Cloud Storage Best Practices
Cloud storage security has grown to evaluate and deploy as it becomes more popular among businesses. It is making a collection of best practices for protecting data. This is because cloud storage revolves around data access from anywhere, at any time, and includes a diverse mix of users, apps, and data sources. Hackers can access individual accounts even if the cloud provider’s system is not compromised.
Table of Contents
What is cloud storage?
How does cloud storage work?
Types of Cloud Storage
Best Practices for Cloud Storage

What is cloud storage?
Cloud storage is a notion in cloud computing in which data is kept on a digital platform by a cloud provider who maintains and manages data storage as a service. It is available on demand, with just-in-time capabilities and pricing, and it minimizes the need for customers to buy and maintain their own data storage architecture. You receive agility, global scale, durability, and data access “anytime, anywhere.”
How does cloud storage work?
A third-party cloud provider provides cloud storage, which is owned and operated by them and accessed over the Internet using a pay-as-you-go pricing model. The storage, privacy, and resilience of your data are managed by these cloud storage providers, making it available to business apps everywhere. Applications can use an Application Programming Interface (API) to access cloud storage or conventional storage protocols. Many providers offer complementary services to collect, store, protect, and analyze data at scale.
Types of Cloud Storage
Cloud data storage is classified into object storage, file storage, and block storage. Each has its own set of benefits and applications:
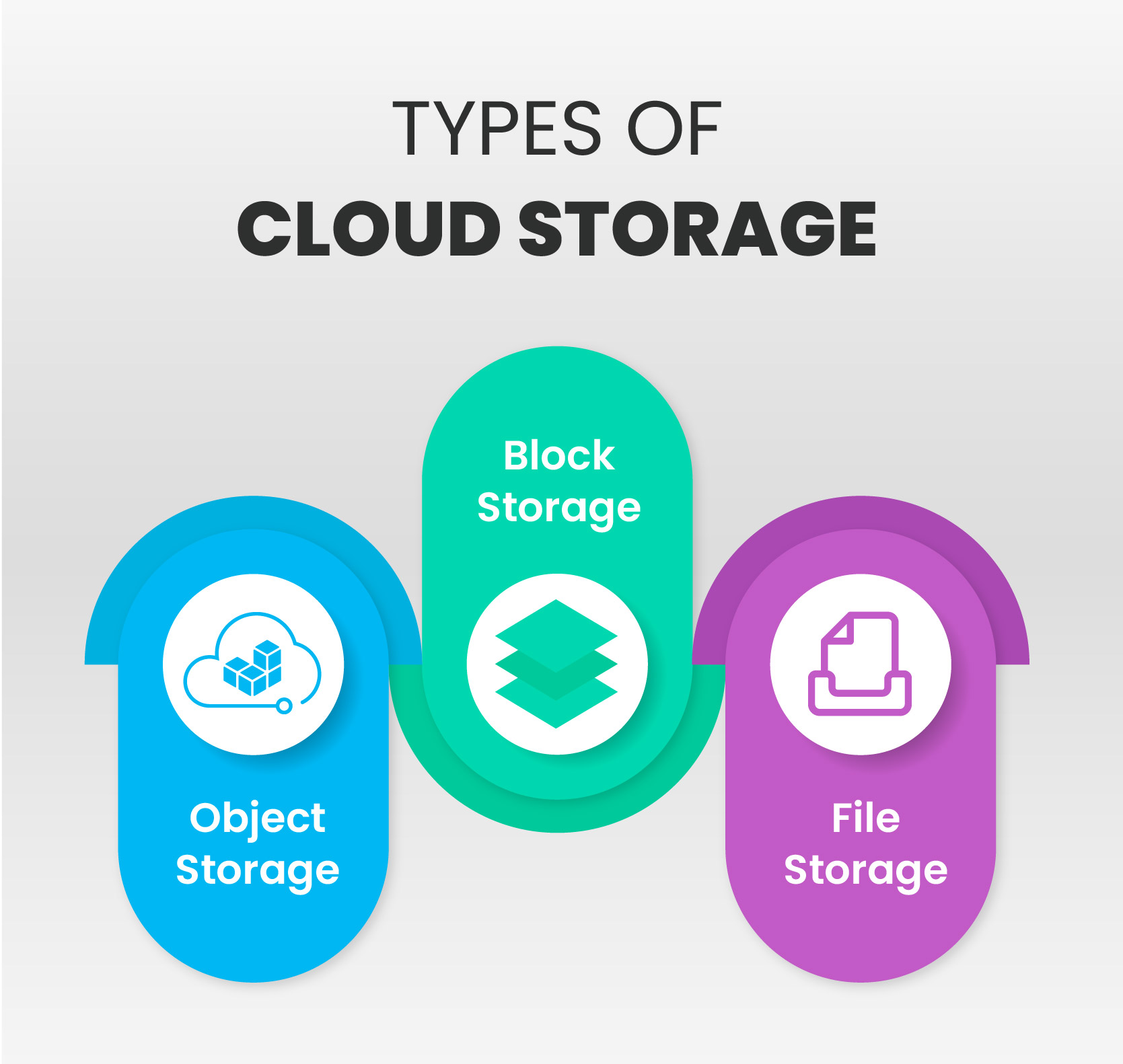
- Object storage: The enormous scalability and metadata features of object storage are extensively employed by applications created in the cloud. Object storage options like Amazon Simple Storage Service (S3) are excellent for developing scale-and-flexibility-required modern applications from the ground up. They can also be used to integrate pre-existing data stores for analysis, backup, or archiving purposes.
- File storage: Some platforms support a file system to access shared files. Network Attached Storage (NAS) servers frequently support this kind of storage. Huge data stores, runtime environments, media stores, and user home files are examples of use cases that benefit significantly from file storage solutions like Amazon Elastic File System (EFS).
- Block storage: Many organization programs, like databases or Enterprise Resource Planning (ERP) systems, frequently necessitate dedicated, low-latency storage for each host. This corresponds to Direct-Attached Storage (DAS) or a Storage Area Network (SAN). Block-based cloud storage systems, such as Amazon Elastic Block Store (EBS), are included with each cloud platform and provide the ultra-low latency needed for high-performance applications.
Best Practices for Cloud Storage
Developing a cloud storage framework and cloud storage security standards is an important practice. Here are six best practices for cloud storage:
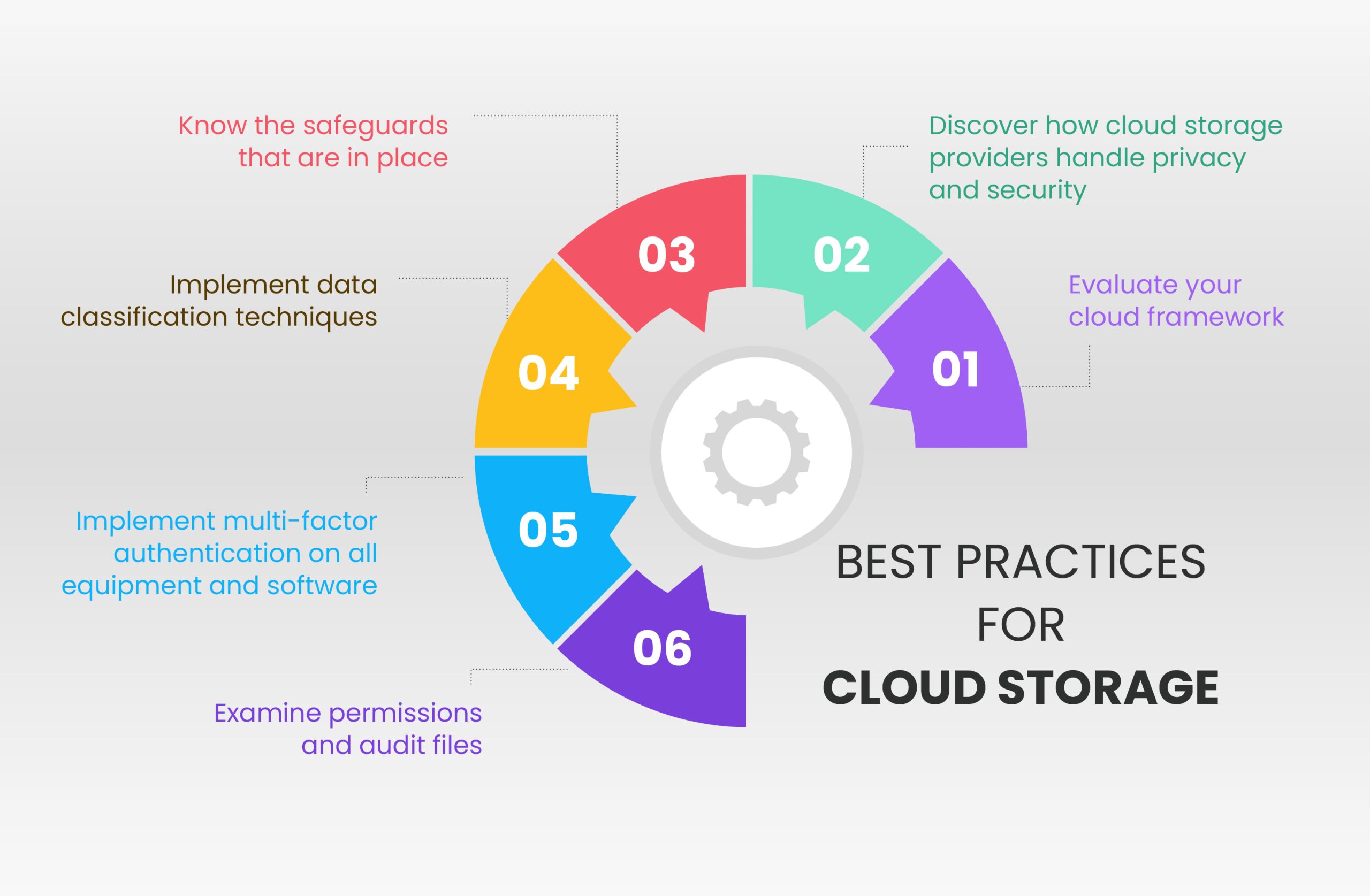
1. Evaluate your cloud framework
An organization must define all devices and programs that connect to the cloud to provide secure cloud storage. It’s also important to understand what cloud storage systems are available within an organization, who utilizes them, and how they’re used.
An organization can ensure high-security cloud storage by mapping the data flow between systems, devices, apps, APIs, and the cloud. Fortunately, many cloud storage programs show additional programs and services they link to. This may make mapping much more accessible and, if necessary, make it simpler to disconnect from other apps or services.
2. Discover how cloud storage providers handle privacy and security
Terms of service agreements are an excellent place to start when determining the general safeguards provided by a cloud provider. However, this is insufficient to ensure secure file storage. Cloud companies often update terms of service and user agreements. As a result, make sure to review the SLAs properly and ensure it is updated as per the business requirements.
3. Know the safeguards that are in place
Encryption for cloud security is a basic necessity. It’s crucial to understand how a cloud storage provider employs encryption, particularly how it’s used when data is transferred between servers, data centers, and storage devices. You should also know who controls the encryption keys and how they are used with particular data sets.
For example, an organization that uses a cloud provider should know who has access to its systems and what measures are in place to prevent everything from distributed denial-of-service (DDoS) cyberattacks to application security vulnerabilities.
4. Implement data classification techniques
Not all data is created equally. Security problems within and outside cloud infrastructure result from treating it similarly. Additionally, as organizations acquire enormous volumes of unstructured data, data protection is becoming more complicated.
It is critical to comprehend the value of data, whether it should be stored in the cloud or saved on media such as optical disk, and how data location correlates to the corporate appetite for risk.
5. Implement multi-factor authentication on all equipment and software
Multi-factor authentication can help to limit the possibility of someone gaining unauthorized access to systems or applications and exploiting it to spread malware or gain access to other data. While the risk is higher for root privileges, it is not eliminated for regular apps and tools. Multi-factor authentication can help safeguard sensitive data from hackers, individual employees, and other insiders who may purposefully or unintentionally compromise data.
6. Examine permissions and audit files
Cloud storage services give both private and public file sharing options. Anyone with the proper URL can access the files. Reviewing the permission settings to determine who has access to edit and download files is critical. You should do frequent audits on your files to see who is viewing them. Delete a file from the cloud when it is no longer needed. This will prevent unauthorized access and will free up extra storage space.
Cloud with Infosectrain
It is critical to understand the potential value of your cloud investment. A storage server, or any similar innovation, should include a thorough assessment of what it means for end users. Organizations that transport cloud-enabled data networks should be offered assurance that their organization can operate as usual if a server collapses, a security breach occurs, or there are issues with common human error.
If you are interested in learning more about Cloud Computing, visit InfosecTrain.



 1800-843-7890 (India)
1800-843-7890 (India) 
