Data Security Challenges in the Cloud Environment
In today’s tech-driven world, companies are more and more dependent on cloud computing for storing, processing, and managing their data. The cloud offers huge benefits, including scalability, cost-effectiveness, and flexibility. However, this shift towards the cloud environment also brings significant data security challenges that must be carefully addressed. Data breaches, unauthorized access, and data loss incidents have become alarming concerns, highlighting the importance of implementing robust security measures within cloud environments.

Table of Contents
What is Cloud Computing?
What is Cloud Security and its Components?
Top Data Security Challenges in Cloud Computing
How to Improve Security in Cloud Computing?
This article explores the essential data security challenges organizations face in the cloud. By understanding these challenges, organizations can better safeguard their sensitive information and make informed decisions when adopting cloud solutions.
What is Cloud Computing?
Cloud security involves the techniques and practices used to protect data, applications, and infrastructure within a cloud computing environment. It involves implementing various security controls and technologies to safeguard information from unauthorized access, data breaches, and other security threats.
What is Cloud Security and its Components?
Cloud security pertains to the protocols and strategies established to secure data, applications, and the infrastructure operating in a cloud computing context. It involves implementing various security controls and technologies to safeguard information from unauthorized access, data breaches, and other security threats.
Utilizing physical, technical, and administrative controls, cloud security safeguards data at repose, in transit, and in use. Here are some critical components of cloud security:
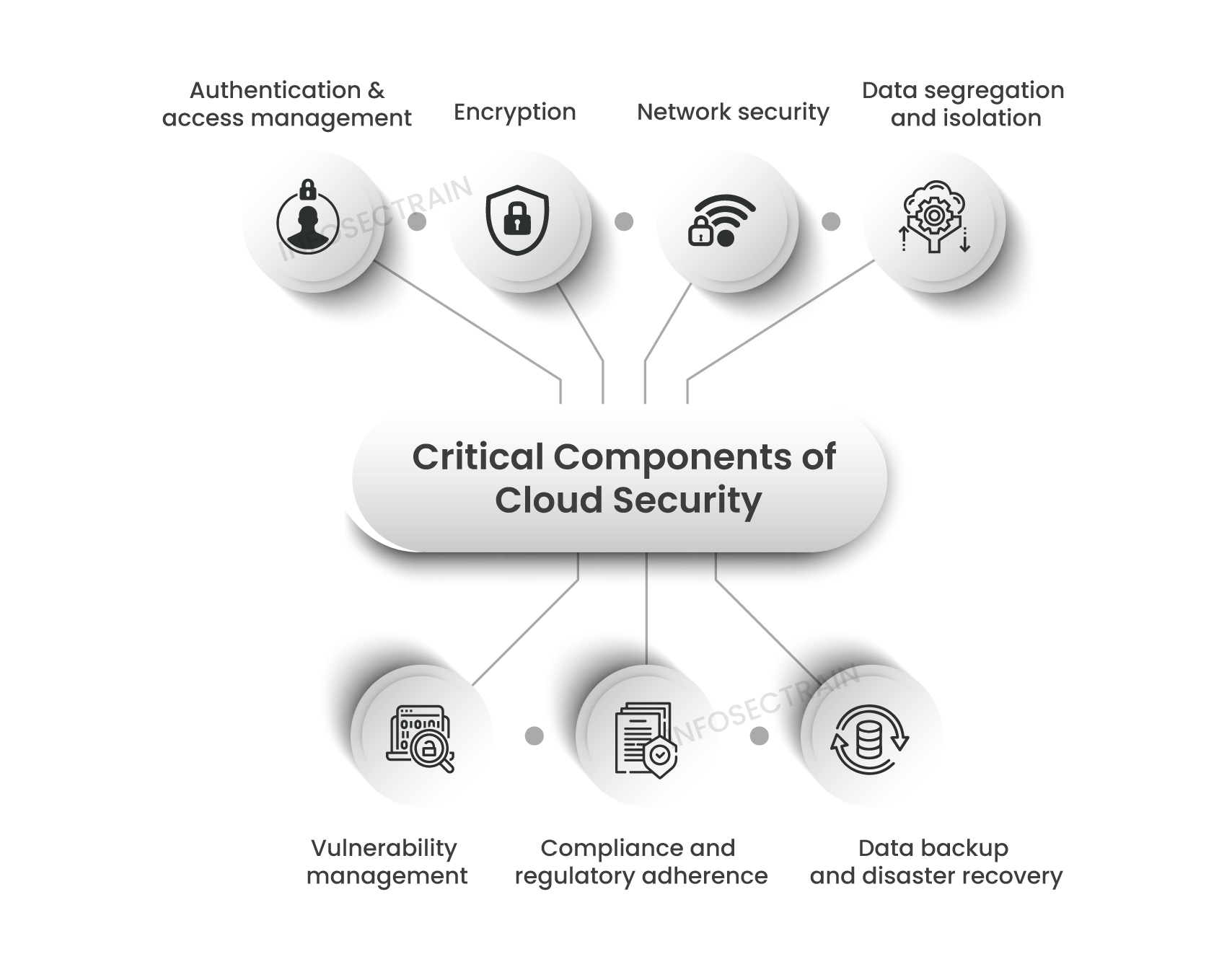
Top Data Security Challenges in Cloud Computing
Cloud computing offers numerous advantages, but it comes with several data security challenges that organizations must address. Here are some of the top data security challenges in cloud computing:

- Data breaches : Data breaches remain a significant concern in the cloud environment. Attackers may exploit vulnerabilities in cloud infrastructure, applications, or user accounts to gain unauthorized access to sensitive data. Weak access controls, insecure APIs, and misconfigurations can all contribute to data breaches.
- Insufficient access controls : Ensuring proper access controls is crucial in cloud computing. Misconfigured permissions or inadequate user authentication mechanisms can result in unauthorized users accessing sensitive data. Organizations must carefully manage user access privileges and implement robust authentication mechanisms to mitigate this risk.
- Insecure APIs : Cloud services utilize Application Programming Interfaces (APIs) for facilitating communication and interaction among various components. However, if APIs are not adequately secured, they become a potential entry point for attackers. Weak authentication, inadequate encryption, or poor validation of API requests can lead to data exposure and unauthorized access.
- Data loss and recovery: While cloud providers typically have robust backup and disaster recovery mechanisms, organizations must still consider the possibility of data loss. Accidental deletion, storage failures, or malicious actions can result in data loss. Organizations must have backup strategies and regularly test their data recovery processes.
- Shared infrastructure vulnerabilities: In a cloud environment, multiple organizations share the same underlying infrastructure. If a vulnerability or misconfiguration in the infrastructure is exploited, it can impact the security of various tenants. It is crucial to adequately isolate and separate resources to block unauthorized access and avoid data breaches among users sharing the same environment.
- Compliance and regulatory challenges: Cloud computing often involves storing and processing data subject to industry-specific regulations and compliance requirements. Adhering to regulations like GDPR or HIPAA within a cloud setting can present complexities. Organizations must carefully assess the cloud provider’s compliance measures and implement additional controls to meet regulatory obligations.
- Data privacy and confidentiality : Safeguarding the privacy and secrecy of data that is stored and handled in the cloud represents a major challenge. Organizations must ensure that appropriate encryption mechanisms are in place at rest and in transit. They should also have clear policies and procedures for data handling and sharing practices.
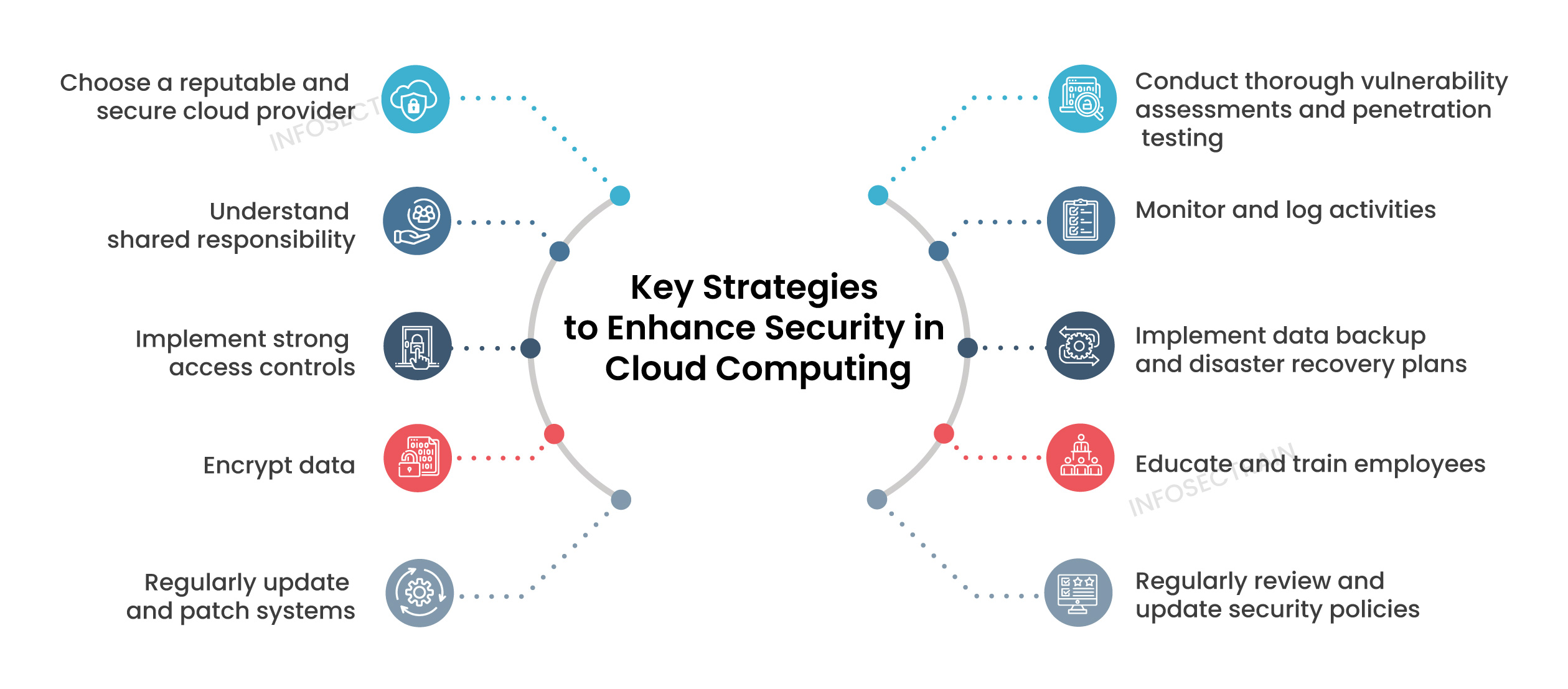
How to Improve Security in Cloud Computing?
Here are some key strategies to enhance security in cloud computing:
Cloud Security With InfosecTrain
Cloud security is crucial for any digital infrastructure, both present and future. It is necessary to take appropriate precautions to safeguard organizations from malicious individuals or groups while reaping the benefits of cloud technology. Before adopting new technologies, it’s crucial to establish adequate security protocols. This approach enables organizations to efficiently safeguard their assets and themselves.
InfosecTrain provides advanced cloud security, cybersecurity, and data security solutions to help organizations achieve enhanced protection and effective risk management. We understand that ensuring the security and smooth functioning of the cloud environment requires utilizing the latest technology and leveraging expert knowledge. Thus, achieving excellence in cloud security is not just about adopting the latest technologies or having expert knowledge; it’s about continuously evolving and adapting to secure and optimize cloud environments effectively.



 1800-843-7890 (India)
1800-843-7890 (India) 
