(ISC)² ® CSSLP Domain 5: Secure Software Testing (14%)

Domains of (ISC)² ® CSSLP
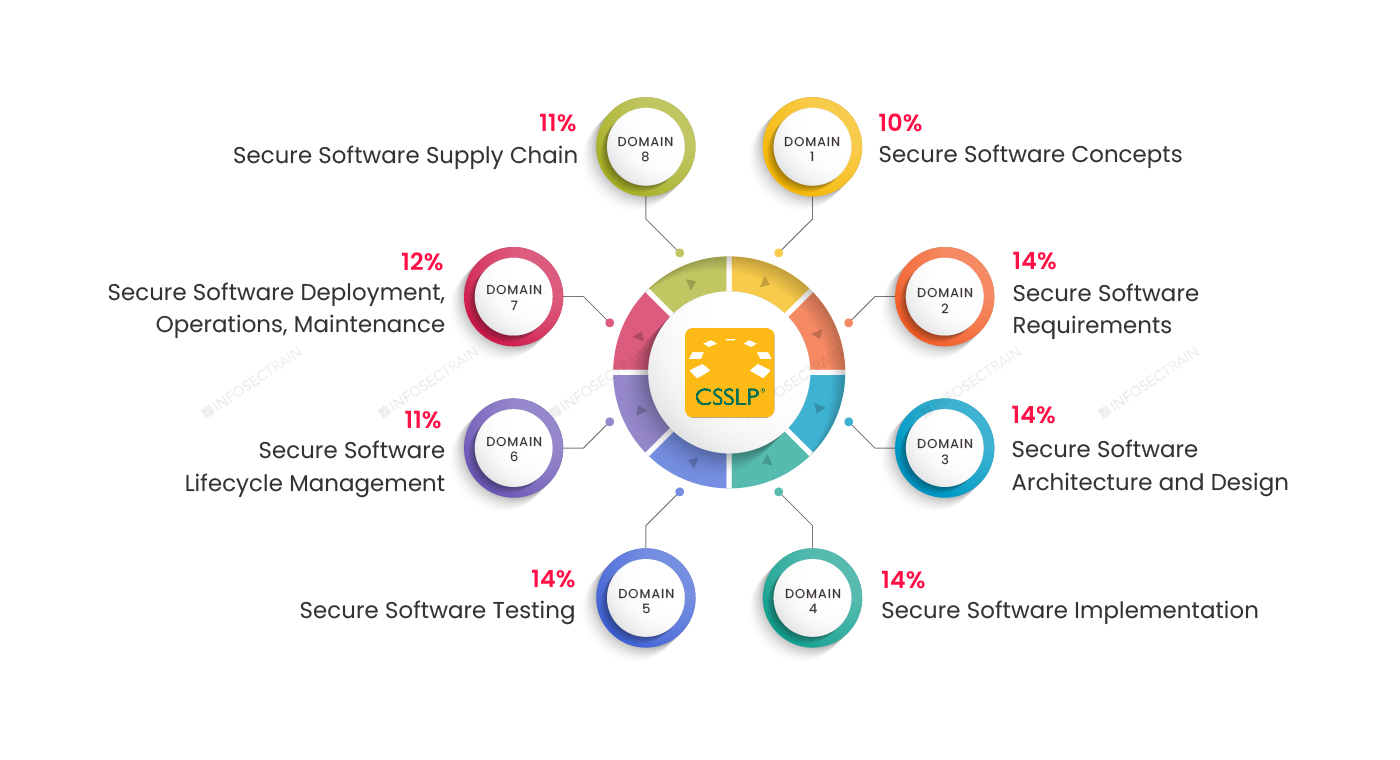
Domain 1: Secure Software Concepts (10%)
Domain 2: Secure Software Requirements (14%)
Domain 3: Secure Software Architecture and Design (14%)
Domain 4: Secure Software Implementation (14%)
Domain 5: Secure Software Testing (14%)
Domain 6: Secure Software Lifecycle Management (11%)
Domain 7: Secure Software Deployment, Operations, Maintenance (12%)
Domain 8: Secure Software Supply Chain (11%)
This article provides an overview of (ISC)² ® CSSLP Domain 5: Secure Software Testing (14%).
Domain 5: Secure Software Testing (14%)
During the software development process, vulnerabilities are discovered through software testing. This CSSLP domain accounts for 14% of the exam weightage, which comprehends how to develop security test cases, methodologies, and security testing plans. It also covers how to check and verify documentation (e.g., installation and setup instructions, problem warnings, user guides, and release notes), how to discover undocumented functionality, and how to analyze the security implications of test results (e.g., impact on product management, prioritization, and break build criteria). The candidate is required to be knowledgeable about the following topics in this domain:
- Develop security test cases
- Develop a security testing strategy and plan
- Verify and validate the documentation
- Identify undocumented functionality
- Analyze security implications of test results
- Classify and track security errors
- Secure test data
- Perform verification and validation testing
1. Develop security test cases
This CSSLP domain five subtopic delves into security test cases. The core of secure software testing is security test cases. This subtopic covers attack surface validation, penetration testing, fuzzing (e.g., generated, mutated), scanning (e.g., vulnerability, content, privacy), simulation (e.g., simulating production environment and production data, synthetic workloads), regression tests, failure, and integration tests (e.g., fault injection, stress testing, break testing), and cryptographic validation(e.g., Pseudo-Random Number Generator (PRNG), entropy).
2. Develop a security testing strategy and plan
Security test cases act as a checklist for executing secure software testing. The strategy and preparation for security testing serve as a reference for performing secure software testing. In this section, you will learn about functional security testing (e.g., logic), non-functional security testing (e.g. reliability, performance, scalability), testing techniques (e.g. white box and black box), standards (e.g. International Organization for Standardization (ISO), Open Source Security Testing Methodology Manual (OSSTMM), Software Engineering Institute (SEI)), and crowdsourcing (e.g. bug bounty).
3. Verify and validate the documentation
A documentation approach is essential in the secure software testing process, and validating documentation is vital.
4. Identify undocumented functionality
This section will teach you how to spot undocumented functionality. Sometimes, some documents may go undetected; therefore, this section will teach you how to identify those undocumented functions.
5. Analyze security implications of test results
During the software testing process, analyzing security implications is a necessary process. This section delves into how important it is to explore the security implications of test results in the testing process, for example, the impact on product management, prioritization, and break-build criteria.
6. Classify and track security errors
Finding security flaws in secure software testing is one thing, but understanding how to categorize and monitor them is essential for software testing. So this section covers bug tracking (e.g., defects, errors, and vulnerabilities) and risk scoring (e.g., Common Vulnerability Scoring System (CVSS)).
7. Secure test data
Securing the tested data in the software testing process is a necessary process. This section explains test data generation (e.g., referential integrity, statistical quality, production representative) and production data reuse (e.g., obfuscation, sanitization, anonymization, tokenization, data aggregation mitigation).
8. Perform verification and validation testing
The final process of software testing is performing verification and validation testing. In this section, you will know how to perform validation and verification testing.
CSSLP with InfosecTrain
When it comes to software development, it’s no longer just about coding; it’s about building secure code to minimize software development weaknesses. The CSSLP certification validates your advanced expertise in designing, developing, and implementing security processes throughout the SDLC. InfoSecTrain’s CSSLP course is spread out and covers all eight domains of the CSSLP certification. So, take a look at InfosecTrain.




 1800-843-7890 (India)
1800-843-7890 (India) 
