SOC Analyst Interview Questions & Answers
Due to the rapid increase in data breach incidents and sophisticated attacks, organizations are investing heavily in technologies and security solutions. The deployment of a Security Operation Center (SOC) is a cost-effective strategy against these cyber threats. The SOC team deals with security incidents within the organization. The SOC Analyst plays a vital role in the SOC team by monitoring the log data, identifying suspicious activities, and reporting to the higher authorities. It could be an excellent platform to start your career in cybersecurity. A candidate must have a basic knowledge of networking, malware analysis, and incidence response.

This article outlines the most common SOC Analyst interview questions and answers to help you get selected for a SOC Analyst job role. The questions test the knowledge of candidates about various SOC processes, networking, and web application security.
Question 1: Why does a company require a Security Operations Center (SOC) team?
Answer: The SOC team’s job is to continuously monitor, prevent, detect, investigate, and respond to cyberattacks. The following are the benefits of having a SOC team:
- They keep track of system activities and analyze them regularly
- They monitor and investigate security incidents on a continual basis
- They aid in the reduction of expenses connected with cyber security incident management
- They take a proactive rather than reactive approach
- They make sure that the company follows all applicable regulations and policies
- They assist businesses in promptly responding to external threats and security incidents
- They provide security operations more control and transparency
Question 2: What is the structure of the SOC team?
Answer: The following diagram exhibits a traditional SOC team hierarchy.
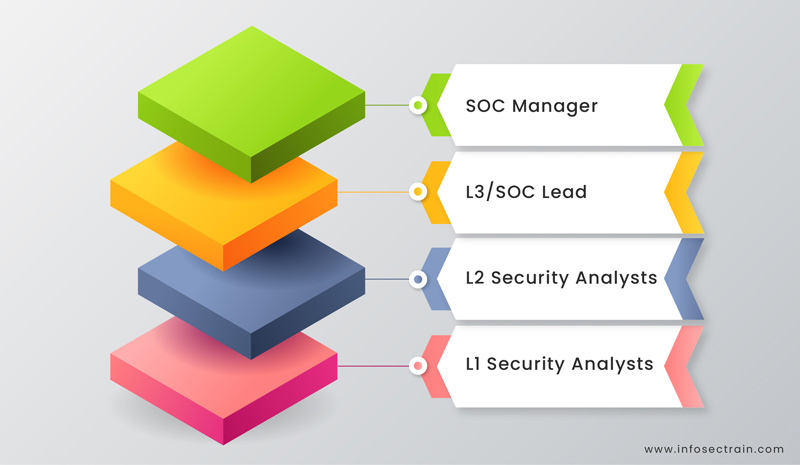
Additional job positions have been introduced to the SOC team structure today. The job titles are as follows:
- Threat Intelligence
- Threat Hunter
- Incident Handler
- Digital Forensic Investigator
- Red Team Specialist
- Incident Response Automation Engineer
Question 3: What are the responsibilities of an L1 and L2 Security Analyst?
Answer: The following are the responsibilities of an L1 Security Analyst:
- They monitor security incidents 24 hours a day, seven days a week, through a variety of SOC entry points
- They use QRadar (SIEM), IDS, IPS, firewall, Cylance, RedCloak, McAfee antivirus, and other tools to monitor and analyze cyber security incidents
- They carry out SOC processes
- They examine the security incidents that have been triggered
- They collaborate with the incident response team to develop remediation strategies
- They assist the L2 Security Analyst and the SOC Lead in the preparation of reports
The following are the responsibilities of an L2 Security Analyst:
- They conduct in-depth analyses of escalated alerts
- They secure the privacy and security of sensitive information
- They verify the incidents that SOC operators have reported
- They help with incident remediation
- They help L1 Security Analysts in the analysis of alerts
- They train the L1 Security Analysts
- They handle primary SIEM challenges
- They keep SOPs and SOC processes up to date and improve them
Question 4: What is the three-way handshake?
Answer: A three-way handshake (also known as TCP-3way handshake) is a mechanism to establish a connection between the client and server over a TCP/IP network. In this mechanism, the client and server send each other the synchronization and acknowledgment packets before an actual data transmission occurs.
Three-way handshake mechanism: In this mechanism, the client sends an SYN TCP packet to the server asking for a connection (synchronizing) request and a sequence number. The server responds with the SYN/ACK packet, acknowledging the connection request and assigning a sequence number. The client again sends an ACK packet to accept the response of the server.
Question 5: What is data leakage? Explain in your own words.
Answer: Data leakage refers to the exposure or transmission of an organization’s sensitive data to the external recipient. The data may be transmitted or exposed via the internet or by physical means.
The following factors can be responsible for data leakage:
- Most of the data losses are accidental. For example, an employee may unintentionally be transmitting information to the wrong recipient.
- Disgruntled employees
- Insecure backup storage
- System breach by a hacker
- Systems not properly configured
- Inappropriate security control measures
Question 6: What are the various SOC models?
Answer: The following are the different SOC models:
- Dedicated or Internal SOC: A Dedicated or internal SOC is a centralized SOC with its infrastructure, people, and processes that are only focused on security. That is, the company creates its own cybersecurity team among its employees. The size of a dedicated SOC is determined by the organization’s size, hazards, and security requirements.
- Virtual SOC: A virtual SOC is a web-based portal based on decentralized security technology that allows teams to watch events and respond to threats from afar. It does not have dedicated infrastructure or reside in a dedicated facility.
- Multifunction SOC: Multifunction SOC combines a Security Operations Center (SOC) and a Network Operations Center (NOC), with specialized personnel, facilities, and infrastructure. It includes IT operations, compliance, risk management, and security functions.
- Co-managed SOC: On-site monitoring solutions expand in a Co-managed SOC, while some functions may be delegated to external staff. Resource restrictions and financial constraints are the main reasons for choosing this model.
- Global SOC: A global SOC, also known as a command SOC, is a high-level group in charge of smaller SOCs spread throughout a massive region.
Question 7: List the steps to develop the Data Loss Prevention (DLP) strategy?
Answer: The steps to develop and implement a DLP strategy are as follows:
- Step1: prioritizing the critical data assets
- Step2: categorizing the data based on its source
- Step3: analyzing which data is more prone to the risks
- Step4: monitor the transmission of the data
- Step5: developing control measures to mitigate the data leakage risk
Question 8: What is the difference between TCP and UDP?
Answer: The difference between TCP and UDP is as follows:
| TCP(Transfer Layer Protocol) | UDP(User Datagram Protocol) |
| TCP is a connection-oriented protocol. | UDP is a datagram oriented protocol. |
| TCP is reliable as it guarantees the delivery of data packets to the destination. | UDP is not reliable as it does not guarantees the delivery of data packets to the destination. |
| TCP Provides a thorough error checking mechanism. | UDP provides a basic error checking mechanism. |
| TCP is heavyweight. | UDP is lightweight. |
| TCP is slower as compared to UDP | UDP IS faster than TCP |
| Failed data packets are retransmitted in TCP. | In UDP, there is no re-transmission for failed data packets. |
| Example: HTTP, SSH, HTTPS, SMTP | Example: TFTP, VoIP, online multiplayer games |
Question 9: What is the difference between firewall deny and drop?
Answer: DENY RULE: If the firewall is set to deny rule, it will block the connection and send a reset packet back to the requester. The requester will know that the firewall is deployed.
DROP RULE: If the firewall is set to drop rule, it will block the connection request without notifying the requester.
It is best to set the firewall to deny the outgoing traffic and drop the incoming traffic so that attacker will not know whether the firewall is deployed or not.
Question 10: What is the SOC Runbook?
Answer: A runbook in SOC is a set of conditional procedures that are used to automatically perform actions, including data enrichment, threat containment, and notification as part of the incident response or security operations process.
Question 11: What is the difference between the Red and Blue Teams?
Answer: Highly skilled cybersecurity professionals make up the Red and Blue Teams. However, the red team consists of offensive security experts who attempt to breach a company’s cybersecurity defenses, while the blue team defends against and responds to the red team attack.
Both teams play a significant role in strengthening an organization’s security posture.
Question 12: What do you understand about cognitive cybersecurity?
Answer: Cognitive security is the use of Artificial Intelligence (AI) technology to detect risks and defend physical and digital systems based on human mental processes.
Question 13: Define a Phishing attack and how to prevent it?
Answer: Phishing is a type of social engineering attack in which an attacker obtains sensitive information from the target by creating urgency, using threats, impersonation, and incentives. Spear phishing, email spam, session hijacking, smishing, and vishing are types of phishing attacks.
Ways to prevent a phishing attack:
- Raising awareness about phishing attacks among employees
- Conducting testing campaigns to check the awareness of the employees
- Implementing two-factor authentication
- Monitoring the behavior of employees
- Applying e-mail filters to identify spams
Question 14: What is the Cross-Site Scripting (XSS) attack, and how to prevent it?
Answer: Cross-site Scripting: In the cross-site scripting attack, the attacker executes the malicious scripts on a web page and can steal the user’s sensitive information. With XSS vulnerability, the attacker can inject Trojan, read out user information, and perform specific actions such as the website’s defacement.
Countermeasures:
- Encoding the output
- Applying filters at the point where input is received
- Using appropriate response headers
- Enabling content security policy
- Escaping untrusted characters
Question 15: Explain the SQL injection vulnerability and give countermeasures to prevent it?
Answer: SQL Injection: SQL injection is a famous vulnerability in the web application that allows hackers to interfere in communication taking place between a web application and its database. Hackers inject malicious input into the SQL statement to compromise the SQL database. They can retrieve, alter, or modify the data. In some cases, it allows attackers to perform DDOS attacks.
Countermeasures:
- Using parameterized queries
- Validating the inputs
- Creating stored procedures
- Deploying a web application firewall
- Escaping untrusted characters
Question 16: Difference between hashing and Encryption?
Answer: The difference between hashing and Encryption is as follows:
| Hashing | Encryption |
| Conversion of data into a fixed-length of unreadable strings using algorithms | Conversion of data into an unreadable string using cryptographic keys |
| Hashed data can not be reverted back into readable strings | Encrypted data can be decrypted back into readable strings |
| The length of the hashed string is fixed | The length of the encrypted string is not fixed |
| No keys are used in hashing | Keys are used in Encryption |
Question 17: What is the difference between SIEM and IDS?
Answer: SIEM (Security Incident and Event Management) system and IDS (Intrusion detection system) are used by organizations to protect the network and systems efficiently. Both collect the log data, but unlike SIEM, IDS does not facilitate event correlation and centralization of log data. Therefore, IDS can only detect intrusions. The SIEM allows security analysts to take security measures and preventive actions against a possible or ongoing attack.
Question 18: What are the stages of SOC implementation?
Answer: The stages of SOC implementation are as follows:
- Create a strategy for your security operations center
- Develop a SOC solution
- Processes, procedures, and training should all be developed
- Make sure your surroundings are ready
- Put your plan into action
- Deploy use cases from beginning to end
- Keep your solution up to date and evolving
Question 19: Being a SOC Analyst, What would you do if you found 300 alerts triggered at once?
Answer: If multiple alerts trigger at the same time, there could be the following three possibilities:
A single alert may have triggered more than once: If a single alert triggers more than once, I will distinguish the duplicate alerts.
If the alerts are different: I will prioritize them and choose the one having a higher impact.
If the alerts are for a new correlation rule: Then alerts may be misconfigured. I will inform the SIEM Engineer.
(These types of questions are asked by the interviewer to check the practical or applied knowledge of the candidates)
Question 20: What is DNS? Why is DNS monitoring essential?
Answer: The domain name system is a distributed database over the internet that enables converting user-friendly hostnames into computer-friendly IP addresses. It is known as the phonebook of the internet.
DNS plays a vital role in how an end-user in an organization connects to the internet. Whenever a client establishes a connection with a domain, its information is stored in DNS logs. DNS monitoring can disclose information such as websites visited by the employee, malicious domain accessed by an end-user, malware connecting to a Command & Control server. It can help in identifying and thwarting cyberattacks.
Wrap up
These were the frequently asked SOC analyst interview questions that might help you get an opportunity to be a SOC team member. The interview questions may vary depending upon the organization. Be prepared for the questions regarding your background and the technologies you have worked on in your previous organization. Just like any other interview, Confidence, and good communication skills are key to success.
It is recommended to validate your technical skills and expertise with the help of some industry-recognized certifications. Check out these certified SOC analyst training program offered by the Infosec Train:
- https://www.infosectrain.com/courses/certified-soc-analyst-csa-certification-training/
- https://www.infosectrain.com/courses/ibm-security-qradar-siem-training/
- https://www.infosectrain.com/courses/soc-analyst-training/
- https://www.infosectrain.com/courses/soc-specialist-training/
- https://www.infosectrain.com/courses/soc-analyst-expert-training/




 1800-843-7890 (India)
1800-843-7890 (India) 
