Program Highlights
The ISSAP (Information Systems Security Architecture Professional) Training & Certification program is designed for professionals seeking to enhance their expertise in security architecture. Covering key topics like security frameworks, risk management, and compliance, it provides a solid foundation for developing effective security solutions.
InfosecTrain’s program equips learners with essential skills for the ISSAP certification exam, empowering them to create and manage robust security architectures that protect critical information assets. This course is a crucial step for those aiming to advance their careers in information security architecture.
50-Hour LIVE Instructor-Led Training
Small batch size
Telegram Group for Exam Practice
Highly Interactive and Dynamic Sessions
98% Exam Pass Rate
Learn from Industry Experts
Career Guidance and Mentorship
Post Training Support
Access to Recorded Sessions
Training Schedule
- upcoming classes
- corporate training
- 1 on 1 training
| Start - End Date | Training Mode | Batch Type | Start - End Time | Batch Status | |
|---|---|---|---|---|---|
| 07 Feb - 21 Mar | Online | Weekend | 19:00 - 23:00 IST | BATCH OPEN |
Why Choose Our Corporate Training Solution
- Upskill your team on the latest tech
- Highly customized solutions
- Free Training Needs Analysis
- Skill-specific training delivery
- Secure your organizations inside-out
Why Choose 1-on-1 Training
- Get personalized attention
- Customized content
- Learn at your dedicated hour
- Instant clarification of doubt
- Guaranteed to run
Can't Find a Suitable Schedule? Talk to Our Training Advisor!

The information security architect plays a vital role to implement a sound security program in the organizations as an expert shouldering the role between a C-suite and upper managerial level. As an information security architect or analyst, this role involves executing diverse information security consultative and analytical processes. The ISSAP is an all-embracing certification that validates your technical skills in security architecture and grants the globally accepted credentials of chief security architect or analyst. This extensive certification evaluates your proficiency to develop, design and analyze various security solutions and instills skills to provide risk-based guidance to the higher management in addressing various organizational goals.
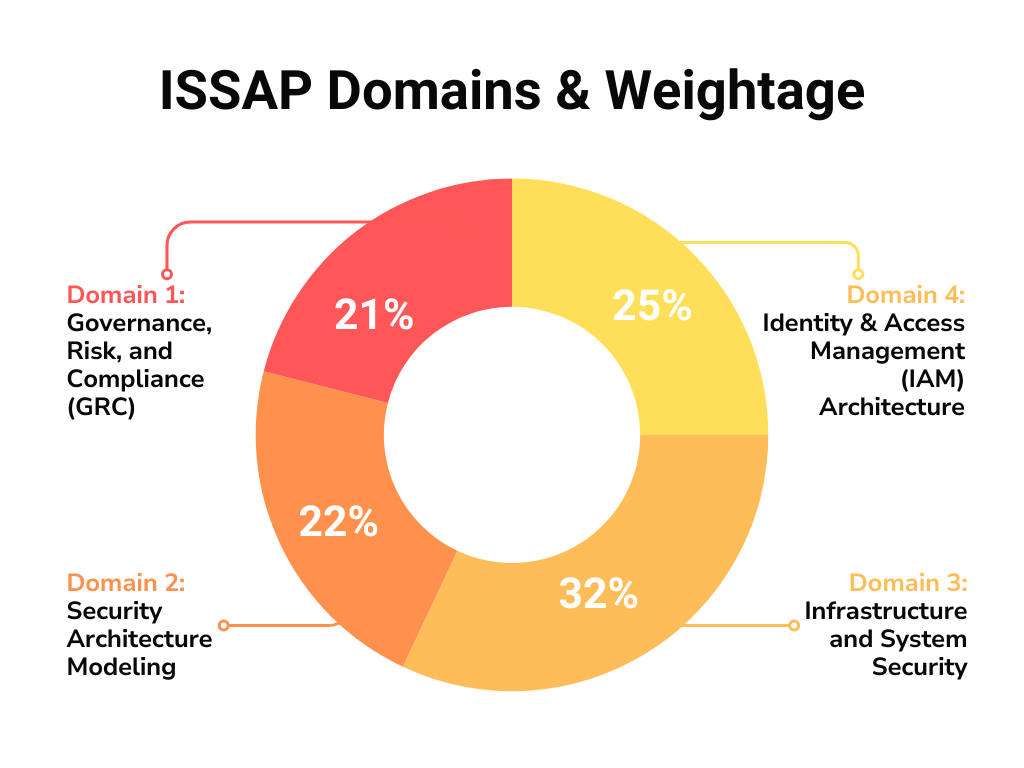
- Domain 1: Governance, Risk, and Compliance (GRC)
- 1.1 Identify legal, regulatory, organizational, and industry requirements
- Applicable information security standards and guidelines
- Third-party and contractual obligations (e.g., supply chain, outsourcing, partners)
- Applicable sensitive/personal data standards, guidelines, and privacy regulations
- Resilient solutions
- 1.2 Architecting for governance, risk, and compliance (GRC)
- Identify key assets, business objectives, and stakeholders
- Design monitoring and reporting (e.g., vulnerability management, compliance audit)
- Design for auditability (e.g., determine regulatory, legislative, forensic requirements,
segregation, high assurance systems) - Incorporate risk assessment artifacts
- Advise risk treatment (e.g., mitigate, transfer, accept, avoid)
- 1.1 Identify legal, regulatory, organizational, and industry requirements
- Domain 2: Security Architecture Modeling
- 2.1 Identify security architecture approach
- Scope (e.g., enterprise, cloud) and types (e.g., network, service-oriented architecture (SOA))
- Frameworks (e.g., The Open Group Architecture Framework (TOGAF), Sherwood Applied
Business Security Architecture (SABSA), service-oriented modeling framework) - Reference architectures and blueprints
- Threat modeling frameworks (e.g., Spoofing, Tampering, Repudiation, Information Disclosure,
Denial of Service, and Elevation of Privilege (STRIDE), Common Vulnerability Scoring System
(CVSS), threat intelligence)
- 2.2 Verify and validate design (e.g., functional acceptance testing, regression)
- Results of threat modeling (e.g., threat vectors, impact, probability)
- Gaps
- Alternative solutions/mitigations/compensating controls
- Internal or external third-party (e.g., tabletop exercises, modeling and simulation, manual
review of functions, peer review) - Code review methodology (e.g., dynamic, manual, static, source composition analysis)
- 2.1 Identify security architecture approach
- Domain 3: Infrastructure and System Security Architecture
- 3.1 Identify infrastructure and system security requirements
- Deployment model (e.g., On-premises, cloud-based, hybrid)
- Information technology (IT) and operational technology
- Physical security (e.g., perimeter protection and internal zoning, fire suppression)
- Infrastructure and system monitoring
- Infrastructure and system cryptography
- Application security (e.g., Requirements Traceability Matrix, security architecture
documentation, secure coding)
- 3.2 Architect infrastructure and system security
- Physical security control set (e.g., cameras, doors, system controllers)
- Platform security (e.g., physical, virtual, container, firmware, operating system (OS))
- Network security (e.g., wired/wireless, public/private, Internet of Things (IoT), management,
firewalls, airgaps, software defined perimeters, virtual private network (VPN), Internet
Protocol Security (IPsec), Network Access Control (NAC), Domain Name System (DNS), Network Time Protocol (NTP), Voice over Internet Protocol (VoIP), Web Application Firewall (WAF)) - Storage security (e.g., direct attached, storage area network (SAN), network-attached storage
(NAS), archival and removable media, encryption) - Data repository security (e.g., access control, encryption, redaction, masking)
- Cloud security (e.g., public/private, Infrastructure as a Service (IaaS), Platform as a Service
(PaaS), Software as a Service (SaaS)) - Operational technology (e.g., industrial control system (ICS), Internet of Things (IoT),
supervisory control and data acquisition (SCADA)) - Endpoint security (e.g., bring your own device (BYOD), mobile, endpoint detection and response
(EDR), host-based intrusion detection system (HIDS)/host-based intrusion prevention system
(HIPS)) - Secure shared services (e.g., e-mail, Voice over Internet Protocol (VoIP), unified
communications) - Third-party integrations (e.g., internal/external, federation, application programming interface
(API), virtual private network (VPN), Secure File Transfer Protocol (SFTP)) - Infrastructure monitoring
- Content monitoring (e.g., email, web, data, social media, data loss prevention (DLP))
- Out-of-band communications (e.g., incident response, information technology (IT) system
management, Business Continuity (BC)/disaster recovery (DR)) - Evaluate applicability of security controls for system components (e.g., web client
applications, proxy services, application services)
- 3.3 Architect infrastructure and system cryptographic solutions
- Determine cryptographic design considerations and constraints (e.g., technologies, lifecycle,
computational capabilities, algorithms, attack in system) - Determine cryptographic implementation (e.g., in-transit, in-use, at-rest)
- Plan key management lifecycle (e.g., generation, storage, distribution)
- Determine cryptographic design considerations and constraints (e.g., technologies, lifecycle,
- 3.1 Identify infrastructure and system security requirements
- Domain 4: Identity and Access Management (IAM) Architecture
- 4.1 Architect identity lifecycle
- Establish identity and verify (e.g., physical, logical)
- Assign identifiers (e.g., to users, services, processes, devices, components)
- Identity provisioning and de-provisioning (e.g., joiners, movers, and leavers process)
- Identity management technologies
- 4.2 Architect identity authentication
- Define authentication approach (e.g., single-factor, multi-factor, risk-based elevation)
- Authentication protocols and technologies (e.g., Security Assertion Markup Language
(SAML), Remote Authentication Dial-In User Service (RADIUS), Kerberos, Open
Authorization (OAuth) - Authentication control protocols and technologies (e.g., eXtensible Access Control
Markup Language (XACML), Lightweight Directory Access Protocol (LDAP)) - Define trust relationships (e.g., federated, stand-alone)
- 4.3 Architect identity authorization
- Authorization concepts and principles (e.g., discretionary/mandatory, Separation of
Duties (SoD), least privilege, interactive, non-interactive) - Authorization models (e.g., physical, logical, administrative)
- Authorization process and workflow (e.g., governance, issuance, periodic review,
revocation, suspension) - Roles, rights, and responsibilities related to system, application, and data access
control (e.g., groups, Digital Rights Management (DRM), trust relationships) - Management of privileged accounts (e.g., Privileged Access Management (PAM))
- Authorization approach (e.g., single sign-on (SSO), rule-based, role-based,
attribute-based, token, certificate)
- Authorization concepts and principles (e.g., discretionary/mandatory, Separation of
- 4.4 Architect identity accounting
- Determine accounting, analysis, and forensic requirements
- Define audit events
- Establish audit log alerts and notifications
- Log management (e.g., log data retention, log data integrity)
- Log analysis and reporting
- Comply with policies and regulations (e.g., PCI-DSS, FISMA, HIPAA, GDPR)
- 4.1 Architect identity lifecycle
ISSAP training helps advancing the technical competencies of:
- System Architects
- Business Analysts
- System and Network Designers
- Chief Security Officers
- Chief Technology Officers
- Candidates must be a CISSP in good standing and have two years cumulative, full-time experience in one or more of the six domains of the current ISSAP Exam Outline.
Or:
- Candidates must have a minimum of seven years cumulative, full-time experience in two or more of the domains of the current ISSAP Exam Outline. Earning a post-secondary degree (bachelors or masters) in computer science, information technology (IT) or related fields or an additional credential from the ISC2 approved list may satisfy one year of the required experience. Part-time work and internships may also count towards the experience requirement.
| Exam Format | Multiple Choice Questions |
| Exam duration | 3 hours |
| No. of Questions | 125 |
| Passing Score | 700 out of 1000 |
| Language | English |
ISSAP certification exam helps you acquire across the board understanding of:
- Core concepts of access control systems, techniques, and access management architecture
- Communications and networks architecture, considerations for security design and associated risks
- Cryptography essentials, design considerations, and integrated cryptographic solutions including Public Key Infrastructure (PKI), API selection and more
- Security architecture approach and analysis, design verification and validations
- Disaster Recovery Planning (DRP), Business Continuity Planning (BCP), and Business Impact Analysis (BIA)
- Security strategies and recovery solutions
- Physical security considerations, requirement assessment, and solutions evaluation
How We Help You Succeed
Vision
Goal
Skill-Building
Mentoring
Direction
Support
Success
Our Expert Course Advisors

18+ Years Of Experience
16+ Years of Experience
Words Have Power

An excellent experience with engaging content! The ISSAP certification course offered valuable insights that will benefit my career immensely.

Overall the ISSAP certification training was good. Trainer was well prepared with the content and target was to prepare for exam.

I thank the whole Infosec training team for conducting the sessions well and in an organized manner. The trainer’s method of teaching the ISSAP course content was great. Sharing real-world scenarios as examples gave a clear picture of the concepts. Thanks again!

A professional and informative training experience! This ISSAP course exceeded my expectations and prepared me well for the challenges ahead.

The effort in teaching the concepts was commendable. Thank you, InfosecTrain, for your dedication to quality training in the ISSAP course!

The trainer was very thorough in explaining technical as well as managerial concepts. The best part of the lectures was explaining the concept using real-world examples and the trainer was not shy to share his personal experiences. This enabled me to relate to the problem statement by remembering the examples and answering the questions. Another good part about the trainer is his approachability; you can always ask him a question and he will satisfy you. There are a lot of things that can be talked about him. Overall, I am extremely satisfied with his training methodology. Regarding Infosec Train, I would also like to mention that they were organised except for a few hiccups with GoToMeeting at the very early stages. However, it can happen to anyone; the important thing is that they promptly addressed the issue and ensured that the rest of the learning sessions remained smooth.
Success Speaks Volumes
Get a Sample Certificate

Frequently Asked Questions
What is the ISSAP Certification, and why should I pursue it?
The ISSAP is an advanced certification under the ISSAP umbrella. It focuses on designing and developing security architectures within an organization. Pursuing this certification validates your expertise in security architecture and opens up career opportunities in senior roles. It enhances your credibility, marketability, and ability to design resilient security systems, making you a valuable asset in any organization.
Who should consider enrolling in the ISSAP Certification course?
ISSAP certification is ideal for:
- System Architects
- Business Analysts
- Chief Security Officers
- Chief Technology Officers
- System and Network Designers
What are the prerequisites for the ISSAP Certification?
Prerequisites:
- Candidates must be ISSAP in good standing.
- At least two years of full-time experience in one or more of the six ISSAP domains.
- Alternatively, seven years of cumulative, full-time experience in two or more domains.
- A relevant bachelor's, master's degree, or ISC2-approved credential can reduce the required experience by one year.
- Part-time work and internships may also contribute to meeting the experience requirement.
What topics are covered in the ISSAP Certification training?
The ISSAP Certification training covers the following topics:
- Integration of security into business processes
- Compliance requirements and frameworks
- Enterprise security architecture design
- Secure network and system design
- Design and implementation of IAM solutions
- Federated identity management
- Security operations management and monitoring and more.
How does the ISSAP Certification benefit my career?
ISSAP certification benefits:
- Opens doors to senior roles like Chief Security Officer (CISO), Director of Security, and Security Consultant.
- Connects you with a global community of ISC2-certified professionals.
- Enhances your professional credibility and attractiveness to employers.
- Qualifies you for specialized positions in various industries.
How long is the ISSAP Certification valid, and how do I maintain it?
The ISSAP certification is valid for three years. To maintain it, certified members must:
If you have ISSAP :
- Earn 60 Continuing Professional Education (CPE) credits every three years, specific to security architecture.
- No additional Annual Maintenance Fee (AMF) required.
If you don't have ISSAP :
- Earn 140 CPE credits every three years.
- No extra AMF if you hold another ISC2 certification, except for Certified in Cybersecurity (CC), where the AMF increases to $135.
If ISSAP is your first ISC2 certification, the AMF is $135.
What is the exam format for the ISSAP Certification?
The ISSAP certification exam consists of multiple-choice questions.
Can I take the ISSAP exam online?
Currently, the ISSAP exam cannot be taken online. ISC2 requires candidates to take the exam at authorized test centers via Pearson VUE due to concerns over security and integrity with online proctoring.
What is the passing score for the ISSAP Certification exam?
The passing score for the ISSAP exam is 700 out of 1000 points.
How do I prepare effectively for the ISSAP Certification exam?
To prepare for the ISSAP certification exam:
- Focus on the six key domains.
- Use ISC2 official study guides, practice tests, and online courses.
- Consider InfosecTrain's CISSP-ISSAP training & certification course for structured learning and expert guidance.
- Apply theoretical knowledge to real-world scenarios through labs and case studies.
- Engage in forums and study groups for peer support.
- Review your notes regularly and take mock exams to identify weak areas.


