Disaster Recovery (DR) Strategies
In today’s technologically driven world, quickly recovering from disasters or outages is crucial for organizations to maintain business continuity and safeguard profits. As organizations increasingly depend on sophisticated Information Technology (IT) data and systems, robust Disaster Recovery (DR) strategies become essential. These strategies are vital for ensuring operational continuity and minimizing downtime during unforeseen disasters or disruptions, whether due to natural, technological failures, cyber attacks, or human-induced. Understanding and implementing these strategies can help businesses to recover from such incidents quickly. Below, we have listed the top DR strategies commonly used in organizations, including their specific techniques, advantages, challenges, and illustrative examples.

7 Key Strategies for Disaster Recovery (DR)
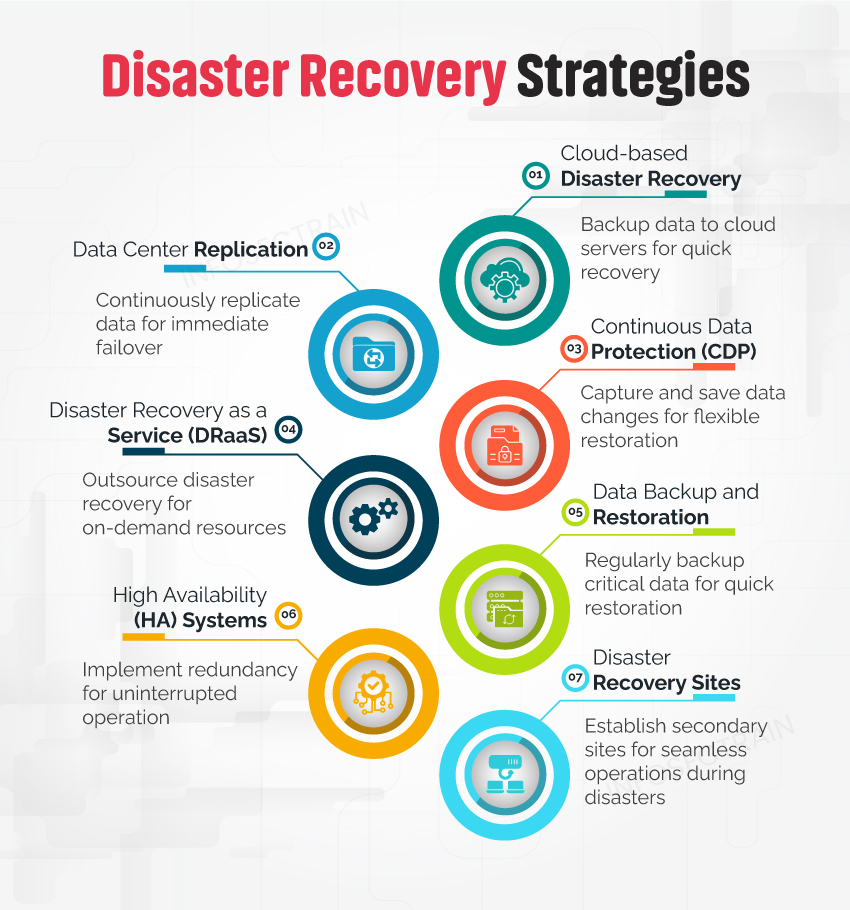
1. Cloud-based Disaster Recovery: This method leverages cloud computing environments to facilitate rapid recovery by utilizing virtualized resources and multi-region deployment to ensure data availability across multiple regions.
Effectiveness: Very high due to its rapid deployment capabilities and minimal downtime.
Advantages:
- Swift deployment
- Minimal downtime
- Data redundancy across regions
Challenges:
- Managing cloud costs effectively
- Ensuring data security in the cloud environment
- Potential for vendor lock-in
- Compliance and regulatory issues
Example: A digital media enterprise uses cloud-based recovery to manage extensive digital content. Deploying its content management system across multiple cloud regions ensures service availability even if one area is compromised.
2. Data Center Replication: This strategy focuses on duplicating data across several data centers through synchronous or asynchronous replication techniques to guarantee data availability and integrity across locations.
Effectiveness: Very high, but often involves significant expenses and resource allocation.
Advantages:
- Enhanced data availability and integrity
- Low RPO (Recovery Point Objective)
- Mitigation of single points of failure
Challenges:
- High costs
- Resource-intensive implementation
- Complex management and coordination required
Example: A global bank uses synchronous replication within the same region to achieve zero data loss for critical transaction systems and asynchronous replication to an overseas data center for less time-sensitive data.
3. Continuous Data Protection (CDP): This technique involves real-time or near-real-time data replication, ensuring that any point-in-time can be restored from backup storage following a disruption.
Effectiveness: High, but can be more expensive and resource-intensive.
Advantages:
- Real-time data replication
- Rapid recovery capability
- Minimal data loss
Challenges:
- High data volume management
- Increased cost of continuous replication
- Resource-intensive implementation
Example: A healthcare institution uses CDP to maintain current patient records and facilitate immediate recovery in any situation.
4. Disaster Recovery as a Service (DRaaS): This strategy utilizes third-party cloud providers to offer scalable and flexible DR solutions, reducing the need for physical DR infrastructure.
Effectiveness: High, particularly for organizations without the capability to maintain their own DR systems.
Advantages:
- Enhanced scalability and flexibility
- Reduced reliance on in-house DR infrastructure
- Access to expert support and resources
Challenges:
- Dependency on third-party providers
- Potential for network latency affecting recovery times
- Security concerns regarding data stored off-site
Example: An e-commerce company utilizes DRaaS to ensure continuous website functionality during server failures, with real-time data replication to a cloud provider.
5. Data Backup and Recovery: This strategy involves regularly saving copies of data in multiple locations, both on-site and off-site, to ensure they can be recovered after a disaster.
Effectiveness: High, though recovery time can be slower than other methods.
Advantages:
- Enhanced data security
- Redundancy minimizes the risk of data loss
- Flexibility in recovery options
Challenges:
- Potential for slower recovery times
- Management complexity increases with multiple backup locations
Example: A retail company performs nightly backups of transaction data, storing it both on-site for swift recovery and in the cloud for disaster readiness.
6. High Availability (HA) Systems: This approach uses redundant hardware and failover mechanisms to maintain operational continuity and minimize downtime by quickly switching to backup systems if a failure occurs.
Effectiveness: High, particularly for critical applications, despite potential costliness.
Advantages:
- Ensures operational continuity
- Minimizes downtime
- Suitable for critical applications
Challenges:
- Costly implementation
- Complex setup and maintenance
Example: A financial institution uses active-active data centers, ensuring both are operational and can handle the full load if one fails.
7. Disaster Recovery Sites: This method involves establishing alternative physical sites (hot, cold, or warm) for seamless operation transfer in case of primary site failure.
Effectiveness: Depends on the chosen setup: hot sites are highly effective but costly, cold sites are less effective but more affordable, and warm sites offer a balance between effectiveness and cost.
Advantages:
- Redundancy ensures continuous operations
- Minimizes downtime and data loss
- Provides peace of mind to stakeholders
Challenges:
- Costly to set up and maintain
- Requires synchronization of data and systems
- Potential for logistical complications
Example: A telecom company maintains a hot site that mirrors its primary operations center to ensure uninterrupted service.
How Can InfosecTrain Help?
At InfosecTrain, we provide various certification training programs focusing on disaster recovery planning, empowering learners to develop robust Disaster Recovery Plans (DRPs). Join our Certified Information Systems Security Professional (CISSP) training course for comprehensive insights into business continuity and disaster recovery principles. This course is delivered by our experienced instructors, who bring extensive expertise and practical insights to the learning experience.
TRAINING CALENDAR of Upcoming Batches For CISSP
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 25-May-2024 | 30-Jun-2024 | 09:00 - 13:00 IST | Weekend | Online | [ Close ] | |
| 01-Jun-2024 | 07-Jul-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 17-Jun-2024 | 28-Jun-2024 | 07:00 - 12:00 IST | Weekday | Online | [ Close ] | |
| 01-Jul-2024 | 01-Aug-2024 | 08:00 - 10:00 IST | Weekday | Online | [ Open ] | |
| 06-Jul-2024 | 11-Aug-2024 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 15-Jul-2024 | 20-Jul-2024 | 09:00 - 18:00 IST | Weekend-Weekday | Classroom Hyderabad | [ Open ] | |
| 20-Jul-2024 | 25-Aug-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 29-Jul-2024 | 09-Aug-2024 | 07:00 - 12:00 IST | Weekday | Online | [ Close ] | |
| 18-Aug-2024 | 23-Aug-2024 | 09:00 - 18:00 IST | Weekend-Weekday | Classroom Dubai | [ Open ] |




 1800-843-7890 (India)
1800-843-7890 (India) 
