CompTIA PenTest+ Domain 1: Planning and Scoping
As more businesses move their operations and processes to the digital realm, the risks associated with this technological adoption are increasing. Hackers exploiting a vulnerability in your IT infrastructure after they acquire unauthorized access to it is one of the primary threats.

As a result, businesses require professionals that can comprehend the attacker’s perspective, tools, and strategies and assist them in defending against these risks. For this reason, demand for Penetration Testers and Ethical Hackers has increased significantly. They do penetration testing to find flaws that a malicious attacker could exploit. They assist employees in learning how to deal with any form of harmful entity break-in.
CompTIA PenTest+ is a vendor-neutral intermediate-level certification that verifies your hands-on ability to conduct penetration testing.
In this article, we will cover domain 1 of CompTIA PenTest+, which is “Planning and Scoping.”
Domains of CompTIA PenTest+:
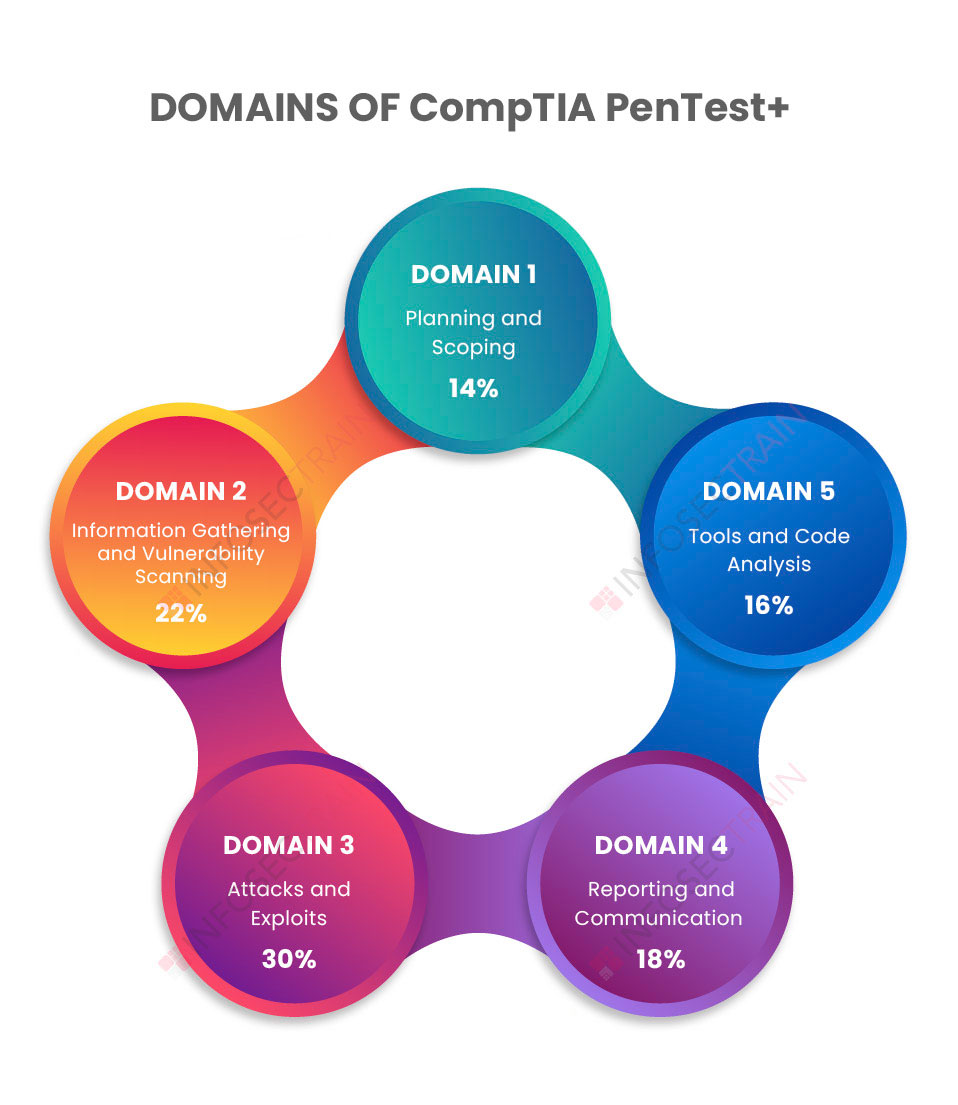
- Domain 1: Planning and Scoping (14%)
- Domain 2: Information Gathering and Vulnerability Scanning (22%)
- Domain 3: Attacks and Exploits (30%)
- Domain 4: Reporting and Communication (18%)
- Domain 5: Tools and Code Analysis (16%)
CompTIA PenTest+ Domain 1: Planning and Scoping
“Planning and Scoping” is the first domain in the CompTIA PenTest+ exam, with a 14% weightage. It must be adequately planned and scoped to guarantee that the organization gets the maximum benefit from penetration testing. If a penetration testing engagement is not adequately scoped and planned, many things can go wrong. As a result, in penetration testing or ethical hacking engagement, the first domain addresses the necessity of excellent planning and scoping. An Ethical Hacker or Penetration Tester must be familiar with local laws and legal principles in order to perform penetration testing. So it covers a number of important legal topics as well as other areas of compliance-based assessment.
The domain is further divided into three subsections:
- Compare and contrast the governance, risk, and compliance concepts
- Explain the importance of scoping and organizational or customer requirements
- Given the scenario, demonstrate an ethical hacking mindset by maintaining professionalism and integrity
1. Compare and contrast the governance, risk, and compliance concepts
The domain covers laws that may impact the assessment process as well as legal considerations around penetration testing contracts. Penetration Testers must be conversant with applicable rules to discover vulnerabilities in an organization’s security measures and compliance strategy. As a result, the section goes into regulatory compliance issues for penetration testing, such as the GDPR and PCI DSS.
It also goes over the many laws that Penetration Testers must follow when operating in a specific jurisdiction. The section also covers legal agreements such as the Non-Disclosure Agreement (NDA), the statement of work, Service-Level Agreements (SLA), and others. Finally, the section goes over the permissions that a Penetration Tester needs to penetrate an organization’s devices and networks.
2. Explain the importance of scoping and organizational or customer requirements
Penetration testing aims to find vulnerabilities or loopholes in the organization’s system, network, data, or users. Penetration testing necessitates an examination of current defenses and security procedures, and it also necessitates a thorough analysis of how various systems, networks, devices, and users interact with one another. As a result, this section goes into the scope and strategy of effective penetration testing. It contains NIST techniques, technological constraints, whether the penetration test will be conducted locally or remotely, the scope of engagement, the type of penetration testing that will be performed, and more.
Permission to undertake a security assessment is required before conducting a penetration test. The section also discusses whether a Penetration Tester may scan or penetrate the cloud environment. As a result, the domain will explain all of the requirements for the target environment, as both the tester and the client should understand the scope and plan for the assessment.
3. Given the scenario, demonstrate an ethical hacking mindset by maintaining professionalism and integrity
The mindset of a Penetration Tester is to consider all of the possibilities in any situation. The ethics of penetration testing are discussed, as well as how to appropriately protect the customer during an engagement. Penetration Testers are responsible for detecting security flaws in a customer’s environment by utilizing cyber threat actors’ tools, techniques, and procedures before they can be exploited in a real-world attack.
As a result, the company must trust the Penetration Tester’s ability to perform and operate legally. Penetration testing teams undertake background checks for this purpose. It also ensures that the Penetration Tester follows a specific scope of engagement, such as detecting criminal activity, immediately reporting breaches and illegal activity, limiting the use of tools to a particular engagement, invasiveness based on scope, and maintaining data or information confidentiality. The penetration test should be carried out as part of a legitimate contract.
CompTIA PenTest+ with InfosecTrain
Planning and scoping are critical elements in the penetration testing process that help a business identify which networks, applications, databases, accounts, people, controls, and assets will be targeted in a particular penetration test and define them for the testers. You would not be able to execute penetration testing without sufficient planning and scoping. The CompTIA PenTest+ training course from InfosecTrain will help you gain the skills you need to become a competent Penetration Tester. In addition, our training will assist you in preparing for all phases of penetration testing. You will have the skills and knowledge required for the new CompTIA PenTest+ certification curriculum once you have completed the course.



 1800-843-7890 (India)
1800-843-7890 (India) 
