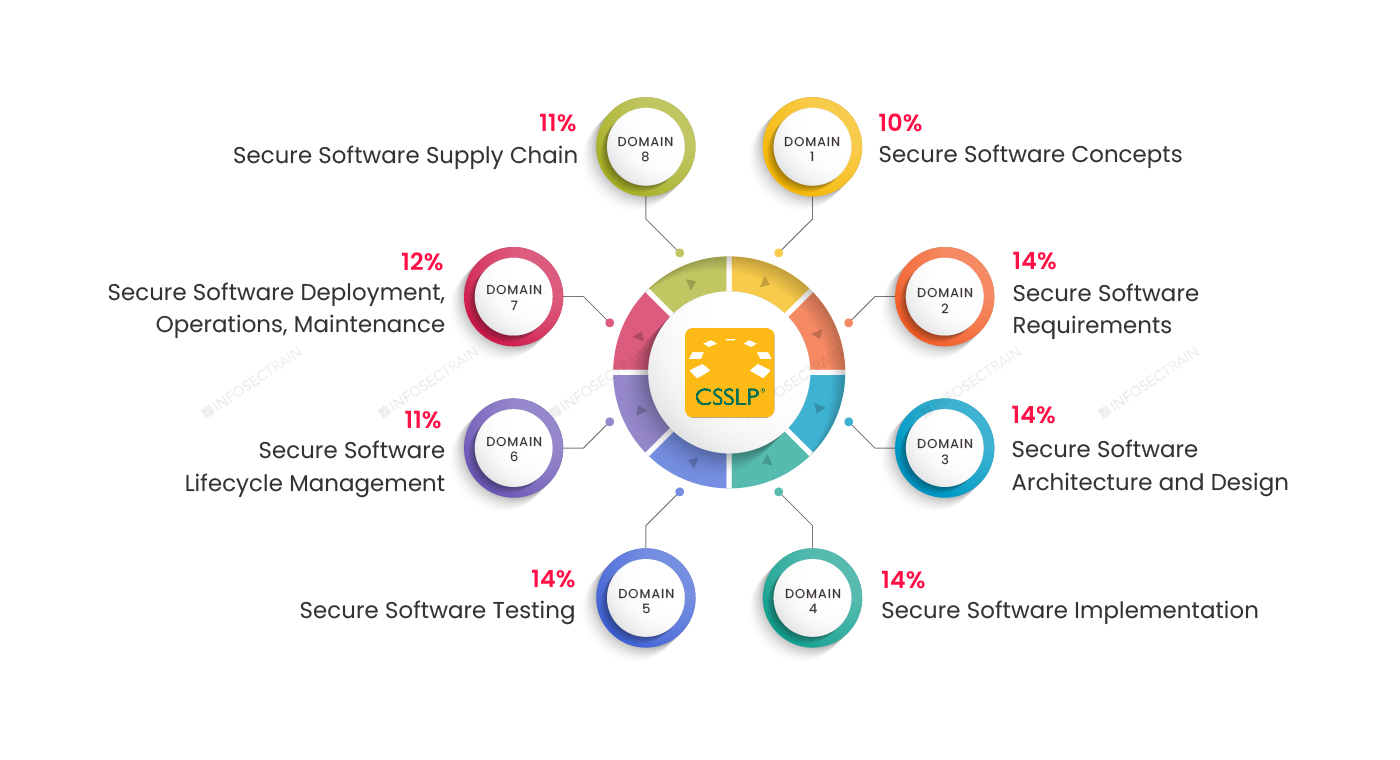
Domain 1: Secure Software Concepts (10%)
Domain 2: Secure Software Requirements (14%)
Domain 3: Secure Software Architecture and Design (14%)
Domain 4: Secure Software Implementation (14%)
Domain 5: Secure Software Testing (14%)
Domain 6: Secure Software Lifecycle Management (11%)
Domain 7: Secure Software Deployment, Operations, Maintenance (12%)
Domain 8: Secure Software Supply Chain (11%)
This article provides an overview of the (ISC)² ® CSSLP Domain 1: Secure Software Concepts (10%).
(ISC)² ® CSSLP Domain 1: Secure Software Concepts (10%)
Secure software concepts is the first domain of the CSSLP certification exam, which carries 10% of the exam weightage. You will learn about confidentiality, authentication, integrity, availability, auditing, authorization, and management concepts in this domain. This domain familiarizes candidates with fundamental concepts of risk management and governance. This domain is focused on foundational definitions and knowledge. This domain is divided into two subcategories:
- Core concepts
- Security design principles
Core Concepts
This subcategories of domain 1 focus on some of the basic concepts of cybersecurity, which includes:
1. Confidentiality
The term confidentiality refers to protecting your information by encryption or other measures.
2. Integrity
In cybersecurity, the term integrity refers to the fact that an unauthorized entity has not manipulated information.
3. Availability
Availability ensures that the service stays accessible and available to users through redundancy, replication, clustering, and other means.
4. Authentication
Authentication identifies a user through multi-factor authentication (MFA), Identity & Access Management (IAM), Single-sign On (SSO), and federated identity.
5. Authorization
Authorization determines whether an access request is authentic or not based on access controls, permissions, and entitlements.
6. Accountability
Through logging and auditing, keeping track of system activity is the term known as accountability.
7. Non-repudiation
Non-repudiation prohibits customers from denying specific activities through digital signatures, blockchain, and other technologies.
Security Design Principles
When the CSSLP domain 1 sub-topic core concepts aspect defines the “objective” of cybersecurity, the security design principles section focuses on best practices for accomplishing these objectives. This sub-topic includes:
1. Least privilege
In this section, you will learn that every process and user of the system should function with the fewest set of privileges required to complete the task. Access control, need-to-know, and run-time privilege can all be used to enforce it.
2. Separation of duties
You’ll learn in this section that no single user should be able to undertake crucial tasks on their own. Multi-party control, secret sharing, and divided knowledge would separate duties across multiple parties.
3. Defense in depth
You will understand that security should not be based on a single line of surveillance and implementation. Layered controls, input validation, and a security zone should be used to secure resources.
4. Resiliency
It is designed to secure a failed system by implementing fail-safe, fail-secure, and no Single Point of Failure (SPOF).
5. Economy of mechanism
This part will teach you how to create security measures embedded in both hardware and software, and they should be as basic and compact as feasible. In this section, you will learn how to use Single Sign-On (SSO), password vaults, and resources.
6. Complete mediation
This section will teach you how to check every access against the access mechanism control. You’ll learn about cookie management, session management, and credential caching.
7. Open design
Here you will understand that security should not depend on the design and algorithm kept secret, and it should be open rather than secret.
8. Least common mechanism
This section tells you that the design should minimize the functions shared by different users, providing mutual understanding. And this is done through white-listing and compartmentalization/isolation.
9. Psychological acceptability
Here you will learn that users’ work should not be excessively hampered by security procedures, while those who approve access should meet their demands.
10. Component reuse
Component reuse means instead of building new security libraries and controls, if possible, using existing ones. These components are more likely to be implemented correctly and to have built-in security.
11. Diversity of defense
This part will teach you that security solutions should be diversified in geography, technology, and distributed systems.
CSSLP with InfosecTrain
It’s no longer only coding when it comes to software development; and it also entails writing secure code to eliminate flaws. The CSSLP certification demonstrates that you have the advanced abilities necessary to design, develop, and execute security processes throughout the SDLC. InfoSec Train’s CSSLP course is spaced out and covers all eight domains of the CSSLP certification. So check out InfosecTrain for your preparation.




 1800-843-7890 (India)
1800-843-7890 (India) 
