What is DarkGate Malware and Its Impact?
In the constantly changing realm of cybersecurity threats, the ominous presence of malware remains a constant source of concern in the digital world. Among the numerous malicious software strains, one name has recently caused concern among cybersecurity experts and everyday users – the mysterious “DarkGate malware.” This complex and mysterious digital threat has gained attention for its sneaky infiltration, harmful capabilities, and significant consequences on individuals, organizations, and governments.

Table of Contents
What is DarkGate Malware?
How does DarkGate Malware Operate?
Impact of DarkGate Malware
How to Protect Yourself from DarkGate Malware?
What is DarkGate Malware?
DarkGate malware is malicious software designed to infiltrate computer systems and compromise security. This strain of malware is potent and adaptable, capable of infiltrating IT systems, evading detection, and executing various cyberattacks. This malware’s name combines “Dark” and “Gate,” representing its secretive nature and the gateway it provides for cybercriminals to exploit. It is a Remote Access Trojan (RAT) with infostealer functionality that can give attackers control over compromised systems and extract valuable information. DarkGate has been involved in various malicious activities, such as data exfiltration, credential phishing, and ransomware deployment.
How does DarkGate Malware Operate?
DarkGate uses several tactics to compromise systems and achieve its nefarious goals:
- Phishing Attacks: DarkGate often spreads through phishing emails or malicious attachments, tricking users into downloading and executing the malware.
- Exploiting Vulnerabilities: DarkGate can exploit unpatched software vulnerabilities to infiltrate systems.
- Command and Control (C&C) Servers: Once installed on a victim’s system, DarkGate establishes a connection with a C&C server. This connection enables cybercriminals to control and manage the infected devices remotely.
Impact of DarkGate Malware
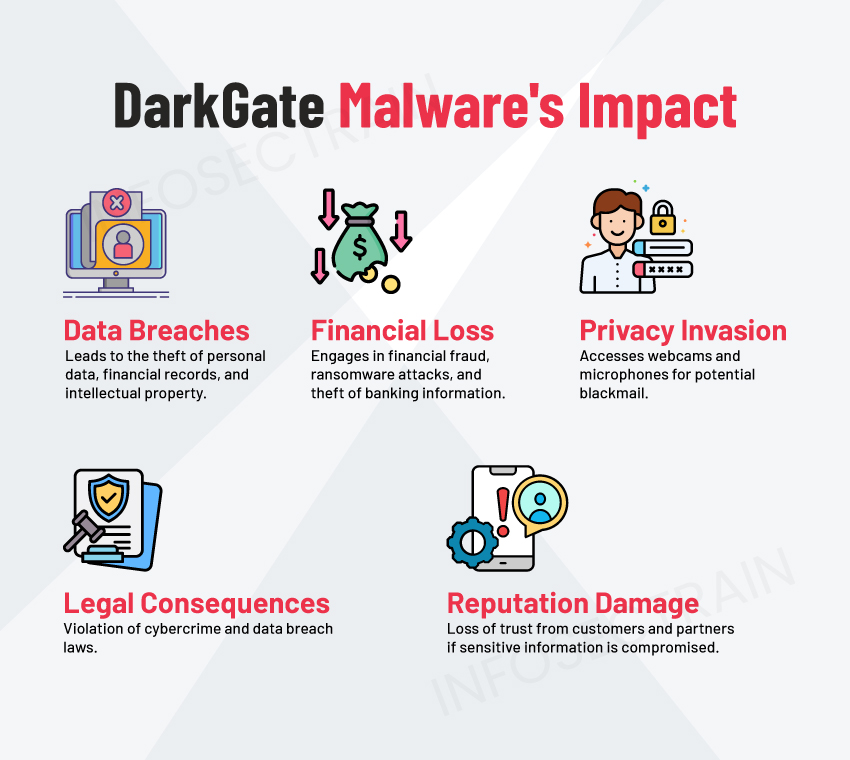
The impact of DarkGate malware can be devastating for individuals and organizations. Some of the significant consequences include:
- Data Breaches: DarkGate can lead to the theft of valuable information, including personal data, financial records, and intellectual property. This information can be exploited for financial benefit or traded on the dark web.
- Financial Loss: DarkGate allows cybercriminals to engage in various illegal activities, such as financial fraud, ransomware attacks, and theft of banking and payment information. These actions can result in substantial financial losses for both individuals and organizations.
- Privacy Invasion: DarkGate can invade personal privacy by accessing webcams and microphones, leading to potential blackmail or other privacy-related violations.
- Legal Consequences: DarkGate attacks can lead to legal repercussions, such as criminal charges and fines, as they violate laws related to cybercrimes and data breaches.
- Reputation Damage: The consequences of a DarkGate attack can tarnish the reputation of an individual or organization. Customers and partners may lose trust if their sensitive information is compromised.
How to Protect Yourself from DarkGate Malware?
Although DarkGate malware poses a significant threat, there are several measures you can take to safeguard yourself from becoming a target:
- Keep Software Updated: Regularly update operating systems, software, and security applications to patch vulnerabilities that malware can exploit.
- Exercise Caution: Be cautious when opening email attachments or downloading files from sources that are not trustworthy. Avoid clicking on any suspicious links.
- Use Antivirus Software: Install reputable antivirus software that detects and mitigates malicious software like DarkGate.
- Enable a Firewall: Configure a firewall to prevent incoming and outgoing malicious traffic.
- Practice Safe Browsing: Avoid browsing suspicious websites and consider utilizing Virtual Private Network (VPN) to enhance security.
- User Education: Educate employees and individuals about cybersecurity best practices, such as maintaining password hygiene, phishing awareness, secure browsing habits, data backup, etc.
How can InfosecTrain Help?
At InfosecTrain, we offer a Certified Ethical Hacker (CEH) training program designed to empower individuals with an advanced understanding of crucial security principles. This comprehensive course encompasses ethical hacking fundamentals, a thorough exploration of information security, security protocols, and much more. Throughout this training, participants will gain insights into the intricacies of malware and various emerging cyber security threats and attack vectors. Our training program ensures that participants receive the industry’s most comprehensive, hands-on lab experience, ensuring that participants develop practical knowledge and skills in cybersecurity.
TRAINING CALENDAR of Upcoming Batches For CEH v12
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 05-May-2024 | 22-Jun-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 02-Jun-2024 | 13-Jul-2024 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] |




 1800-843-7890 (India)
1800-843-7890 (India) 
