Certified Threat Intelligence Analyst (CTIA) Training and Certification
 Read Reviews
Read Reviews
Certified Threat Intelligence Analyst (CTIA) from EC-Council is a credentialing certification and training program. This highly valued certification has been exclusively devised in collaboration with threat intelligence and cybersecurity experts worldwide to empower organizations effectively to identify and mitigate security risks with extensive processing and analysis of available threat information. The CTIA is a specialist level training and certification that demonstrates security professionals the structured approach to acquiring threat intelligence. The CTIA certified candidates attain a competitive edge over other information security professionals. This threat intelligence certification course delivers standards-based, intensive practical skills to the most essentially required threat intelligence across information security.





 5th Sep: Weekend
5th Sep: Weekend 



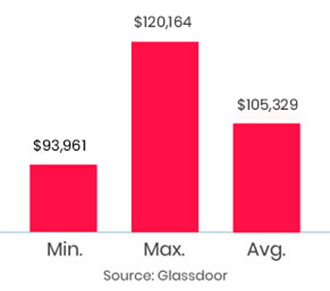

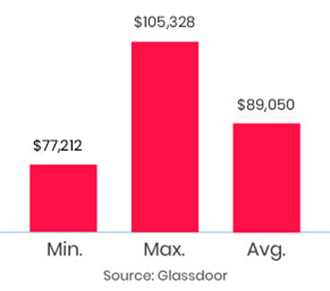

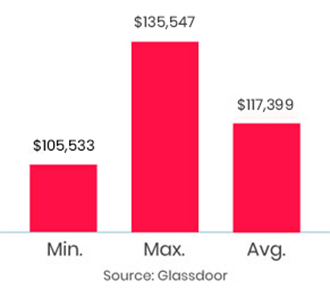



 The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.
The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.






 Certified & Experienced Instructors
Certified & Experienced Instructors Post Training Support
Post Training Support Customized Training
Customized Training Flexible Schedule
Flexible Schedule Access to Recorded Sessions
Access to Recorded Sessions 




 1800-843-7890 (India)
1800-843-7890 (India) 
