Is Red Teaming The Right Career Choice For You?
If a cyberattacker can walk out of the data center with an unencrypted hard drive, even the most up-to-date firewall in the world is worthless. Given this cyber threat landscape, it is critical that businesses have the proper protocols, policies, and processes to keep their data safe, infrastructure robust, and, ultimately, make them resilient. With this in mind, businesses should test their systems and networks to see how vulnerable they are to a successful attack and create a comprehensive information security program to protect their organization before an attacker exploits it. This is where offensive security approaches like Red Teaming come to the rescue. Moreover, this need has surged the demand for Red Team experts in the organizations.

Today, we are faced with a lot of career choices that will have long-term consequences. But is Red Teaming the career for you? In this article, we will explore what Red Teaming is and the benefits of being a Red Team expert so you can decide if this is the career you want to pursue or not.
What is Red Teaming?
Red Teaming is a viable technique for assessing your organization’s security weaknesses. It is based on the idea that mimicking an attacker can help your security team improve their defense. A Red Team, also known as an ethical or white-hat hacker, is a group of people who have been equipped in the art of hacking but utilize their expertise for “good” using Tactics, Techniques, and Procedures (TTPs) used by real adversaries. Their goal is to demonstrate the consequences of successful cyberattacks in order to improve enterprise cybersecurity. This team challenges an organization to enhance its effectiveness by playing an adversarial role or standpoint. The Red Team is generally independent of the organization but can be a part of it.
How is Red Team methodology different from Penetration Testing?
However, Red Teaming is often misinterpreted as Penetration Testing but is primarily different in depth and scope. Penetration Testing aims to find and exploit as many vulnerabilities as possible in a short period, whereas Red Teaming is a more thorough assessment that takes weeks. Red Teaming activities are used to evaluate an organization’s detection and response capabilities as well as to meet specific goals.
How does a Red Team work?
Red Teams work like this; leaders recognize the risk of a cybersecurity breach in their organization. An organization may use a Red Team to reduce risk and find vulnerabilities from an unbiased and adversarial standpoint. Once the Red Team has been formed, they will begin coordinating with the company’s trusted agents. It is now up to the Red Team to put their technical skills to use and exploit the organization’s weaknesses. The Red Team’s primary phases of operation are as follows:
- Perform Reconnaissance: If a thief knows the floor plan and family routine, they will have a better chance to break into the residence. Similarly, the Red Team can get a grasp of the client’s organization through reconnaissance before identifying weak points of access. This initial phase is all about learning the lay of the land.
- Gain Access: A Red Team may plan and execute the best ways to obtain access after they have a sound grasp of their target and the vulnerabilities.
- Enumeration and Escalation: The Red Team evaluates their position about where they want to be once they have gained access. This may necessitate escalation or a higher degree of user access. During this phase, the Red Team conducts reconnaissance from within the network, calculating the optimum network position to achieve their goal.
- Pivot: After gaining a strategic foothold, the team will repeat any or all of the processes to explore and exploit more network nodes in order to move laterally towards vital business assets and their intended objective.
- Persistence: The more skilled an attacker is, the more likely their presence will go undetected. Red Teamers demonstrate their persistence by using non-destructive methods to show they have had access for a long time.
- Evade and Erase: As malware and attackers become more sophisticated and automated, tools and techniques for evading detection become increasingly effective. Malware may frequently detect, defeat, or deceive human and machine-based countermeasures, leaving little to no evidence of its activities. The Red Team imitates similar tradecraft to go undetected and leave minimal forensic evidence. They often blend in with their environment.
- Reporting: Once the Red Team has demonstrated their ability to exploit a security vulnerability in an organization’s security, they complete the operation, restore systems to their previous state, and report their findings and recommendations on how to secure the network in the future better, educating the organization and reducing their cyber risk to business operations.
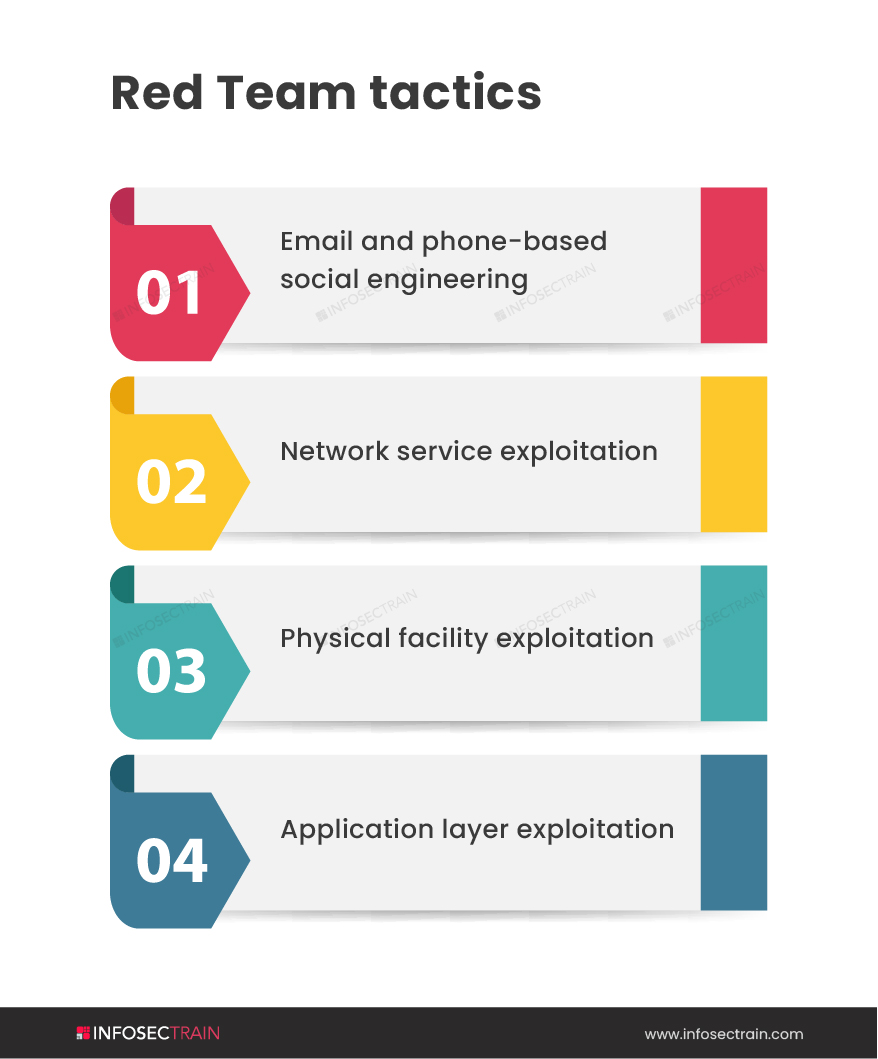
Benefits of Red Team:
Here are some of the benefits of the Red Team assessment:
- They assist in identifying the risk of attack and susceptibility of crucial business information assets.
- They identify vulnerabilities in systems and applications.
- They aid in determining a company’s ability to detect, respond to, and avoid complex and targeted threats.
- They help determine whether an organization is prepared to protect against cyber-attacks by broadening your perspective.
- Genuine threat actors’ Tactics, Techniques, and Procedures (TTP) are effectively simulated in a risk-managed and controlled way.
- They facilitate close collaboration with internal incident response and Blue Teams in order to deliver effective mitigation and detailed post-assessment feedback workshops.
Benefits of being a Red Team expert:
Let us discuss the advantage you will gain as a Red Team expert:
- Career enhancement: The need for professionals who can test an organization’s ability to prevent, detect, and respond to attacks is growing as cyber threats evolve at an unprecedented rate. As a result, the demand for Red Team experts has skyrocketed, allowing you to advance in your offensive cybersecurity career.
- Higher salary: The Red Team experts are paid higher salaries as compared to their peers.
- Opportunity to learn: Being a Red Team expert requires you to be skilled in various offensive security tools and techniques to mimic a real-world cyber-attack. Therefore you can learn a lot to handle security threats as a Red Team expert.
Red Teaming with InfosecTrain
If this career is at the forefront of your mind, InfosecTrain has got you covered. Our Red Team Expert training course is meant to turn you into a powerful Red Team expert who can defend against cyber threats and conduct effective Penetration Testing to detect them. You will learn all of the tools and techniques you will need to become a successful Red Team expert.




 1800-843-7890 (India)
1800-843-7890 (India) 
