All About Data Privacy
Data is the new gold and a resource worth billions of dollars in the twenty-first century. Data is valuable in the dark web marketplace and legitimate business, where one organization produces user profiles for partners or competitors for more extensive business arrangements. For example, WhatsApp gives Facebook and other companies access to user information. As data volumes grow and become more valuable, so grows the need for data protection and privacy.
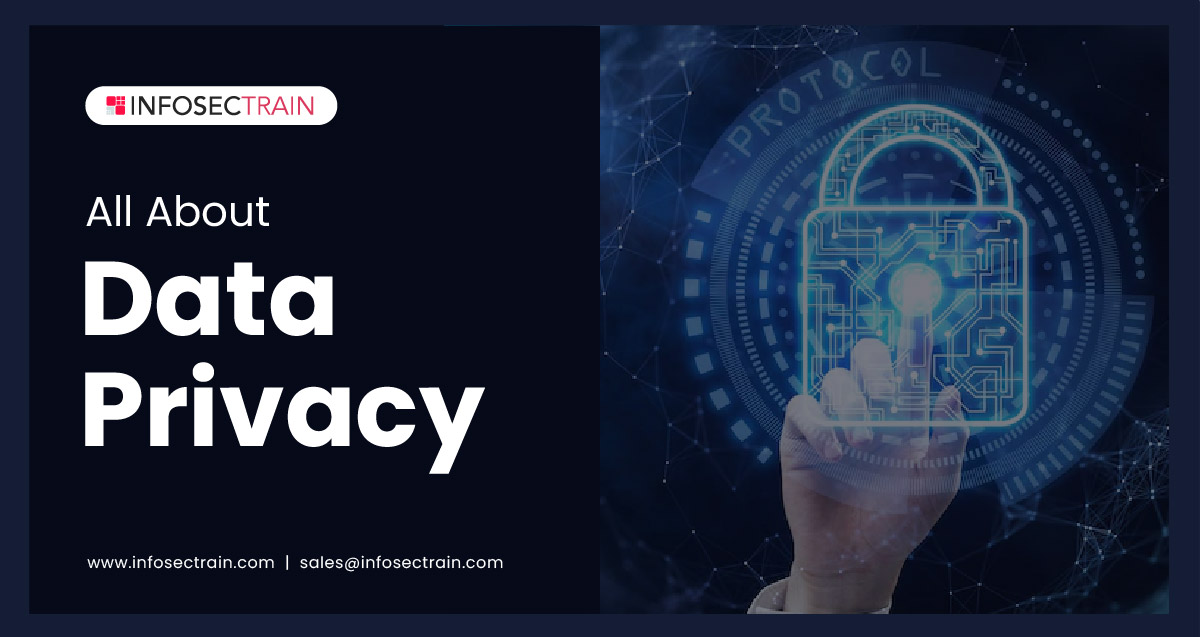
Table of Contents
What is data privacy?
Importance of data privacy
Elements of data privacy
Things you need to know about data privacy
Solutions for data privacy breaches
What is data privacy?
Data privacy, also known as “Data Protection” or “Information Privacy,” refers to the prudent management of information throughout its lifecycle, beginning with data production and ending with data deletion, depending on its relative significance. Data Privacy is a branch of the same that is primarily concerned with data processing and handling. In contrast, Data Security or Data Protection is a more critical word outlining how data can be safeguarded and preventing illegal access to the data.
Importance of data privacy
The importance of data privacy is assessed from both a personal and a commercial point of view:
1. For individuals: The objective of privacy laws worldwide is to offer customers more access to their data by letting them know how, by whom, and for what purposes their information is being used. This provides people with power over how their data is treated and used.
2. For business: Without personal information, businesses cannot function. Therefore, organizations must manage personal data comprehensively and competently, take responsibility for processing personal data, and uphold privacy standards to remain compliant. Otherwise, companies risk massive regulatory fines, customer dissatisfaction, investor appeal, and data breaches.
Elements of data privacy
Data privacy consists of three components:
- Data privacy compliance with data protection laws
- The right of a person to know privacy and management of their data.
- The methods for correctly handling, acquiring, processing, and exchanging personal data.
The need for privacy and data is even more pressing because cyber-attacks are the biggest threat to enterprises worldwide. According to research, a computer is attempted to be hacked every 39 seconds on average, and this astonishing pace is only increasing. Around the world, data protection laws have been implemented to give people back control over their sensitive and personal data and to understand how, by whom, and for what purposes their data is being used.
Consider our data privacy training to make your organization compliant with privacy laws. We’ll teach you all the industry standards for storing information and teach your organization to implement all compliance standards and the relevant privacy and data security laws.
Things you need to know about data privacy
Numerous software programs are available to assist businesses in adhering to the new data privacy laws. We have a list of the most common frameworks that govern what data is acquired from consenting and nonconsenting users:
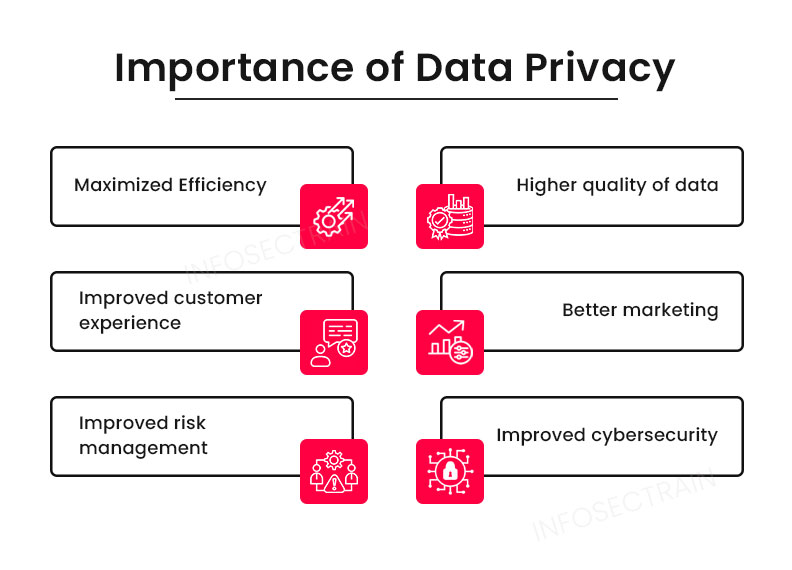
- General Data Protection Regulation (GDPR): This set of guidelines governs the collection, storage, processing, and sharing of personal information about EU individuals with third parties. This framework also addresses the right to be forgotten, which is unique to the EU. Principles for the Lawful Handling of Personal Information are outlined in the General Data Protection Regulation (GDPR).
2. National Data Protection Laws (NDPL): Since the GDPR took effect in May 2018, nations like Canada, Singapore, Australia, Brazil, and Japan have enacted comparable regulations to safeguard the online data of their citizens.
3. California Consumer Privacy Act (CCPA): In California, users must inform about what personal data is gathered and how it is utilized and be able to control and limit how information is stored, handled, and transferred to third parties.
4. PCI-DSS: Regulations established by the Payment Card Industry Data Security Standard (PCI-DSS) must be followed by any business that keeps records of customer’s credit card and bank account information. This compliance standard is about keeping user’s payment information safe so that scams and identity theft don’t happen. To store customer’s financial information, big and small businesses, like online stores and other businesses, must follow the rules set by PCI-DSS.
These regulations are expected to become even stronger in the future. Many privacy advocates argue that there are several ways to circumvent them and that customers still lack sufficient control over their data.
The COVID-19 outbreak has revealed to everyone how quickly what we consider normal can alter. As many business and customer contacts have shifted online, customers, businesses, and authorities are concerned about data privacy.
The management, storage, processing, and sharing of PII (Personal Identification Information) is a topic that is becoming more and more prominent and significant. Since customers are unfamiliar with this new idea, regulatory agencies worldwide are looking for measures to secure this information. Have a look at this report:

Several organizations rarely include a specific tool for data privacy in their regulatory assessments. In the long term, especially for medium and big businesses, this can prove to be an expensive error given the increasingly sophisticated data privacy risks.
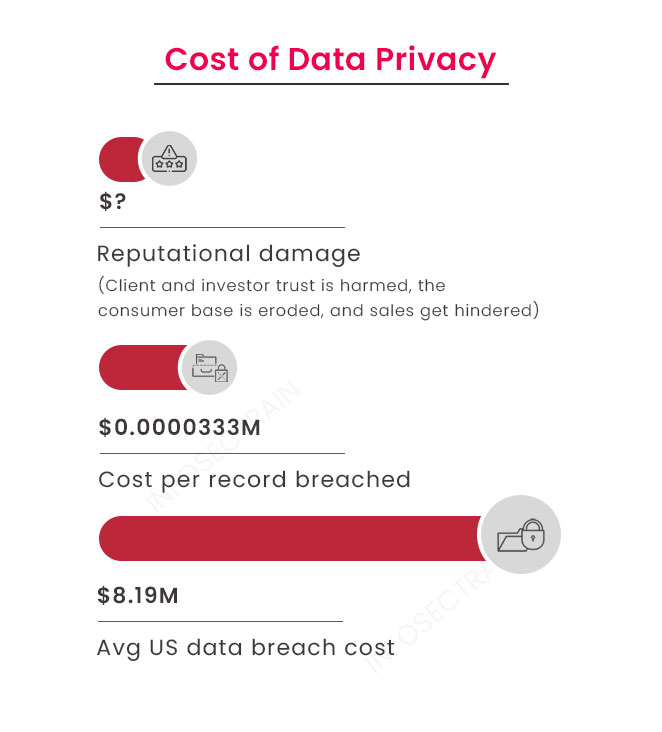
Data breaches are a significant issue, particularly for businesses that keep many sensitive, private information on their clients, partners, or staff. The average cost of data breaches is given below:
Solutions for data privacy breaches
Here are some of the solutions for data privacy breaches:
- Know your sensitive data sources: Sources from the cloud, on-premises, unstructured, structured, and unstructured data sources. What and where are they?
- Know how you will know if it changes: Are PII records being added? And if so, where? Does it change? Assuming a riskier form? How are you going to manage it?
- Know who has access to it: Systems, endpoint devices, and the entire company. Who has access to these personal data?
Data Privacy with InfosecTrain
Data protection has become more important due to technological advancements against security breaches, theft, and loss. Managing personal data in compliance with data rules, regulations, and general privacy is called the discipline of data privacy. Data privacy is one of the essential factors on which every individual, business, or organization relies. If you are interested in learning more about data privacy, check out InfosecTrain.



 1800-843-7890 (India)
1800-843-7890 (India) 
