Risk Analysis, Evaluation, and Assessment

Many enterprises are highlighting IT risk management as a critical component of their overall risk and compliance operations, with good reason. Recent high-profile cyber-attacks and data breaches have brought technology risk and cybersecurity issues to the forefront. But what’s behind this rise in IT risk?
- More core functions are powered by applications and hardware.
- The majority of essential business procedures are now reliant on technology. As a result, technological failures or breaches can have far-reaching consequences for operations, money, and reputation.
- Organizations are struggling to stay up with the evolving threat environment, which is powered by new and complex technology and growing data amounts.
Table of Contents
IT Risk Management
What is the Importance of IT Risk Management?
Steps in the Risk Analysis Process
Importance of Risk Analysis
Steps in the Risk Assessment Process
Importance of Risk Assessment
Steps in the Risk Evaluation Process
Importance of Risk Evaluation
IT Risk Management
The practice of controlling cybersecurity risks through systems, policy, and technology is known as IT risk management. This approach consists of three primary stages to mitigate vulnerabilities impacting sensitive resources: detection, assessment, and control.
The foundation of risk management consists of three fundamental building blocks:
- Risk Analysis
- Risk Assessment
- Risk Evaluation
What is the Importance of IT Risk Management?
An IT risk management program reduces the effect of data breaches, resulting in significant cost savings. Besides cost reductions, an IT risk management plan includes the following advantages:
- It enables enterprises to become more resilient to cyberattacks.
- It provides stability to business operators.
- It may reduce legal liability.
- It safeguards employees against potential harm.
- It aids in the fulfillment of organizational objectives and the continuity of operations.
1. Risk Analysis
Risk analysis is a multi-step process that aims to reduce the impact of threats on organizational processes. Professionals use risk analysis from various industries to ensure that all elements of the organization are protected from possible risks. Regular risk analysis also reduces the business’s sensitivity to unpredictable circumstances. Or we can simply say that risk analysis is a process of estimating the frequency and size of IT risk situations.
Risk analysis is the initial stage of risk management, which examines the value of assets to the organization, identifies vulnerabilities to those assets, and assesses how sensitive each asset is to those risks.
Steps in the Risk Analysis Process
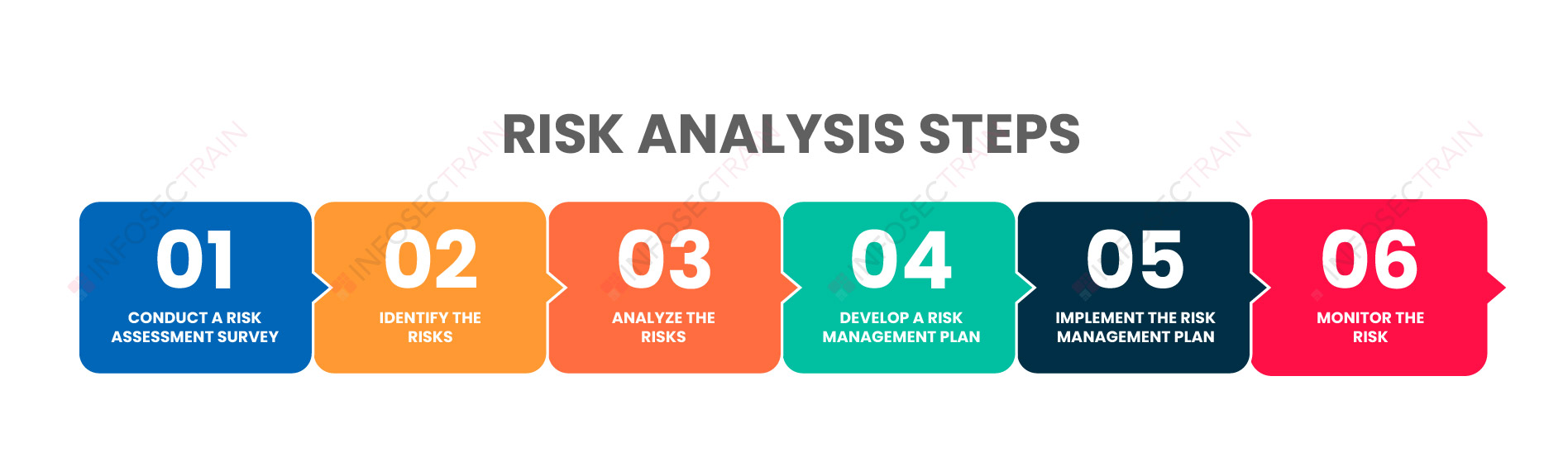
Importance of Risk Analysis
- It anticipates and mitigates the impact of adverse outcomes from bad situations.
- It assesses if a development’s potential risks are balanced by its benefits to aid in decision-making when deciding whether to execute the work.
- It develops strategies for dealing with technological or equipment failures and losses resulting from natural and human-caused events.
- It determines the impact of changes in the enterprise environment and prepares for them.
2. Risk Assessment
Risk assessment is concerned with detecting the dangers to your information systems, networks, and data and estimating the potential consequences of such incidents. Risk assessments should be carried out regularly and whenever significant organizational changes occur. IT risk assessments are an essential component of any effective security operation. Risk assessments enable you to see how your organization’s risks and vulnerabilities change over time, allowing decision-makers to put appropriate measures and checks to respond to threats.
In simpler terms, risk assessment identifies and evaluates risk and its potential consequences.
Steps in the Risk Assessment Process
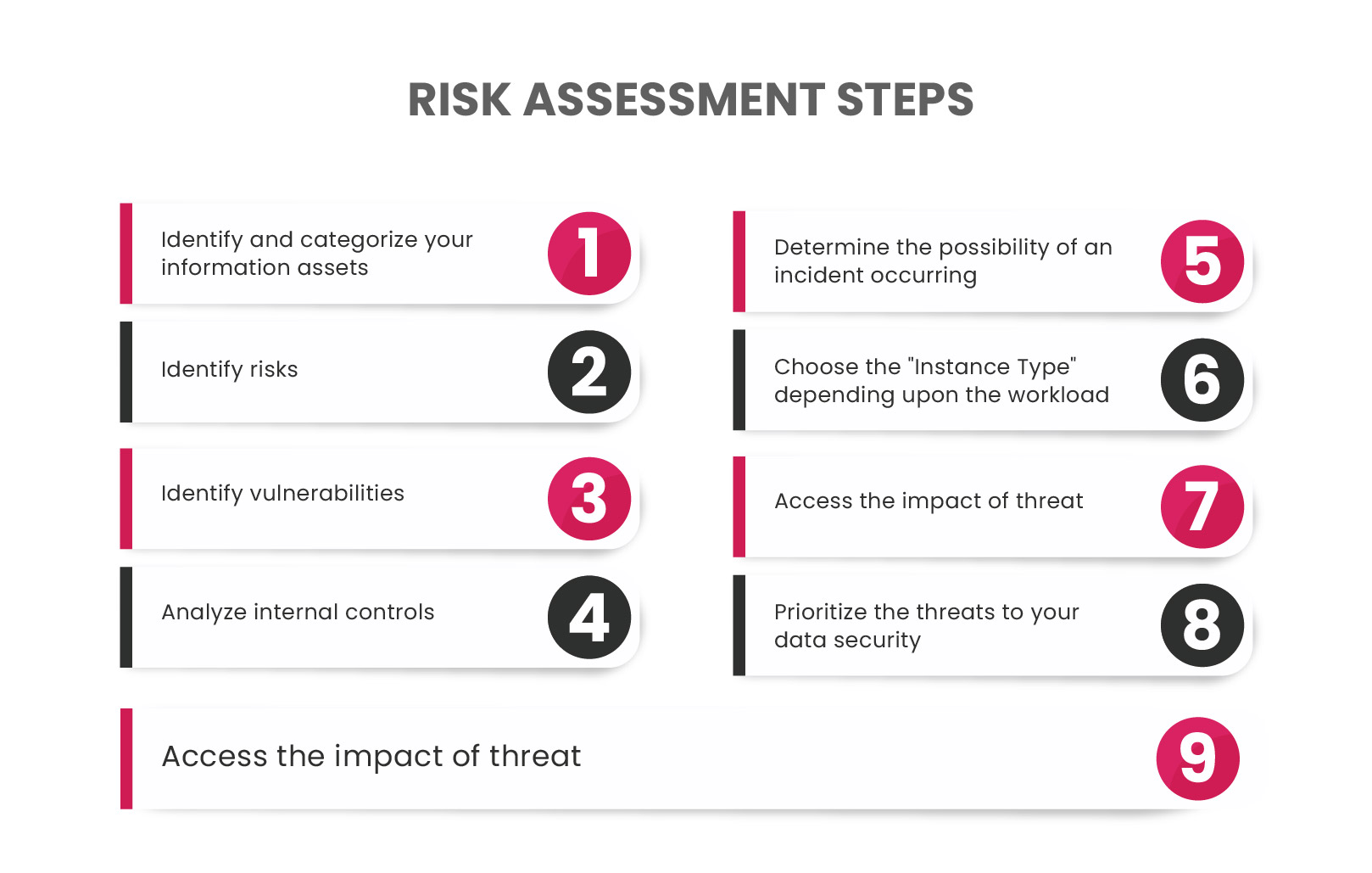
Importance of Risk Assessment
- It assesses threats and methodically ranks risks based on the likelihood of harm, which is critical for prioritizing risk management tasks and allocating resources effectively.
- It identifies and remediates vulnerabilities.
- It is in charge of cataloging IT and data assets.
- Regular IT risk assessments can assist your firm in reducing excessive security expenditures.
- Regular risk assessment is also necessary for businesses that must deal with customer privacy regulations such as PCI DSS or financial disclosure regulations such as SOX.
3. Risk Evaluation
The process of detecting and evaluating risks is known as risk evaluation. Or the technique of determining the significance of a risk by comparing it to specified risk criteria. Anyone in charge of an organization, server, network, or software must evaluate risk. A risk evaluation can assist in evaluating whether those assets are vulnerable to a cyberattack, infection, data loss due to natural disasters, or any other threat.
Steps in the Risk Evaluation Process
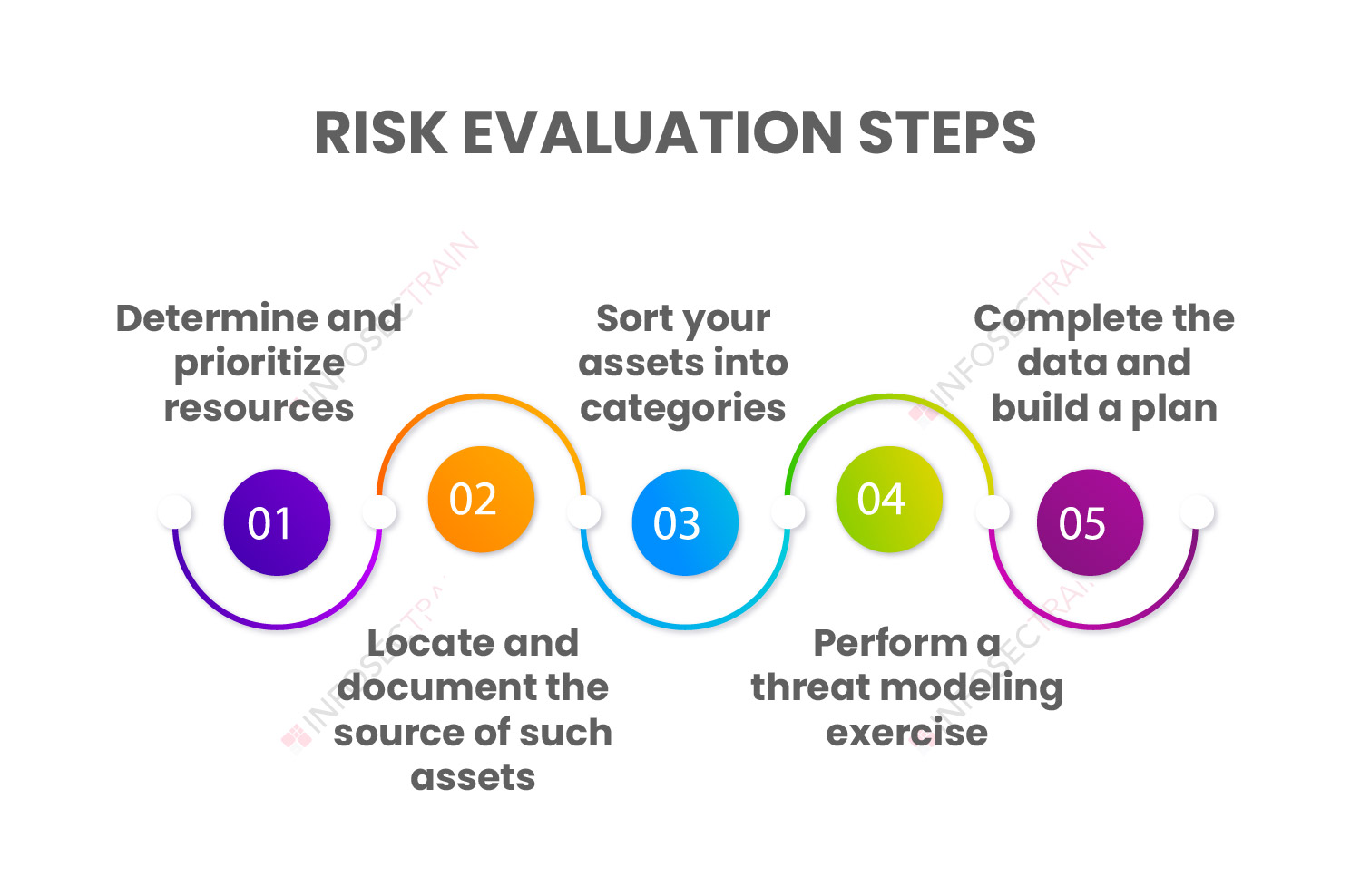
Importance of Risk Evaluation
The value of a risk evaluation is straightforward: it informs IT professionals about where and how their firms and reputation are at risk.
Final Thoughts
Establishing a risk management framework eventually automates standard techniques due to constant continuing surveillance of controls and risk exposure. This leads to more efficient task completion and aids in the reduction of excessive measures inside your firm.
Professionals who have earned the CRISC certification better understand information technology risks. They create strategies and tactics to minimize and manage risks that affect the entire enterprise. So if you are ready to make a career in IT risk management, then CRISC is the right choice for you. CRISC holders help firms analyze business risks and have the technical competence to set up suitable IT controls. InfosecTrain’s CRISC training course prepares IT professionals to handle enterprise risk management concerns. Enroll in our CRISC certification training course to benefit from the knowledge of industry experts.
TRAINING CALENDAR of Upcoming Batches For CRISC
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 05-Apr-2025 | 27-Apr-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |







 1800-843-7890 (India)
1800-843-7890 (India)