CISA DOMAIN 5 – PROTECTION OF INFORMATION ASSETS
This article covers –
- Overall understanding of the domain
- Important concepts to focus on from exam point of view
The article is split into 16 parts as below:
- Part 1 – Information Security Management Systems (ISMS) – Its importance and key elements
- Part 2 – The Classification of Information assets, Various fraud risk factors, Information security control design
- Part 3 – System Access Permission, Mandatory Access Controls (MACs), and Discretionary Access Controls (DACs) and other types of Access controls.
- Part 4 – Difference between privacy and Confidentiality, privacy principles and the role of IS auditors, the privacy-related compliance requirements
- Part 5 – Critical Success Factors (CSFs) to Information Security Management, the different mechanisms available for raising information security awareness, the various Human Resources security.
- Part 6 – The various Computer crime issues and exposures, the perpetrators in computer crimes, the common attack methods, and techniques
- Part 7 – The various phases of incident response, the logical access exposures, Identification, and Authentication (I&A).
- Part 8 – The common I&A vulnerabilities, the categorization of Authentication, the various authentication techniques.
- Part 9 – Biometric access controls, Operation of each biometric access control, the various biometric devices/ techniques.
- Part 10 – The quantitative measures to determine the performance of biometric control devices, Single sign-on – its advantages and disadvantages, Firewall security systems.
- Part 11 – The general features of the firewall, the types of firewalls, the Packet filter firewall – its advantages and disadvantages.
- Part 12 – Application firewall systems – its advantages and disadvantages, a Stateful inspection firewall – its advantages and disadvantages, the various firewall implementations that are commonly used.
- Part 13 – Intrusion Detection Systems (IDS) – its types, its components, and its features
- Part 14 – The limitations of Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), Honeypots and its types
- Part 15 – Honeynets, Cryptography, Encryption, and decryption
- Part 16 – Digital signature, the various environmental issues and exposures in Information security, the controls for environmental exposures, the various physical exposure issues and exposures in Information security, the controls for Physical access exposures
PART 1 – CISA Domain 5 – Protection of Information assets
|
Overall understanding of the domain:
Weightage – This domain constitutes 25 percent of the CISA exam (approximately 38 questions)
Covers 26 Knowledge statements covering the process of auditing information systems
- Knowledge of generally accepted practices and applicable external requirements (e.g., laws, regulations) related to the protection of information assets
- Knowledge of privacy principles
- Knowledge of the techniques for the design, implementation, maintenance, monitoring, and reporting of security controls
- Knowledge of physical and environmental controls and supporting practices related to the protection of information assets
- Knowledge of physical access controls for the Identification, Authentication, and restriction of users to authorized facilities and hardware
- Knowledge of logical access controls for the Identification, Authentication, and restriction of users to authorized functions and data
- Knowledge of the security controls related to hardware, system software (e.g., applications, operating systems) and database management systems.
- Knowledge of risk and controls associated with the virtualization of systems
- Knowledge of risk and controls associated with the use of mobile and wireless devices, including personally owned devices (bring your own device [BYOD])
- Knowledge of voice communications security (e.g., PBX, Voice-over Internet Protocol [VoIP])
- Knowledge of network and Internet security devices, protocols and techniques
- Knowledge of the configuration, implementation, Operation, and maintenance of network security controls
- Knowledge of encryption-related techniques and their uses
- Knowledge of public key infrastructure (PKI) components and digital signature techniques
- Knowledge of risk and controls associated with peer-to-peer computing, instant messaging and web-based technologies (e.g., social networking, message boards, blogs, cloud computing)
- Knowledge of data classification standards related to the protection of information assets
- Knowledge of the processes and procedures used to store, retrieve, transport and dispose of confidential information assets
- Knowledge of risk and controls associated with data leakage
- Knowledge of security risk and controls related to end-user computing
- Knowledge of methods for implementing a security awareness program
- Knowledge of information system attack methods and techniques
- Knowledge of prevention and detection tools and control techniques
- Knowledge of security testing techniques (e.g., penetration testing, vulnerability scanning)
- Knowledge of processes related to monitoring and responding to security incidents (e.g., escalation procedures, emergency incident response team)
- Knowledge of the processes followed in forensics investigation and procedures in the collection and preservation of the data and evidence (i.e., chain of custody).
- Knowledge of fraud risk factors related to the protection of information assets
Important concepts from exam point of view:
- What is Information Security Management Systems (ISMS)?
- Represents the collation of all the interrelated/interacting information security elements of an organization so as to ensure policies, procedures, and objectives can be created, implemented, communicated, and evaluated to better guarantee an organization’s overall information security
- This system is typically influenced by the organization’s needs, objectives, security requirements, size, and processes
- Includes and lends to effective risk management and mitigation strategies
- What is the importance of Information Security Management Systems (ISMS)?
- Ensure the continued availability of their information systems and data.
- Ensure the integrity of the information stored on their computer systems and while in transit.
- Preserve the confidentiality of sensitive data while stored and in transit.
- Ensure conformity to applicable laws, regulations, and standards.
- Ensure adherence to trust and obligation requirements in relation to any information relating to an identified or identifiable individual (i.e., data subject) in accordance with its privacy policy or applicable privacy laws and regulations.
- Ensure that sensitive data are adequately protected while stored and when in transit, based on organizational requirements.
- What are the key elements of Information security management?
- An ISMS is defined in the International Organization for Standardization (ISO)/International Electro-Technical Commission (IEC) 27000 series of standards and guidelines
- The first standard in this series was ISO/IEC 17799:2000; this was a fast-tracking of the existing British Standard BS 7799part 1:1999
- The initial release of BS 7799was based, in part, on an information security policy manual developed by the Royal Dutch/Shell Group in the late 1980s and early 1990s
- ISO 27000 series is as follows:
- ISO 27001
- ISO 27002
- ISO 27003
- ISO 27004
- ISO 27005
PART 2 – CISA Domain 5 – Protection of Information assets
|
- What is the classification of Information assets?
- Effective control requires a detailed inventory of information assets.
- Creating this list is the first step in classifying assets and determining the level of protection needed for each asset.
- Information assets have varying degrees of sensitivity and criticality in meeting business objectives
- Classification of information assets reduces the risk and cost of over- or under-protecting information resources in linking security to business objectives because it helps to build and maintain a consistent perspective of the security requirements for information assets throughout the organization
- Most organizations use a classification scheme with three to five levels of sensitivity.
- The number of classification categories should take into consideration the size and nature of the organization and the fact that complex schemes may become too impractical to use.
- Data classification is a major part of managing data as an asset.
- Data classification as a control measure should define:
- The importance of the information asset
- The information asset owner
- The process for granting access
- The person responsible for approving the access rights and access levels
- The extent and depth of security controls
- If documents or media are not labeled according to a classification scheme, this is an indicator of the potential misuse of information. Users might reveal confidential information because they did not know that the requirements prohibited disclosure.
- Below is the example of classification of assets:
- HIGHLY RESTRICTED: This classification label applies to the most private or otherwise sensitive information of the Company. Information under this classification shall be strictly monitored and controlled at all times. (e.g., merger and acquisition documents, corporate-level strategic plans, litigation strategy memos, reports on breakthrough new product research, and Trade Secrets such as certain computer programs.)
- CONFIDENTIAL:This classification label applies to Company information, which is private or otherwise sensitive in nature and shall be restricted to those with a legitimate business need for access. (e.g., employee performance evaluations, customer transaction data, strategic alliance agreements, unpublished internally generated market research, computer passwords, identity token personal identification numbers (PINs), and internal audit reports).
- INTERNAL USE ONLY:This classification label applies to information intended for use within the Company, and in some cases, within affiliated organizations, such as business partners of the Company. Assets of this type are widely-distributed within the Company and may be distributed within the Company without permission from the information asset owner. (e.g., telephone directory, dial-up computer access numbers, new employee training materials, and internal policy manuals.
- PUBLIC:This classification applies to information that has been explicitly approved by the Company’s management for release to the public. Assets of this type may be circulated without potential harm. (e.g., product and service brochures, advertisements, job opening announcements, and press releases.)
Points to remember:
|
- What are the various fraud risk factors?
- Fraud is the crime of using dishonest methods to take something valuable from a person or organization.
- There can be many reasons why a person commits fraud, but one of the more accepted models is the fraud triangle, which was developed by criminologist Donald R. Cressey
- Below are the three key elements in the fraud triangle:
- Motivation – a perceived financial (or other) need
- Rationalization – the way the fraudster justifies the crime to himself/herself
- Opportunity – the method by which the crime is to be committed. Opportunity is created by the abuse of position and authority, poor internal controls, poor management oversight, etc.
- What is Information Security Control design?
- Information security is maintained through the use of controls
- Controls can be
- Proactive controls – Controls which attempt to prevent an incident (Safeguards)
- Reactive controls – Controls that allow the detection, containment, and recovery from an incident (Countermeasures)
- Every organization has some controls in place, and a risk assessment should document these controls and their effectiveness in mitigating risk
- Effective control is one that prevents, detects and/or contains an incident and enables recovery from an event
- Controls are divided into three categories:
- Managerial controls – Controls related to the oversight, reporting, procedures, and operations of a process. These include policy, procedures, balancing, employee development, and compliance reporting.
- Technical controls – Controls, also known as logical controls and are provided through the use of technology, a piece of equipment or device. Examples include firewalls, network or host-based intrusion detection systems (IDSs), passwords, and antivirus software. Technical control requires proper managerial (administrative) controls to operate correctly.
- Physical controls – Controls that are locks, fences, closed-circuit TV (CCTV), and devices that are installed to physically restrict access to a facility or hardware. Physical controls require maintenance, monitoring, and the ability to assess and react to an alert should a problem be indicated.
- Controls within the above groups can be classified into:
- Preventive controls – internal controls which are deployed to prevent the happening of an event that might affect the achievement of organizational objectives
- Detective controls – Detective controls seek to identify when preventive controls were not effective in preventing errors and irregularities, particularly in relation to the safeguarding of assets.
- Corrective controls – When detective control activities identify an error or irregularity, corrective control activities should then see what could or should be done to fix it, and hopefully put a new system in place to prevent it the next time around.
PART 3 – CISA Domain 5 – Protection of Information assets
|
| Points to remember:
1. Security administration efforts are BEST reduced through the deployment of – Role-based access controls (RBACs) |
- What is System Access Permission?
- System access permission is the prerogative to act on a computer resource.
- This usually refers to a technical privilege, such as the ability to read, create, modify or delete a file or data; execute a program, or open or use an external connection
- System access to computerized information resources is established, managed and controlled at
- the physical level and/or
- the logical level
- Physical controls:
- The controls restrict the entry and exit of personnel to an area such as an office building, suite, data center, or room containing information processing equipment such as a local area network (LAN) server.
- There are many types of physical access controls, including badges, memory cards, guard keys, true floor-to-ceiling wall construction fences, locks, and biometrics.
- Logical system access controls:
- Restrict the logical resources of the system (transactions, data, programs, applications) and are applied when the subject resource is needed.
- On the basis of Identification and Authentication of the user that requires a given resource and by analyzing the security profiles of the user and the resource, it is possible to determine if the requested access is to be allowed (i.e., what information users can utilize, the programs or transactions they can run, and the modifications they can make).
- Such controls may be built into the operating system (OS), invoked through separate access control software and incorporated into application programs, database systems, network control devices, and utilities (e.g., real-time performance monitors).
- What are Mandatory Access Controls (MACs) and Discretionary Access Controls (DACs
- Mandatory Access Controls (MACs):
- MACs are logical access control filters used to validate access credentials that cannot be controlled or modified by normal users or data owners; they act by default
- With mandatory access control, the security policy is centrally controlled by a security policy administrator; users do not have the ability to override the policy and, for example, grant access to files that would otherwise be restricted
- Discretionary Access Controls (DACs):
- Controls that may be configured or modified by the users or data owners
- This would be the case of data owner-defined sharing of information resources, where the data owner may select who will be enabled to access his/her resource and the security level of this access.
- DACs cannot override MACs; DACs act as an additional filter, prohibiting still more access with the same exclusionary principle.
- What are the other types of Access controls?
- Role-based access control (RBAC) – Provides access based on the position an individual hold in the organization
- Rule-based access control (RAC) – Dynamically assign rules to users based on criteria defined by owner or system administrator
- Organization-based access control (OrBAC) – allows the policy designer to define a security policy independently of the implementation
PART 4 – CISA Domain 5 – Protection of Information assets
|
- What does privacy mean, and how is it different from Confidentiality?
- Privacy means freedom from unauthorized intrusion or disclosure of information about an individual (data subject).
- It is an organization-wide matter that, by its nature, requires a consistent approach throughout the organization
- A good practice to ensure this includes the following:
- The privacy should be considered from the outset and be built in by design.
- Private data should be collected fairly in an open, transparent manner. Only the data required for the purpose should be collected in the first instance.
- Private data should be kept securely throughout their life cycle.
- Private data should only be used and/or disclosed for the purpose for which they were
- Private data should be accurate, complete, and up to date.
- Private data should be deleted when they are no longer required.
- In terms of information,privacy is the right of an individual to have some control over how his or her personal information (or personal health information) is collected, used, and/or disclosed. Confidentiality, on the other hand, is a far slimmer concept than privacy. Confidentiality is the duty to ensure information is kept secret only to the extent possible.
- Privacy talks about a person, but Confidentiality is about information. Privacy restricts the public from accessing the personal details about a person, whereas Confidentiality protects the information from the range of unauthorized persons
- What are the privacy principles and the role of IS auditors?
- IS auditors may be asked to support or perform a review of privacy impact analysis. Such assessments should:
- Pinpoint the nature of personally identifiable information associated with business processes.
- Document the collection, use, disclosure, and destruction of personally identifiable information.
- Ensure that accountability for privacy issues exists.
- Identify legislative, regulatory, and contractual requirements for privacy.
- Be the foundation for informed policy, operations, and system design decisions based on an understanding of privacy risk and the options available for mitigating that risk.
- The IS auditor may also be called on to give assurance on compliance with the privacy policy, laws, and other regulations. To fulfill this role, the IS auditor should:
- Identify and understand legal requirements regarding privacy from laws, regulations, and contract agreements.Examples include the Organisation for Economic Co-operation and Development (OECD) Guidelines on the Protection of Privacy and Transborder Flows of Personal Data, European Union Data Protection Directives, and the US-EU Safe Harbor Framework. Depending on the assignment, IS auditors may need to seek legal or expert opinion on these.
- Review management’s privacy policy to ascertain whether it takes into consideration the requirement of these privacy laws and regulations.
- Check whether sensitive personal data are correctly managed with respect to these requirements.
- Verify that the correct security measures are adopted.
- What are the privacy-related compliance requirements?
- ISO/IEC 29100:2011 – Information Technology – Security techniques – Privacy framework – provides a privacy framework which
- specifies a common privacy terminology;
- defines the actors and their roles in processing personally identifiable information (PII);
- describes privacy safeguarding considerations; and
- provides references to known privacy principles for information technology.
- ISO/IEC 27018:2014 – Information technology — Security techniques — Code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors
- ISO/IEC 27701: 2019 – Privacy extension of ISO/IEC 27001 – The design goal is to enhance the existing Information Security Management System (ISMS) with additional requirements in order to establish, implement, maintain, and continually improve a Privacy Information Management System (PIMS). The standard outlines a framework for Personally Identifiable Information(PII) Controllers and PII Processors to manage privacy controls to reduce the risk to the privacy rights of individuals
| PART 5 – CISA Domain 5 – Protection of Information assets
» What are the Critical Success Factors to Information Security Management? » What are the different mechanisms available for raising information security awareness? » What are the various Human Resources security? |
- What are the Critical Success Factors to Information Security Management?
- Security Awareness, Training, and education:
- Security awareness program should include the following:
- Training (often administered online)
- Quizzes to gauge retention of training concepts
- Security awareness reminders such as posters, newsletters or screensavers
- A regular schedule of refresher training
- Security awareness program should include the following:
- Strong leadership, direction, and commitment by senior management on security training are needed. This commitment should be supported by a comprehensive program of formal security awareness training
- A professional risk-based approach must be used systematically to identify sensitive and critical information resources and to ensure that there is a clear understanding of threats and risks. Thereafter, appropriate risk assessment activities should be undertaken to mitigate unacceptable risk and ensure that residual risk is at an acceptable level
- What are the different mechanisms available for raising information security awareness?
- Computer-based security awareness and training programs
- Email reminders and security tips
- Written security policies and procedures (and updates)
- Nondisclosure statements signed by the employee
- Use of different media in promulgating security (e.g., company newsletter, web page, videos, posters, login reminders)
- Visible enforcement of security rules
- Simulated security incidents for improving security
- Rewarding employees who report suspicious events
- Periodic reviews
- Job descriptions
- What is the various Human Resources security?
- Screening and Background verifications and checks:
- All the candidates for employment, contractors, or third-party users should be subject to background verification checks.
- These should be carried out and documented in accordance with relevant laws, regulations, and ethics, and proportional to the business requirements, the classification of the information to be accessed, and the perceived risk.
- The same process should be followed for hiring candidates through an agency.
- During employment:
- Application of security policies:
- Management should require employees, contractors, and third-party users to apply security in accordance with the established policies and procedures of the organization.
- Management responsibilities should be defined to ensure that security is applied throughout an individual’s employment within the organization.
- A formal disciplinary process for handling security breaches should be established.
- Documentation of responsibilities in the Job description: Specific responsibilities should be documented in approved job descriptions. This will help ensure that employees, contractors, and third-party users are aware of information security threats and concerns, their responsibilities and liabilities, and are equipped to support organizational security policy in the course of their normal work and to reduce the risk of human error
- Employee education, Training, and awareness: An adequate level of awareness, education, and Training in security procedures and the correct use of information processing facilities should be provided to all employees, contractors and third-party users to minimize possible security risk.
- Application of security policies:
- Termination or change of employment:
- When an employee, contractor, or the third-party user exits the organization, responsibilities should be in place to manage this process, including the return of all equipment and removal of all access rights.
- Communication of termination responsibilities should include ongoing security requirements and legal responsibilities.
- Where appropriate, responsibilities contained within any confidentiality agreement and the terms and conditions of employment continuing for a defined period after the end of the employee, contractor, or third-party user’s employment should also be communicated.
- Responsibilities and duties still valid after termination of employment should be contained in the employee, contractor, or third-party user’s contracts.
- Removal of access rights
- The access rights of all employees, contractors and third-party users to information and information processing facilities should be removed upon termination of their employment, contract or agreement, or adjusted upon change.
- The access rights that should be removed or adapted include physical and logical access, keys, identification cards, information processing facilities, subscriptions, and removal from any documentation that identifies them as a current member of the organization. This should include notifying partners and relevant third parties—if a departing employee has access to the third party premises.
- If a departing employee, contractor, or third-party user has known passwords for accounts remaining active, these should be changed upon termination or change of employment, contract, or agreement.
- Access rights for information assets and information processing facilities should be reduced or removed before the employment terminates or changes, depending on the evaluation of risk factors such as:
- Whether the termination or change is initiated by the employee, contractor or third-party user, or by management and the reason for termination
- The current responsibilities of the employee, contractor or any other user
- The value of the assets currently accessible.
| Points to remember:
1. The primary/best method for assuring the integrity of a prospective staff member – Background screening 2. When an employee is terminated from service, the MOST important action is to – disable the employee’s logical access. |
| PART 6 – CISA Domain 5 – Protection of Information assets
» What are the various Computer crime issues and exposures? » Who are the perpetrators in computer crimes? – Hackers – Nations – Script kiddies – Educated or interested outsiders – Employees – Part-time and temporary personnel – IT personnel – Third parties – End users – Opportunists – Formal employees » What are the common attack methods and techniques? – Alternation attack – War driving – Botnets – Eavesdropping (Active and Passive) – Brute force attack – Man-in-the-middle – War dialing – Interrupt attack – War chalking – Masquerading – War walking – Pharming – Piggybacking – Salami |
- What are the various Computer crime issues and exposures?
- Computer systems can be used to fraudulently obtain money, goods, software or corporate information.
- Crimes can also be committed when the computer application process or data are manipulated to accept false or unauthorized transactions.
- Computer crime can be performed without anything physically being taken or stolen, and it can be done remotely.
- Threats to business include:
- Financial loss – These losses can be direct, through the loss of electronic funds, or indirect, through the costs of correcting the exposure.
- Legal repercussions –
- A person cannot use another person’s material without citation and reference. An author has the right to sue a plagiarist. Some plagiarism may also be deemed a criminal offense, possibly leading to a prison sentence.
- The IS auditor should obtain legal assistance when reviewing the legal issues associated with computer security.
- Loss of credibility or competitive edge –
- Many organizations, especially service firms such as banks, savings and loans, and investment firms, need credibility and public trust to maintain a competitive edge.
- A security violation can damage this credibility severely, resulting in loss of business and prestige
- Blackmail/industrial espionage/organized crime –
- Blackmail – is an act of coercion using the threat of revealing or publicizing either substantially true or false information about a person or people unless certain demands are met. It is often damaging information and may be revealed to family members or associates rather than to the general public.
- Industrial espionage – means spying directed towards discovering the secrets of a rival manufacturer or other industrial Company.
- Organized crime – is a category of transnational, national, or local groupings of highly centralized enterprises run by criminals to engage in illegal activity, most commonly for profit. Some criminal organizations, such as terrorist groups, are politically motivated.
- Disclosure of confidential, sensitive, or embarrassing information – As noted previously, such events can damage an organization’s credibility and its means of conducting business. Legal or regulatory actions against the Company may also be the result of the disclosure.
- Sabotage –
- a deliberate action aimed at weakening a polity, effort, or organization through subversion, obstruction, disruption, or destruction.
- “Hacktivism” occurs when perpetrators make nonviolent use of illegal or legally ambiguous digital tools in pursuit of political ends.
- Who are the perpetrators in computer crimes?
- Perpetrators in computer crimes are often the same people who exploit physical exposures, although the skills needed to exploit logical exposures are more technical and complex.
- The following are the probable perpetrators in computer crimes:
- Hackers:
- Hackers are also known as crackers.
- Persons with the ability to explore the details of programmable systems and the knowledge to stretch or exploit their capabilities, whether ethical or not.
- Hackers are typically attempting to test the limits of access restrictions to prove their ability to overcome the obstacles
- Some hackers seek to commit a crime through their actions for some level of personal gain or satisfaction
- Script kiddies:
- Script kiddies are also known as Skiddies.
- Script kiddies are an unskilled individual who uses existing computer scripts or codes to hack into computers, lacking the expertise to write their own.
- Employees (authorized or unauthorized) – Affiliated with the organization and given system access based on job responsibilities, these individuals can cause significant harm to an organization. Therefore, screening prospective employees through appropriate background checks are an important means of preventing computer crimes within the organization.
- IT personnel – These individuals have the easiest access to computerized information, as they are the custodians of this information. In addition to logical access controls, good SoD and supervision help in reducing logical access violations by these individuals.
- End-User – Personnel who often have a broad knowledge of the information within the organization and have easy access to internal resources
- Former Employees – who have left on unfavorable terms may have access if it was not immediately removed at the time of the employee’s termination or if the system has “back doors.
- Nations – As more critical infrastructure is controlled from the Internet (e.g., supervisory control and data acquisition [SCADA] systems) and more nation’s key organizations and businesses rely on the Internet; it is not uncommon for nations to attack each other.
- Interested or educated outsiders – These may include – Competitors, Terrorists, organized criminals, Hackers looking for a challenge, Script kiddies for the purpose of curiosity, joyriding and testing their newly acquired tools/scripts and exploits, Crackers, Phreakers
- Part-time and temporary personnel – Remember that facility contractors such as office cleaners often have a great deal of physical access and could perpetuate a computer crime.
- Third parties – Vendors, visitors, consultants or other third parties who, through projects, gain access to the organization’s resources and could perpetrate a crime
- Accidental unaware – Someone who unknowingly perpetrates a violation
- Opportunists – Where information is inadvertently left unattended or left for destruction, a passerby can access the same
- Hackers:
- What are the common attack methods and techniques?
- Alternation attack: This occurs when unauthorized modifications affect the integrity of the data or code. A cryptographic hash is a primary defense against alteration attacks.
- Botnets:
- Short form of Robot network
- Botnets comprise a collection of compromised computers (called zombie computers) running software, usually installed via worms, Trojan horses or back doors
- Examples are Denial-of-service (DoS) attacks, adware, spyware, and spam
- Brute force attack:
- Attack launched by an intruder, using many of the password-cracking tools available at little or no cost, on encrypted passwords and attempts to gain unauthorized access to an organization’s network or host-based systems
- The attacker systematically checks all possible passwords and passphrases until the correct one is found.
- War dialing:
- Also known as Dial-in penetration attack.
- a technique to automatically scan a list of telephone numbers, usually dialing every number in a local area code to search for modems, computers, bulletin board systems ( computer servers ) and fax machines .
- Wardriving:
- the act of searching for Wi-Fi wireless networks , usually from a moving vehicle, using a laptop or smartphone
- The practice of driving around businesses or residential neighborhoods while scanning with a laptop computer, hacking tool software and sometimes with a global positioning system (GPS) to search for wireless network names
- War walking – Similar to wardriving, but a vehicle is not used. The potential hacker walks around the vicinity with a handheld device. Currently, there are several free hacking tools that fit in these mini-devices.
- War Chalking:
- The practice of marking a series of symbols (outward-facing crescents) on sidewalks and walls to indicate nearby wireless access points.
- These markings are used to identify hotspots, where other computer users can connect to the Internet wirelessly and at no cost.
- War chalking was inspired by the practice of unemployed migrant workers during the Great Depression in the US, using chalk marks to indicate which homes were friendly.
- Eavesdropping:
- Also known as “Sniffing or snooping attack.”
- An intruder gathers the information flowing through the network with the intent of acquiring and releasing the message contents for either personal analysis or for third parties who might have commissioned such eavesdropping.
- This is significant when considering that sensitive information, traversing a network, can be seen in real-time by all other machines, including email, passwords, and, in some cases, keystrokes.
- These activities can enable the intruder to gain unauthorized access, to fraudulently use information such as credit card accounts, and to compromise the Confidentiality of sensitive information that could jeopardize or harm an individual’s or an organization’s reputation.
- There are two types of eavesdropping attack:
- Passive eavesdropping – The hacker simply listens to data that is passing through the network.
- Active eavesdropping – The hackers disguise themselves. This allows them to impersonate a website where users would normally share their private data.
- Interrupt attack:
- Occurs when a malicious action is performed by invoking the OS to execute a particular system call
- Example: A boot sector virus typically issues an interrupt to execute a write to the boot sector.
- Man-in-the middle attack:
- The following scenarios are possible:
- The attacker actively establishes a connection to two devices. The attacker connects to both devices and pretends to each of them to be the other device. Should the attacker’s device be required to authenticate itself to one of the devices, it passes the authentication request to the other device and then sends the response back to the first device. Having authenticated himself/herself in this way, the attacker can then interact with the device as he/she wishes. To successfully execute this attack, both devices have to be connectable.
- The attacker interferes while the devices are establishing a connection. During this process, the devices have to synchronize the hop sequence that is to be used. The aggressor can prevent this synchronization so that both devices use the same sequence but a different offset within the sequence.
- Types of Man-in-the middle attack – IP snoofing, DNS snoofing, HTTPS snoofing, SSL hijacking, Email hijacking, Wi-Fi eavesdropping, stealing browser cookies.
- The following scenarios are possible:
- Masquerading:
- The term masquerade means “pretend to be someone one is not/ be disguised or passed off as something else.”
- An active attack in which the intruder presents an identity other than the original identity. The the purpose is to gain access to sensitive data or computing/network resources to which access is not allowed under the original identity.
- Impersonation both by people and machines falls under this category.
- Pharming:
- An attack that aims to redirect the traffic of a web site to a bogus web site
- In recent years, both pharming and phishing have been used to steal identity information.
- Pharming has become a major concern to businesses hosting e-commerce and to online banking web sites. For example, A web page created to deceive visitors into believing that it is another company’s web page. A user may create a web page that appears to be for a specific bank, requesting a username and password for login.
- Sophisticated measures known as anti-pharming are required to protect against this serious threat. Antivirus software and spyware removal software cannot protect against pharming.
- Piggybacking:
- Piggyback attackis an active form of wiretapping.
- The act of following an authorized person through a secured door or electronically attaching to an authorized telecommunications link to intercept and possibly alter transmissions.
- Piggybacking is considered a physical access exposure
- Salami:
- A Salami attack is a series of minor attacks that together results in a larger attack.
- Involves slicing small amounts of money from a computerized transaction or account.
- A real-time example is that an employee of a bank in the USA had his employment terminated. The man introduced a logic bomb into the bank’s servers. The logic bomb was programmed to debit ten cents from all the accounts registered in the bank and transfer them into the account of the person whose name was alphabetically the last in the bank’s records. Later, he had opened an account in the name of Ziegler. The amount transferred was so little that nobody had noticed the fault. However, it had been brought to light when a person by the name of Zygler opened his account in the same bank. He was surprised to find a large amount of money being transferred into his account every week. He reported the ‘mistake’ to the bank, and the former employee was prosecuted.
| Points to remember:
1. A monitored double-doorway entry system, also referred to as a mantrap or dead man door, is used as a deterrent control for the vulnerability of piggybacking. |
| Points to remember:
1. Active attack based on if and then logic – Logic bomb 2. Ping of Death is the result of denial-of-service attack 3. The expansion of a network infrastructure to support a wireless solution increases the risk of which type of attack – War driving 4. Sniffing is an attack that can be used to capture sensitive pieces of information (e.g., a password) passing through the network 5. Spoofing is forging an address and inserting it into a packet to disguise the origin of the communication. 6. Data destruction is erasing information or removing it from its original location. 7. Traffic analysis is a passive attack to a network 8. Message modification, Masquerading and denial-of-service attack are active attacks to a network |
| PART 7 – CISA Domain 5 – Protection of Information assets
» What are the various phases of incident response? » What are the logical access exposures? » What is Identification and authentication (I&A)? |
- What are the various phases of the incident response?
- Planning and preparation
- Detection
- Initiation
- Recording
- Evaluation
- Containment
- Eradication
- Escalation
- Response
- Recovery
- Closure
- Reporting
- Post-incident review
- Lessons learned
- What are the logical access exposures?
- Exposures that arise through accidental or intentional Exploitation of Logical Access Control weaknesses include technical exposures such as destroying data, compromising system usability, distracting processing resources at either the network, platform, database or application level.
- Technical exposures include the following:
- Data leakage:
- Involves siphoning or leaking information out of the computer.
- This can involve dumping files to paper or can be as simple as stealing computer reports and tapes.
- Unlike product leakage, data leakage leaves the original copy, so it may go undetected.
- Wiretapping:
- Involves eavesdropping on information being transmitted over telecommunications lines.
- Computer shutdown:
- Initiated through terminals or personal computers connected directly (online) or remotely (via the Internet) to the computer.
- Only individuals who know a high-level logon ID usually can initiate the shutdown process, but this security measure is effective only if proper security access controls are in place for the high-level logon ID and the telecommunications connections into the computer.
- Some systems have proven to be vulnerable to shutting themselves down under certain conditions of overload.
- Data leakage:
- What is Identification and authentication (I&A)?
- Identification and Authentication (I&A) is a logical access control software is a process of establishing and providing one’s identity.
- Before proceeding further, let us understand the difference identification, authorization, Authentication to be more clear on the concepts.
- Identification occurs when someone claims an identity (such as with a username)
- Authentication occurs when someone proves their identity (such as entering a password)
- Once that person’s identity is proven, authorization techniques can grant or block access to objects based on their proven identities.
- So, Identification and Authentication (I&A) is a process by which the systems obtain from a user his/her claimed identity and the credentials needed to authenticate this identity and validates both pieces of information.
| PART 8 – CISA Domain 5 – Protection of Information assets
» What are the common I&A vulnerabilities? » What are the categorization of Authentication? » What are the various authentication techniques? |
- What are the common I&A vulnerabilities?
- Weak authentication methods (e.g., no enforcement of password minimum length, complexity and change frequency)
- Use of simple or easily guessed passwords
- The potential for users to bypass the authentication mechanism
- The lack of Confidentiality and integrity for the stored authentication information
- The lack of Encryption for Authentication and protection of information transmitted over a network
- The user’s lack of knowledge on the risk associated with sharing authentication elements (e.g., passwords, security tokens)
- What is the categorization of Authentication?
- Authentication is categorized into three as below:
- Something you know (Example: Password)
- Something you have (Example: Token card)
- Something you are/ you do (Example: a biometric feature)
- These techniques can be used independently or in combination to authenticate and identify a user.
- What are the various authentication techniques?
- A Single-factor authentication technique (something you know) involves the use of the traditional logon ID and password/credential.
- A Two-factor authentication technique (also known as 2FA) is a combination of any three above categories. For example, something you know, such as a personal identification number (PIN), combined and associated with something you have, such as a token card, is a Two-factor authentication technique. Another example is withdrawing money from an ATM; only the correct combination of a bank card(something you have) and a PIN (something you know) allows the transaction to be carried out.
- A Multi-factor authentication technique (also known as MFA) is a combination of more than one method, such as token and password (or PIN or token and biometric device). MFA is an effective method to provide enhanced security. Examples of Multi-factor Authentication include using a combination of these elements to authenticate:
- Codes generated by smartphone applications
- Badges, USB devices, or other physical devices
- Soft tokens, certificates
- Fingerprints
- Codes sent to an email address
- Facial recognition
- Retina or iris scanning
- Behavioral analysis
- Answers to personal security questions
| PART 9 – CISA Domain 5 – Protection of Information assets
» What are biometric access controls? » How does biometric access control system work? » What are the various biometric devices/techniques? – Physically oriented biometric devices o Palm-based o Hand Geometry o Retina scan o Iris scan o Finger prints o Face recognition – Behaviour oriented biometric devices o Signature recognition |
- What are biometric access controls?
- Biometrics Access controlsecurity systems are designed to restrict physical entry to only users with authorization.
- Biometric access controls are the best means of authenticating a user’s identity based on a unique, measurable attribute or trait for verifying the identity of a human being
- This control restricts computer access based on physical (something you are) or behavioral (something you do) characteristic of the user.

| Points to remember:
1. Biometric door locks – This system is used in instances when extremely sensitive facilities must be protected such as in the military |
- How does biometric access control system work?
- A biometric access control system is a pattern recognition unit that gathers a specific type of biometric data from a person, focuses on a relevant feature of that data, compares that feature to a preset group of attributes in its database, and then performs an action based on the accuracy of the comparison.
- There are a variety of characteristics that can be used for biometric comparisons, such as fingerprints, irises, hand geometries, voice patterns, or DNA information, and although there are certain limitations to biometric capabilities, an effective system can precisely identify an individual based on these factors.
- A standard biometric access control system is composed of four main types of components:
- A sensor device,
- A quality assessment unit,
- Feature comparison and the matching unit, and
- A database.
- What are the various biometric devices/techniques?
- The types of biometric devices/ techniques are divided into two, which are as follows:
- Physically oriented biometrics
- Behavior oriented biometricsOn each of the biometric device, let us have an overview of the device, how the biometric device operates, the advantages and disadvantages of them.
- Physically oriented biometrics:
- Palm-based biometric devices:
- These devices analyze physical characteristics associated with the palm, such as ridges and valleys.
- This biometric involves placing the hand on a scanner where physical characteristics are captured.
- Hand Geometry:
- This type of biometric device is one of the oldest techniques.
- This technique is concerned with measuring the physical characteristics of the users’ hands and fingers from a three-dimensional perspective.
- The user places his hand, palm-down, on a metal surface with five guidance pegs to ensure that fingers are placed properly and in the correct hand position.
- The template is built from measurements of physical geometric characteristics of a person’s hand (usually 90 measurements) – for example, length, width, thickness, and surface area.
- Iris scan:
- An Iris, which has patterns associated with the colored portions surrounding the pupils, is unique for every individual and, therefore, a viable method for user identification.
- To capture this information, the user is asked to center his/her eye onto a device by seeing the reflection of their iris in the device. Upon this alignment occurs, a camera takes a picture of the user’s iris and compares it with a stored image.
- The iris is stable over time, having over 400 characteristics, although only approximately 260 of these are used to generate the template.
- As is the case with fingerprint scanning, the template carries less information than a high-quality image.
- Advantage of Iris scan – Contact with the device is not needed, which contrasts with other forms of identification such as fingerprint and retinal scans
- Disadvantages of iris scan – The iris recognition are the high cost of the system, as compared to other biometric technologies, and the high amount of storage requirements needed to uniquely identify a user.
- Retina scan:
- A retinal scan is a biometric technique that uses unique patterns on a person’s retina blood vessels.
- Retina scan uses optical technology to map the capillary pattern of the eye’s retina.
- The user has to put his eye within 0.4 to 0.8 inches (1 to 2 cm) of the reader while an image of the pupil is taken.
- The patterns of the retina are measured at over 400 points to generate a 96-byte template.
- Advantages of Retina scanning: Retinal scan is extremely reliable, and it has the lowest FAR among the current biometric methods.
- Disadvantages of Retina scanning: The need for fairly close physical contact with the scanning device, which impairs user acceptance, and the high cost.
- Fingerprints:
- Fingerprint access control is commonly used biometric technique
- The user places his/her finger on an optical device or silicon surface to get his/her fingerprint scanned.
- The template generated for the fingerprint, named “minutiae,” measures bifurcations, divergences, enclosures, endings, and valleys in the ridge pattern.
- It contains only specific data about the fingerprint (the minutiae), not the whole image of the fingerprint itself.
- Additionally, the full fingerprint cannot be reconstructed from the template.
- Depending on the provider, the fingerprint template may use between 250 bytes to more than 1,000 bytes.
- More storage space implies lower error rates. Fingerprint characteristics are described by a set of numeric values.
- While the user puts the finger in place for between two and three seconds, a typical image containing between 30 and 40 finger details is obtained, and an automated comparison to the user’s template takes place.
- Advantages of fingerprint scanning:
- Low cost,
- The small size of the device,
- Ability to physically interface into existing client-server–based systems, and
- ease of integration into existing access control methods.
- Disadvantages of fingerprint scanning:
- the need for physical contact with the device and the possibility of poor-quality images due to residues, such as dirt and body oils, on the finger.
- Fingerprint biometrics are not as effective as other techniques.
- Face Recognition:
- In this biometric device, the biometric reader processes an image captured by a video camera, which is usually within 24 inches (60 cm) of the human face, isolating it from the other objects captured within the image.
- The reader analyzes images captured for general facial characteristics.
- The template created is based on either generating two- or three-dimensional mapping arrays or by combining facial-metric measurements of the distance between specific facial features, such as the eyes, nose, and mouth. Some vendors also include thermal imaging in the template.
- Advantages of facial recognition:
- The face is considered to be one of the most natural and most “friendly” biometrics
- It is acceptable to users because it is fast and easy to use.
- Disadvantages of face recognition:
- The lack of uniqueness, which means that people who look alike may fool the device.
- Some systems cannot maintain high levels of performance as the database grows in size.
- Palm-based biometric devices:
- Behavior oriented biometrics:
- Signature recognition:
- They are also referred to as Signature dynamics.
- This biometric technique can be operated in two ways:
- Static: In this mode, users write their signature on paper, digitize it through an optical scanner or a camera, and the biometric system recognizes the signature analyzing its shape. This group is also known as “off-line”.
- Dynamic:In this mode, users write their signature in a digitizing tablet, which acquires the signature in real-time. Another possibility is the acquisition by means of stylus-operated PDAs. Some systems also operate on smartphones or tablets with a capacitive screen, where users can sign using a finger or an appropriate pen. Dynamic recognition is also known as “online.”
- Advantages of signature recognition:
- It is fast, easy to use, and has a low implementation cost.
- Even though a person might be able to duplicate the visual image of
- someone else’s signature, it is difficult if not impossible to duplicate the dynamics (e.g., the time duration in signing, pen-pressure, how often pen leaves signing block, etc.)
- Disadvantages of signature recognition:
- They are capturing the uniqueness of a signature, particularly when a user does not sign his/her name in a consistent manner. For example, this may occur due to illness/disease or the use of initials versus a complete signature.
- Users’ signing behavior may change when signing onto signature identification and authentication “tablets” versus writing the signature in ink onto a piece of paper.
| Points to remember:
1. Biometrics – provides authentication based on a physical characteristic of a subject 2. Retina scan – highest reliability and lowest false-acceptance rate (FAR) among the current biometric methods. 3. Iris pattern – The biometric parameter that is better suited for authentication use over a long period of time |
| PART 10 – CISA Domain 5 – Protection of Information assets
» What are the quantitative measures to determine the performance of biometric control devices? – False-error rate (FER) – False-acceptance rate (FAR) – Equal Error rate (EER) » What is Single sign-on? What are its advantages and disadvantages? » What are firewall security systems? |
- What are the quantitative measures to determine the performance of biometric control devices?
- The following are the three quantitative measures to determine the performance of biometric control devices.
- False-Rejection Rate (FRR)
- False-Acceptance Rate (FAR)
- Equal Error Rate (EER)
-
- The lower the overall measure, the more effective the biometric
- False-Rejection Rate (FRR):
- It relates to the percentage of identification instances in which authorized persons are incorrectly rejected.
- It is also known as a Type-1 error rate.
- False-Acceptance Rate (FAR):
- It relates to the percentage of identification instances in which unauthorized persons are incorrectly accepted.
- It is also known as the Type-2 error rate.
- Equal Error rate:
- Each biometric system may be adjusted to lower FRR or FAR, but as a general rule when one decreases, the other increases (and vice versa), and there is an adjustment point where the two errors are equal.
- An overall metric related to the two error types is the equal error rate (EER), which is the percent showing when false rejection and acceptance are equal.
- What is Single sign-on? What are its advantages and disadvantages?
- An authentication scheme that allows a user to log in with a single ID and password to any of several related, yet independent, software systems
- The SSO process begins with the first instance where the user credentials are introduced into the organization’s IT computing environment.
- The information resource or SSO server handling this function is referred to as the primary domain.
- Every other information resource, application, or platform that uses those credentials is called a secondary domain.
- Advantages of Single sign-on:
- Multiple passwords are no longer required; therefore, a user may be more inclined and motivated to select a stronger password.
- It improves an administrator’s ability to manage users’ accounts and authorizations to all associated systems.
- It reduces administrative overhead in resetting forgotten passwords over multiple platforms and applications.
- It reduces the time taken by users to log into multiple applications and platforms.
- Disadvantages of Single sign-on:
- Support for all major OS environments is difficult.
- SSO implementations will often require a number of solutions integrated into a total solution for an enterprise’s IT architecture.
- The costs associated with SSO development can be significant when considering the nature and extent of interface development and maintenance that may be necessary.
-
- The centralized nature of SSO presents the possibility of a single point of failure and total compromise of an organization’s information assets. For this reason, strong Authentication in the form of complex password requirements and the use of biometrics is frequently implemented.
- What are firewall security systems?
- In the world of computer firewall protection, a firewall refers to a network device that blocks certain kinds of network traffic, forming a barrier between a trusted and an untrusted network.
- It is analogous to a physical firewall in the sense that firewall security attempts to block the spread of computer attacks
- Firewalls are hardware and software combinations that are built using routers, servers, and a variety of software. They separate networks from each other and screen the traffic between them
| PART 11 – CISA Domain 5 – Protection of Information assets
» What are the general features of firewall? » What are the types of firewall? 1. Packet Filter firewall 2. Application firewall systems and 3. Stateful Inspection firewall » What is packet filter firewall, its advantages and disadvantages? |
- What are the general features of a firewall?
The following are the features of a firewall:
- Block access to particular sites on the Internet
- Limit traffic on an organization’s public services segment to relevant addresses and ports
- Prevent certain users from accessing certain servers or services
- Monitor communications and record communications between an internal and an external Network
- Monitor and record all communications between an internal network and the outside world to investigate network penetrations or detect internal subversion
- Encrypt packets that are sent between different physical locations within an organization by creating a VPN over the Internet (i.e., IPSec, VPN tunnels)
- What are the types of firewalls?
- There are three basic types of firewalls that are used by companies to protect their data & devices to keep destructive elements out of network, which is as follows:
- Packet Filter firewall
- Application firewall systems and
- Stateful Inspection firewall
- What are a packet-filter firewall, its advantages, and disadvantages?
- It is also known as a “Static filtering firewall.”
- The simplest and earliest kinds of firewalls (i.e., the first generation of firewalls) were packet filtering-based firewalls deployed between the private network and the Internet.
- Packet filters act by inspecting packets transferred between computers. When a packet does not match the packet filter’s set of filtering rules, the packet filter either drops (silently discards) the packet, or rejects the packet (discards it and generates an Internet Control Message Protocol notification for the sender) else it is allowed to pass.
- Packets may be filtered by source and destination network addresses, protocol, source, and destination port numbers.
- Advantages:
- They can process packets at very fast speeds.
- They easily can match on most fields in Layer 3 packets and Layer 4 segment headers, providing a lot of flexibility in implementing security policies.
- Disadvantages/limitations:
- Its simplicity is a disadvantage because it is vulnerable to attacks from improperly configured filters and attacks tunneled over permitted services.
- If a single packet filtering router is compromised, every system on the private network may be compromised, and organizations with many routers may face difficulties in designing, coding, and maintaining the rule base.
- Some of the more common attacks against packet filter firewalls are – IP spoofing, Source routing specification, Miniature fragment attack.
| PART 12 – CISA Domain 5 – Protection of Information assets
» What is Application firewall systems, its advantages and disadvantages? » What is Stateful inspection firewall, its advantages and disadvantages? » What are the various firewall implementations that are commonly used? |
- What are Application firewall systems, its advantages, and disadvantages?
- It is also known as a “Proxy firewall.”
- An application firewall is a type of firewall that scans, monitors and controls network, Internet, and local system access and operations to and from an application or service.
- This type of firewall makes it possible to control and manage the operations of an application or service that’s external to the IT environment.
- The application firewall systems are of two types:
- Circuit-level firewall systems
- Application-level firewall systems
- Circuit-level firewall systems:
- This works at the session layer of the OSI model, between the application layer and transport layer of the TCP/IP stack.
- It creates a connection (circuit) between the two communicating systems
- This type of proxy cannot look into the contents of a packet; thus, it does not carry out deep-packet inspection. It can only make access decisions based upon protocol header and session information that is available to it
- This firewall system does not provide the deep-inspection capabilities of an application-layer proxy.
- Application-level firewall systems:
- This works at the application layer of the OSI model
- An application-level proxy firewall has one proxy per-protocol hence one application-level proxy per-protocol is required (FTP, SMTP, NTP, HTTP)
- Each proxy is a piece of software that has been designed to understand how a specific protocol talks and how to identify suspicious data within a transmission using that protocol.
- This firewall system requires more processing per packet and thus are slower than a circuit-level proxy firewall
- This firewall system provides more protection than circuit-level proxy firewalls
- What are a Stateful inspection firewall, its advantages, and disadvantages?
- It is also known as a “dynamic filtering firewall.”
- A stateful inspection firewall keeps track of the destination IP address of each packet that leaves the organization’s internal network.
- Whenever the response to a packet is received, its record is referenced to ascertain and ensure that the incoming message is in response to the request that went out from the organization.
- This is done by mapping the source IP address of an incoming packet with the list of destination IP addresses that are maintained and updated.
- This approach prevents any attack initiated and originated by an outsider.
- Advantages:
- Stateful firewalls are aware of the state of a connection. Stateful firewalls typically build a state table and use this table to allow only returning traffic from connections currently listed in the state table
- Stateful firewalls do not have to open up a large range of ports to allow communication. The state table is used to determine whether this is returning traffic; otherwise, the filtering table is used to filter the traffic.
- Stateful firewalls prevent more kinds of DoS attacks than packet-filtering firewalls and have more robust logging.
- Disadvantages/limitations:
- They can be complex to configure.
- They cannot prevent application-layer attacks.
- They do not support user authentication of connections.
- Not all protocols contain state information.
- Some applications open multiple connections, some of which use dynamic port numbers for additional connections.
- Additional overhead is involved in maintaining a state table.
- What are the various firewall implementations that are commonly used?
The following are the various firewall implementations that are commonly used across organizations:
- Screened-host firewall
- Dual-homed firewall
- Dematerialized zone (DMZ) or screened-subnet firewall
- Screened-host firewall:
- The screened host firewall combines a packet-filtering router with an application gateway located on the protected subnet side of the router.
- A screened host firewall architecture uses a host (called a bastion host) to which all outside hosts connect, rather than allowing direct connection to other, less secure, internal hosts.
- To achieve this, a filtering router is configured so that all connections to the internal network from the outside network are directed toward the bastion host.
- Dual-homed firewall:
- This is a firewall system that has two or more network interfaces, each of which is connected to a different network
- One facing the external network and
- The other facing the internal network
- The host controls or prevents the forwarding of traffic between NICs.
- This can be an effective measure to isolate a network
- This is a firewall system that has two or more network interfaces, each of which is connected to a different network
- Dematerialized zone (DMZ) or Screened-subnet firewall:
- This firewall system is also known as the “Triple-homed firewall.”
- This architecture adds another layer of security to the screened-host architecture.
- The external firewall screens the traffic entering the DMZ network.
- However, instead of the firewall then redirecting the traffic to the internal network, an interior firewall also filters the traffic.
- The use of these two physical firewalls creates a DMZ
- The screened-subnet approach provides more protection than a stand-alone firewall or a screened-host firewall because three devices are working together and all three devices must be compromised before an attacker can gain access to the internal network
| PART 13 – CISA Domain 5 – Protection of Information assets
» What is Intrusion Detection Systems (IDS) and its types? » What are the components of Intrusion Detection Systems (IDS)? » What are the features of Intrusion Detection Systems (IDS)? |
- What are Intrusion Detection Systems (IDS) and its types?
- An intrusion detection system is a device or software application that monitors a network or system for malicious activity or policy violations.
- Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management system.
- IDS has two main types:
- Network intrusion detection system – They identify attacks within the monitored network and issue a warning to the operator.
- Host-based intrusion detection system – They are configured for a specific environment and will monitor various internal resources of the OS to warn of a possible attack.
- What are the components of Intrusion Detection Systems (IDS)?
The Components of an Intrusion Detection System are as follows:
- Sensors that are responsible for collecting data, such as network packets, log files, system call traces, etc.
- Analyzers that receive input from sensors and determine the intrusive activity
- An administration console
- A user interface
- What are the features of Intrusion Detection Systems (IDS)?
The features of Intrusion Detection System are as follows:
- Intrusion detection
- Gathering evidence on intrusive activity
- Automated response (i.e., termination of the connection, alarm messaging)
- Security policy
- Interface with system tools
- Security policy management
| PART 14 – CISA Domain 5 – Protection of Information assets
» What are the limitations of Intrusion Detection Systems (IDS)? » What is Intrusion Prevention Systems (IPS)? » What are honeypots and its types? |
- What are the limitations of Intrusion Detection Systems (IDS)?
An IDS cannot help with the following weaknesses:
- Weaknesses in the policy definition
- Application-level vulnerabilities
- Back doors into applications
- Weaknesses in identification and authentication schemes
- What is Intrusion Prevention Systems (IPS)?
- An intrusion prevention system (IPS) is a form of network security that works to detect and prevent identified threats.
- Intrusion prevention systems continuously monitor your network, looking for possible malicious incidents, and capturing information about them.
- As the name suggests, an IPS is a preventative and proactive technology, whereas an IDS is a detective and after-the-fact technology.
- What are honeypots and their types?
- A honeypot is a software application that pretends to be a vulnerable server on the Internet and is not set up to actively protect against break-ins.
- It acts as a decoy system that lures hackers.
- The more a honeypot is targeted by an intruder, the more valuable it becomes.
- Although honeypots are technically related to IDSs and firewalls, they have no real production value as an active sentinel of networks.
- There are two basic types of honeypots:
- High-interaction – Give hackers a real environment to attack
- Low-interaction – Emulate production environments and provide more limited information
| Points to remember:
1. Honeypots are often used as a detection and deterrent control against Internet attacks. |
| PART 15 – CISA Domain 5 – Protection of Information assets
» What are Honeynets? » What is Cryptography? » What is Encryption and decryption? |
- What are honeynets?
- A honeynet is a group of virtual servers contained within a single physical server, and the servers within this network are honeypots.
- The purpose of this virtual network is to attract the attention of an attacker, similar to how a single honeypot tries to attract the attention of an attacker
- An IDS triggers a virtual alarm whenever an attacker breaches the security of any networked computers.
- A stealthy keystroke logger watches everything the intruder types.
- A separate firewall cuts off the machines from the Internet anytime an intruder tries to attack another system from the honeynet.
- What is Cryptography?
- Cryptographyprovides for secure communication in the presence of malicious third-parties known as adversaries. Encryption uses an algorithm and a key to transform an input (i.e., plaintext) into an encrypted output (i.e., ciphertext).
- It is a method of storing and transmitting data in a form that only those it is intended for can read and process.
- It is also considered a science of protecting information by encoding it into an unreadable format
- Cryptanalysis is the science of studying and breaking the secrecy of encryption processes, compromising authentication schemes, and reverse-engineering algorithms and keys.
- In cryptography, theone-time pad (OTP) is an encryption technique that cannot be cracked, but requires the use of a one-time pre-shared key the same size as, or longer than, the message being sent. In this technique, a plaintext is paired with a random secret key (also referred to as a one-time pad). The one-time pad is also known as Vernum Cipher.
| Points to remember:
1. One-time pad – The type of encryption is proven to be unbreakable. 2. A key distinction between encryption and hashing algorithms is that hashing algorithms are irreversible. |
- What are Encryption and decryption?
- Encryption is the process of encoding information.
- This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext.
- Only authorized parties can decipher a ciphertext back to plaintext and access the original information. This is called decryption.
- It serves as a mechanism to ensure Confidentiality
- Encryption generally is used to:
- Protect data in transit over networks from unauthorized interception and manipulation
- Protect information stored on computers from unauthorized viewing and manipulation
- Deter and detect accidental or intentional alterations of data
- Verify authenticity of a transaction or document
- Encryption is limited in that it cannot prevent the loss or modification of data
- The process of encrypting and decrypting messages involves keys. The two main types of keys in cryptographic systems are:
- Symmetric-key (also known as Unique key/ Secret key)
- Public-key (also known as an asymmetric key)
| PART 16 – CISA Domain 5 – Protection of Information assets
» What is digital signature? » What are the various environmental issues and exposures in Information security? » What are the controls for environmental exposures? » What are the various physical exposure issues and exposures in Information security? » What are the controls for Physical access exposures? |
- What is a digital signature?
-
- A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents. A valid digital signature, where the prerequisites are satisfied, gives a recipient very strong reason to believe that the message was created by a known sender (Authentication) and that the message was not altered in transit (integrity)
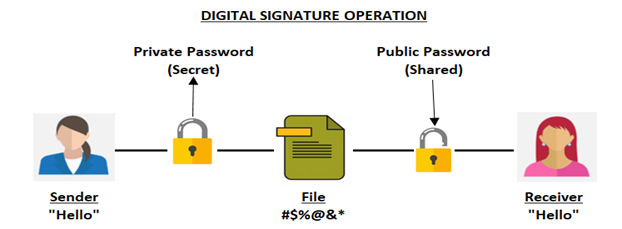
- Therefore, the digital signature ensures:
- Data integrity
- Authentication
- Non-repudiation
| Points to remember:
1. The IS auditor should be familiar with how a digital signature functions to protect data. The specific types of message digest algorithms are not tested on the CISA exam. 2. Digital signature encrypts the hash of the message and not the message. Hence, digital signature does not provide confidentiality or privacy. 3. The private key of the sender is used for encryption of hash of the message 4. Non-repudiation is best described as proving a user performed a transaction that did not change |
- What are the various environmental issues and exposures in Information security?
- Environmental exposures are due primarily to naturally occurring events such as lightning storms, earthquakes, volcanic eruptions, hurricanes, tornados, and other types of extreme weather conditions.
- The result of such conditions can lead to many types of problems. One particular area of concern is the power failures of computers and supporting environmental systems.
- Generally, power failures can be grouped into four distinct categories, based on the duration and relative severity of the failure:
- Total failure (Blackout)
- Severely reduced voltage (brownout)
- Sags (Temp Rapid decreases – Power line conditioners)
- Spikes (1 nanosecond – Temp Rapid Increases – Surge Protector)
- Surges (More than three nanoseconds – Temp Rapid Increases)
- Electromagnetic interference (EMI) – Caused by electrical storms or noisy electrical equipment which result in hang or crash of computer systems
- What are the controls for environmental exposures?
- Alarm control panels
- Water detectors
- Handheld fire extinguishers
- Manual fire alarms
- Smoke detectors
- Fire suppression systems
- Dry-pipe sprinkling systems
- Halon systems
- FM-200
- Argonite
- CO2 systems
| Points to remember:
1. Soda acid should not be used to extinguish a class C (U.S.) fire 2. Although many methods of fire suppression exist, dry-pipe sprinklers are considered to be the most environmentally friendly. 3. The private key of the sender is used for encryption of hash of the message |
- What are the various physical exposure issues and exposures in Information security?
Exposures that exist from an accidental or intentional violation of these access paths include:
- Unauthorized entry
- Damage, vandalism or theft to equipment or documents
- Copying or viewing of sensitive or copyrighted information
- Alteration of sensitive equipment and information
- Public disclosure of sensitive information
- Abuse of data processing resources
- Blackmail
- Embezzlement
- What are the controls for Physical access exposures?
- Bolting door locks
- Combination door locks (cipher locks)
- Electronic door locks
- Biometric door locks
- Manual logging
- Electronic logging
- Identification badges (photo IDs)
- Video cameras
- Security guards
- Controlled visitor access
- Deadman doors (Mantrap)
- Computer workstation locks
- Not advertising the location of sensitive facilities
- The controlled single entry point
- Alarm system
- Secured report/document distribution cart
- Windows
- Touring the information processing facility (IPF)
- Testing of physical safeguards




 1800-843-7890 (India)
1800-843-7890 (India) 
