CompTIA PenTest+ Domain 2: Information Gathering and Vulnerability Scanning
Information gathering, also known as reconnaissance, is the first and most important stage in successful penetration testing. It is the process of learning about our target and gathering specific information about it so that we might exploit it in the future. The more helpful information you have on a target, the more likely you are to discover vulnerabilities and more severe issues in the target by exploiting them. The Penetration Tester or Ethical Hacker may not know what to target if no information is gathered. Furthermore, it is vital to perform a vulnerability scan. It evaluates the potential for cybercriminals to exploit security vulnerabilities in IT systems, internal and external networks, communications equipment, and other related resources. CompTIA PenTest+ delves into the information gathering and vulnerability scanning phase of penetration testing in domain 2.

Domains of CompTIA PenTest+:
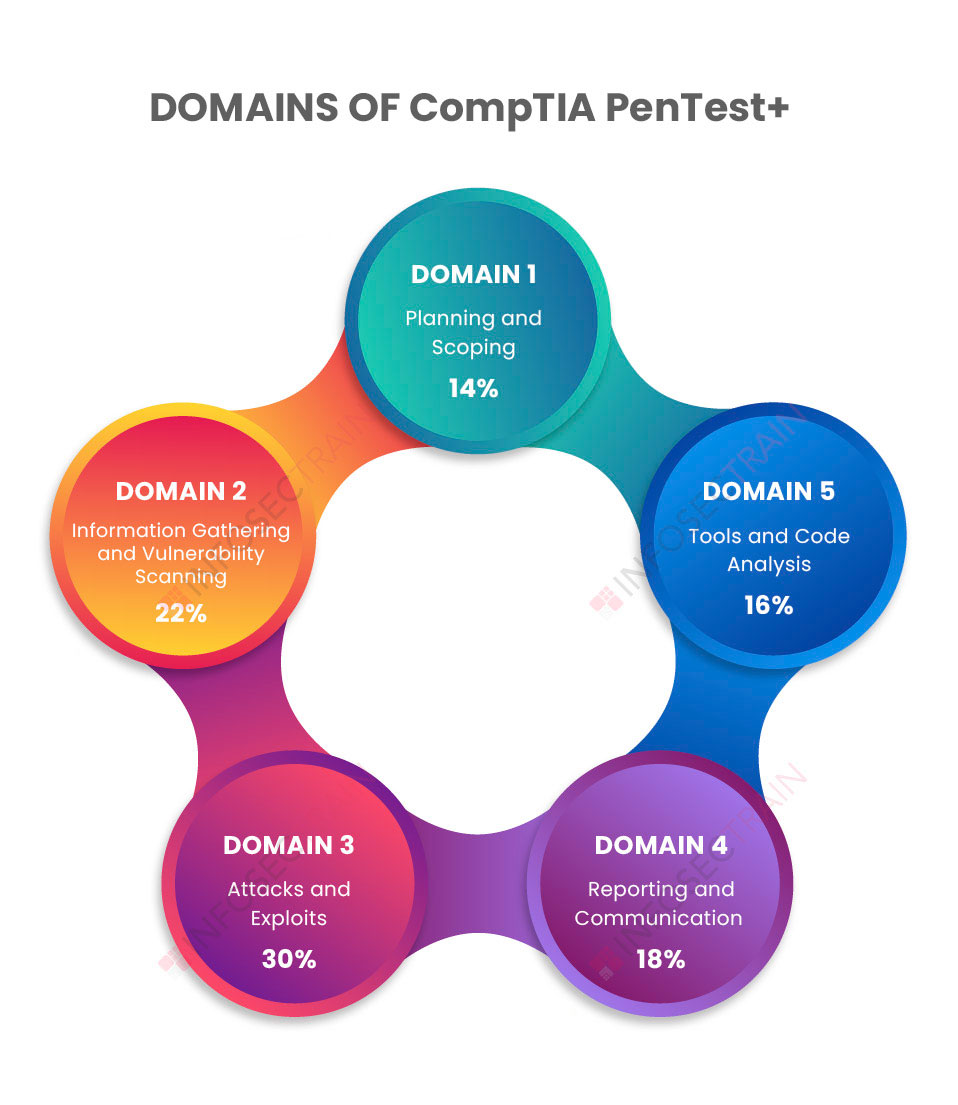
- Domain 1: Planning and Scoping (14%)
- Domain 2: Information Gathering and Vulnerability Scanning (22%)
- Domain 3: Attacks and Exploits (30%)
- Domain 4: Reporting and Communication (18%)
- Domain 5: Tools and Code Analysis (16%)
CompTIA PenTest+ Domain 2: Information Gathering and Vulnerability Scanning
It is the second-largest domain of the CompTIA PenTest+ exam covering a weightage of 22%. The domain goes through the definition of information gathering or reconnaissance in general, as well as the differences between passive and active reconnaissance techniques. It will assist in learning how to obtain publicly accessible or internal information on a target while conducting passive and active reconnaissance, which can be employed in subsequent testing phases. It discusses some of the most commonly used tools and techniques. The domain then goes through the process of vulnerability scanning and how vulnerability scanning tools function, how to assess vulnerability scanning data and turn them into valuable deliverables, and how to leverage the information acquired during the exploitation phase. The domain also goes over some critical issues to keep in mind when running vulnerability scans.
The domain is further divided into four subsections:
- Given a scenario, perform passive reconnaissance
- Given a scenario, perform active reconnaissance
- Given a scenario, analyze the results of the reconnaissance exercise
- Given a scenario, perform vulnerability scanning
1.Given a scenario, perform passive reconnaissance
Passive reconnaissance is a technique of gathering information about targeted IT systems and networks without having to interact with them. It includes the use of publicly available information about the target. Penetration Testers commonly use Open Source Intelligence (OSINT) to collect publicly available information. Anyone with a foundational set of skills can learn about the targets. IP addresses, DNS information, subdomain names, and other forms of information of systems within the organizations are collected using various tools. It can also be used to find out whether a company’s IT infrastructure is cloud-based or self-hosted. It also determines the organization’s technical as well as administrative contacts. Furthermore, it also aids in evaluating whether critical information about an organization has been released through password dumps, files that have been exposed to the public internet by accident, source code repositories, or cached copies of websites.
2. Given a scenario, perform active reconnaissance
In active reconnaissance, a Penetration Tester interacts with the targeted system in order to acquire information about vulnerabilities that are not available through passive reconnaissance. It involves enumeration to identify the target organization’s hosts, users, services, domains, and Uniform Resource Locators (URLs). The section delves into cloud asset discovery, which entails mapping an organization’s complete cloud deployment and third-party hosted services. It also covers how to craft network packets, identify defenses, and other tactics that interact directly with target computers. It also dives into the concepts of website reconnaissance and wardriving.
3. Given a scenario, analyze the results of the reconnaissance exercise
Analyzing the reconnaissance findings is critical because a Penetration Tester must be able to evaluate the results of these tools and utilize them to plan the rest of the engagement. The capacity to obtain meaningful intelligence from the output of reconnaissance tools and procedures is tested in this domain. A fingerprint is a collection of data that can be used to identify software, network protocols, operating systems, and hardware. During reconnaissance, you will learn to use fingerprinting to scan a network to identify the systems operating on it and the same services and applications available on those systems. It will also cover how to assess the output of reconnaissance tools to extract usable intelligence for attack preparation.
4. Given a scenario, perform vulnerability scanning
Vulnerability scanning is finding security weaknesses and vulnerabilities in IT systems and software, and it is a crucial part of the penetration testing process. It covers vulnerability scanning considerations such as scan time, protocols, network topology, bandwidth restrictions, query throttling, unstable systems, and non-traditional assets and how to perform and automate vulnerability scans in various scenarios. It will also cover multiple scanning methods such as stealth scans, Transmission Control Protocol (TCP) connect scans, credentialed vs. non-credentialed, and automated vulnerability testing tools like Nmap.
CompTIA PenTest+ with InfosecTrain
Information gathering and vulnerability scanning are vital steps in the penetration testing process. Without the information about the target, you would not be able to perform penetration testing. InfosecTrain’s CompTIA PenTest+ training course will assist you in acquiring the expertise needed to gather information about the target and perform a vulnerability scan to detect system vulnerabilities the attacker can exploit. Our course also helps you prepare for all the phases of penetration testing. When you complete the course, you will have the skills and knowledge needed for the CompTIA PenTest+ certification in Information Gathering and Vulnerability Scanning.



 1800-843-7890 (India)
1800-843-7890 (India) 
