CompTIA Security+ SY0-601 Domain 5: Governance, Risk, and Compliance

Security+ SY0-601 Domains
There are 5 domains in the new version of security+ SY0-601.
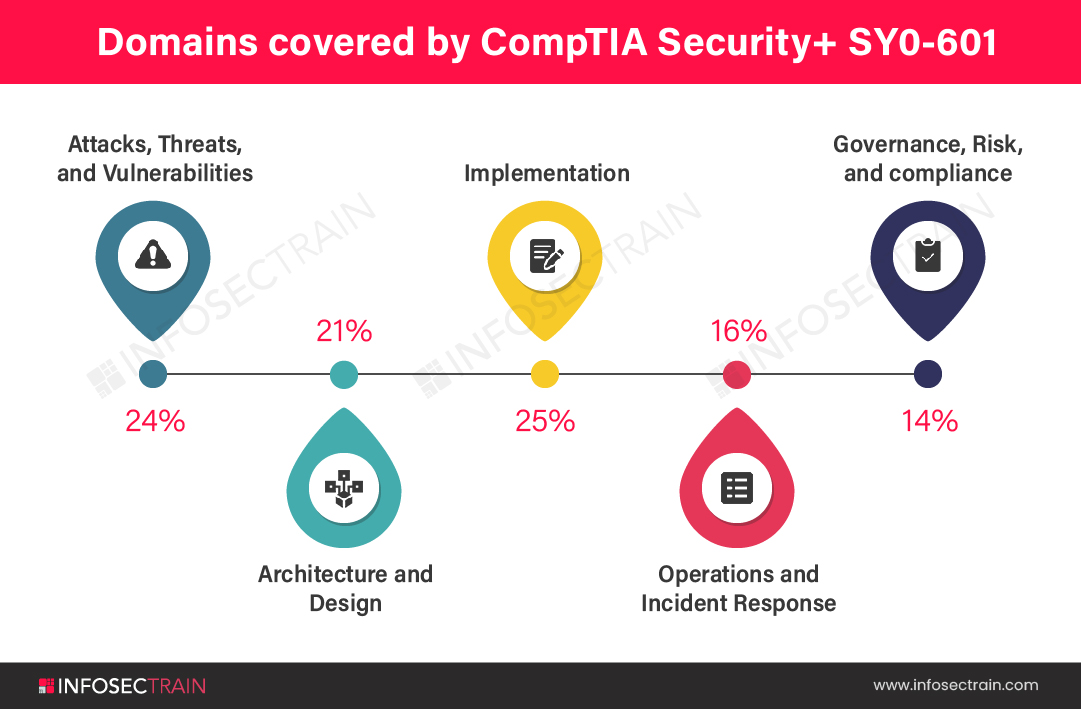
- Domain 1.0: Attacks, Threats, and Vulnerabilities (24%)
- Domain 2.0: Architecture and Design (21%)
- Domain 3.0: Implementation (25%)
- Domain 4.0: Operations and Incident Response (16%)
- Domain 5.0: Governance, Risk, and Compliance (14%)
In this blog, we discuss domain 5.0 Governance, Risk, and Compliance.
Governance, Risk, and Compliance
In the earlier version of Security+ (SY0-501) only risk management was covered in domain 5 but in the latest version of Security+ (SY0-601) domain 5 we have an important concept: Governance, Risk, and Compliance.
GRC or (Governance, Risk, and Compliance) is the process of aligning and integrating IT and business objectives to verify that risks are successfully managed while maintaining efficient business operations and adherence to all applicable industry laws. This domain covers 14% of weightage in the exam.
The topics covered in this domain are listed below:
- Compare and contrast various types of controls
- Explain the importance of applicable regulations, standards, or frameworks that impact the organizational security posture
- Explain the importance of policies to organizational security
- Summarize risk management processes and concepts
- Explain privacy and sensitive data concepts in relation to security
1. Compare and contrast various types of controls
Candidates’ ability to analyze and compare various security controls is tested in this part. In this subdomain, we will understand the Category of controls: Managerial control, Operational control, Technical control. We will get familiar with types of risk controls: Preventive, Detective, Corrective, Deterrent, Compensating, Physical.
2. Explain the importance of applicable regulations, standards, or frameworks that impact the organizational security posture
In this subdomain, we will learn about various Regulations, Standards, and Legislation. Inside this part, we will cover General Data Protection Regulation (GDPR), National, Territory, State laws, Payment Card Industry Data Security Standard (PCI DSS).
This part explains to us the key frameworks of security. Inside this part we will cover the following topics:
- Center for Internet Security (CIS)
- National Institute of Standards and Technology (NIST) Risk Management Framework (RMF)/ Cybersecurity Framework (CSF)
- International Organization for Standardization (ISO) 27001/27002/27701/31000
- SSAE SOC 2 Type I/II
- Cloud security alliance
- Explanation of the Cloud control matrix
In this part, we also learn Benchmarks/secure configuration guides, Platform /vendor-specific guides, Web server, OS, Application server, Network infrastructure devices.
3. Explain the importance of policies to organizational security
In this subdomain, you will understand Personnel management control, Third-party risk management, Data, Credentials policies, Organization policies, and Diversity of training techniques. In personnel management control we cover various topics like Acceptable use policy, Job rotation, Mandatory vacation, Separation of duties, Least privilege, Clean desk space, Background checks, a Non-disclosure agreement (NDA), Social media analysis, Onboarding, Offboarding, User training, Gamification, Capture the flag, Phishing campaigns, Phishing simulations, Computer-based training (CBT).
Third-party risk management focuses on various types of agreements, SLA (Service level agreement), and BPA (Business partnership agreement). This part also covers topics like Supply chain, Memorandum of understanding (MOU), End of service life (EOSL).
4. Summarize risk management processes and concepts
Many companies have proper risk management policies and processes in place to fulfill regulatory obligations and keep their operations safe. In this subdomain, we will summarize the concepts of risk management. We will understand the types of Risk, such as External risk, Internal risk, Legacy systems, Multiparty, IP theft, Software compliance/licensing. The strategies of Risk management, Acceptance, Avoidance, Transference, and Cybersecurity insurance. We will also learn to define Risk analysis, Risk register, Risk control assessment, Single-Loss Expectancy (SLE), Annualized Loss Expectancy (ALE), Annualized Rate of Occurrence (ARO). Also, understand the concept of Business impact analysis (BIA) like Recovery Time Objective (RTO), Recovery Point Objective (RPO), Mean Time To Repair (MTTR) and Mean Time Between Failures (MTBF), Disaster Recovery Plan (DRP), Mission essential functions, and Identification of critical systems.
5. Explain privacy and sensitive data concepts in relation to security
In this subdomain, we will understand the concept of Organizational consequences of privacy and data breaches, Reputation damage, Identity theft, Fines, and IP theft. We also get an in depth understanding of the Data types and classifications of data types Public, Private, Sensitive, Confidential, Critical, Proprietary. We understand Privacy-enhancing technologies like Data minimization, Data masking, Tokenization, Anonymization, Pseudo-anonymization. We get familiar with Roles and responsibilities, Data owners, Data controller, Data custodian/steward, Data Protection Officer (DPO). We will also cover the information life cycle, Impact assessment, Terms of the agreement, and Privacy notice.
Learn Security+ With Us
InfosecTrain is a leading provider of IT security training and consulting organization, focusing on a wide range of IT security training. The training sessions will be delivered by highly qualified and professional trainers with years of industry experience whom you can easily interact with and solve your doubts anytime. If you are interested and looking for live online training, InfosecTrain provides the best online Security+ certification training. You can check and enroll in our CompTIA Security+ Online Certification Training to prepare for the certification exam.




 1800-843-7890 (India)
1800-843-7890 (India) 
