CompTIA Security+ SY0-601 Domain 3: Implementation

Security+SY0-601 Domains
Security + new exam version is SY0-601. In this new version, we have 5 domains:
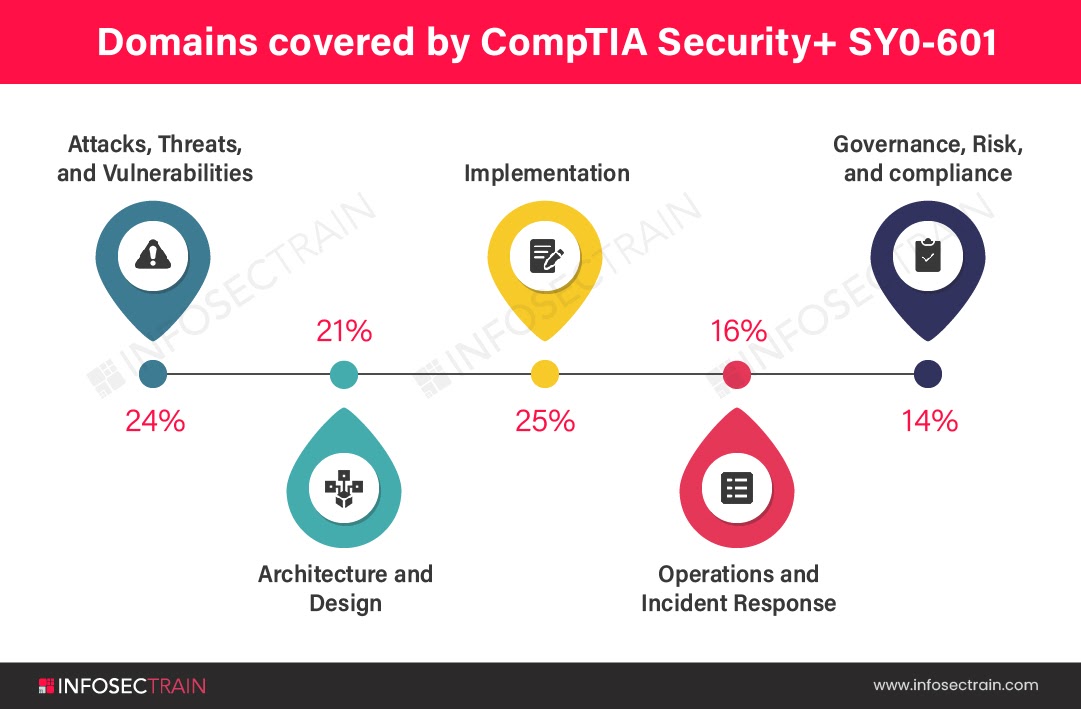
- Domain 1.0: Attacks, Threats, and Vulnerabilities (24%)
- Domain 2.0: Architecture and Design (21%)
- Domain 3.0: Implementation (25%)
- Domain 4.0: Operations and Incident Response (16%)
- Domain 5.0: Governance, Risk, and Compliance (14%)
In this blog, we discuss domain 3.0 Implementation.
Implementation
For a company’s security program, implementation is critical. It is the point at which a security system or technology comes into being, a new security effort is nothing but a collection of thoughts on a document if it isn’t put into action. In this domain, we cover 9 objectives and their subtopics.
The objectives covered in security+ domain 3.0 are listed below.
- Implement Secure Protocols
- Implement Host or Application Security Solutions
- Implement Secure Network Designs
- Install and Configure Wireless Security Settings
- Implement Secure Mobile Solutions
- Apply Cybersecurity Solutions to the Cloud
- Implement Identity and Account Management Controls
- Implement Authentication and Authorization Solutions
- Implement Public Key Infrastructure
1. Implement Secure Protocols
Cyber attackers can take advantage of insecure protocols to damage data security and the integrity of systems. In this lesson, you’ll learn about some of the protocols and services that provide network hosts with addressing, name resolution, and monitoring. These protocols aren’t as visible as apps like web servers and email servers, but they’re essential for securing networks.
This lesson covers two parts: Protocols and Use case. Inside Protocols we learn Domain Name System (DNS), DNS Security Extensions (DNSSEC), Secure Real-time Transport Protocol (SRTP), File Transfer Protocol (FTPS), SSH File Transfer Protocols (SFTP), Understand Simple Network Management Protocol (SNMP) framework, Hypertext Transfer Protocol (HTTP), we can cover email service protocols, secure POP3 (Post Office Protocol v3), Secure IMAP (Internet Message Access Protocol v4). We understand Internet Protocol Security (IPSec) and its 2 Protocols:
- Authentication Header (AH)
- Encapsulation Security Payload (ESP)
In Use case part we learn how security protocols work inside this we cover:
- Voice and Video
- Time Synchronization
- Email and Web
- File Transfer
- Directory Services
- Remote Access
- Domain Name Resolution
- Routing and Switching
- Network Address Allocation
- Subscription Services
2. Implement Host or Application Security Solutions
This lesson is concentrated on which security solutions are implemented for various hosts and applications. Inside this lesson, we cover Endpoint Protection, Boot Integrity, Application Security, Hardening.
In Endpoint Protection we can understand Antivirus and Anti-Malware, NGFW (Next-generation firewall), Host-based intrusion detection system (HIDS), Endpoint detection and response (EDR), Data Loss Prevention (DLP). Boot Integrity covers Boot Security, Unified Extension Firmware Interface (UEFI), work of Measured boot and Boot Attestation.
Inside Application security we learn Input Validation, Secure Cookies, HTTP Headers, we understand Allow list, Block list, Dynamic Code analysis.
3. Implement Secure Network Designs
Networks are as prevalent in the business as computers themselves. As a result, understanding secure network designs is essential for creating a protected network for your company. In this lesson we understand the working of Load balancing, Network segmentation, Virtual local area network (VLAN), we learn the difference between Extranet and Intranet. Cover the working of VPN (Virtual Private Network), DNA, also cover Network access control (NAC), Access control list (ACL). We will also understand the use of Port security.
4. Install and Configure Wireless Security Settings
Wireless security is becoming very important in the field of information security. In this lesson, we learn Cryptographic protocols, WiFi protected Access 2 (WAP2) and WiFi protected access 3 (WAP3), Simultaneous Authentication of Equals (SAE). We also cover Authentication protocols, Extensible authentication protocol (EAP), Protected Extensible Authentication Protocol (PEAP), IEEE 802.1X. We understand the Methods of configuring wireless security and Installation considerations, WiFi Protected Setup (WPS), Site surveys, WiFi analyzers, Wireless access point (WAP) placement.
5. Implement Secure Mobile Solutions
In this lesson, we will understand the concept of Connection methods and receivers. Inside this concept, we cover Cellular, WiFi, Bluetooth, NFC, Infrared, Point to Point, Point to multipoint. We learn Mobile device management (MDM), Application management, Content management, Remote wipe, Geofencing, Screen lock, Biometrics, Storage segmentation. We cover Deployment models, BYOD (Bring your own device), Corporate-owned personally enabled (COPE), Choose your own device (CYOD), Virtual desktop infrastructure (VDI).
6. Apply Cybersecurity Solutions to the Cloud
In this lesson, we will learn the use of Cloud security controls, Cybersecurity solutions, and Cloud-native controls vs third-party solutions. In Cloud Security controls we will cover several sub-topics like High availability across zones, Storage, Network, Compute. And inside Cybersecurity solutions, we cover Application security, Next-generation secure web gateway (SWG), Firewall considerations in a cloud environment.
7. Implement Identity and Account Management Controls
In this lesson, we will learn 3 topics: Identity, Account types, and Account policies. In the first topic Identity, we cover Identity providers (IdP), know about Identity Attributes, how the tokens are used, SSH keys, and Smart cards. In the second topic, we cover types of accounts, User account, Guest accounts, Service accounts. Inside Account policies, we cover Account permissions, Access policies, Password complexity, Time-based logins, Account audits.
8. Implement Authentication and Authorization Solutions
In this lesson, we will learn Authentication management, Password keys, Password vaults, TPM, Knowledge-based authentication. We will cover Authentication/authorization, inside this topic we will understand Challenge-Handshake Authentication Protocol (CHAP), Password Authentication Protocol (PAP), Terminal Access Controller Access Control System Plus (TACACS+), Kerberos, OpenID. We also cover Access control schemes and their subtopics Attribute-based access control (ABAC), Role-based access control, Rule-based access control, Privileged access management, Filesystem permissions.
9. Implement Public Key Infrastructure
In this lesson, we will cover the concept of Public key infrastructure (PKI), Key management, Certificate authority (CA), Certificate revocation list (CRL), use of Certificate attributes, Online Certificate Status Protocol (OCSP), Certificate signing request (CSR). We learn types of certificates, Wildcard, Subject alternative name, Code signing, Domain Validation, Extended validation. We also cover formats of certification and Concepts of certification changing, Key escrow, online vs offline CA.
Learn Security+ With Us
Infosec Train is a leading provider of IT security training and consulting organization. We have certified and experienced trainers in our team whom you can easily interact with and solve your doubts anytime. If you are interested and looking for live online training, Infosec Train provides the best online security+ certification training. You can check and enroll in our CompTIA Security+ Online Certification Training to prepare for the certification exam.




 1800-843-7890 (India)
1800-843-7890 (India) 
