Security+ Domain 2: Threats, Vulnerabilities, & Mitigations
The Security+ certification is a globally recognized standard for IT security professionals. The SY0-701 exam focuses on the latest trends and techniques within risk management, threat management, intrusion detection, and risk mitigation strategies.

The CompTIA Security+ exam encompasses several domains, each dedicated to specific security realms:
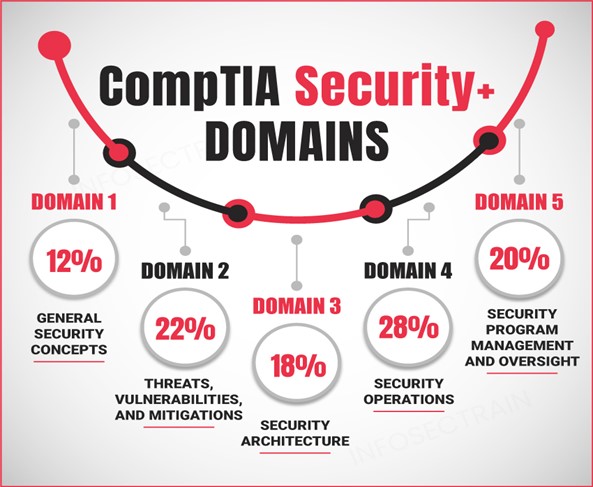
Domain 2 of this exam is particularly crucial, covering various aspects of threats, vulnerabilities, and their mitigation. This blog provides an in-depth exploration of each section within Domain 2:
Domain 2: Threats, Vulnerabilities, and Mitigations
Domain 2 focuses on identifying and understanding the threats and vulnerabilities affecting information systems. It emphasizes the importance of recognizing potential security risks and implementing effective mitigation strategies to safeguard information assets. Let us discuss each section:
2.1: Compare and Contrast Common Threat Actors and Motivations
This section delves into comprehending different threat actors and their motivations, which are crucial for assessing information security risks. It covers identifying and characterizing threat actors like hackers, insiders, nation-states, and cybercriminal groups, exploring motives ranging from financial gain to espionage or disruption.
This section highlights understanding their behaviors, tactics, preferred targets, and potential impacts on organizations. Furthermore, it may explore the psychological and sociological factors behind these threat actors, offering a holistic view for cybersecurity professionals to anticipate and counter diverse cyber threats. Understanding these aspects is pivotal for effective cybersecurity defense strategies.
2.2: Explain Common Threat Vectors and Attack Surfaces
This section focuses on identifying common threat vectors and attack surfaces in cybersecurity. It categorizes threats into various types: message-based threats like email, SMS, and instant messaging, image-based and file-based threats, voice calls, and also threats from removable devices. The section emphasizes risks in unsecured networks like wireless, wired, and Bluetooth, open service ports, and the use of default credentials. It also covers threats from supply chains, including MSPs, vendors, and suppliers.
Furthermore, it delves into human vectors and social engineering tactics like phishing, vishing, smishing, misinformation, impersonation, business email compromise, pretexting, watering hole attacks, brand impersonation, and typosquatting. These categories highlight the diverse and evolving nature of cybersecurity threats.
2.3: Explain Various Types of Vulnerabilities
This section focuses on various cybersecurity vulnerabilities, encompassing application vulnerabilities, emphasizing risks related to software design and implementation. It covers memory injection and buffer overflow threats, illustrating unauthorized data insertion and memory overruns. It delves into race conditions like Time-of-Check (TOC) and Time-of-Use (TOU), exposing simultaneous operation risks. It includes malicious updates, OS-based, web-based, SQL injection, and XSS vulnerabilities, highlighting risks in systems, web platforms, databases, and scripting.
Hardware issues such as firmware, end-of-life, and legacy systems are covered, alongside virtualization concerns like VM escape and resource reuse. This section also covers cloud-specific vulnerabilities, supply chain risks, cryptographic issues, misconfiguration problems, mobile device threats, and zero-day vulnerabilities that conclude the exploration of unknown threats.
2.4: Analyze Indicators of Malicious Activity
In this section, the focus is on identifying signs of security breaches and malicious activities, encompassing various forms of attacks such as malware like ransomware, Trojans, worms, and viruses, physical attacks including brute force and RFID cloning, network attacks like DDoS and DNS attacks, application attacks including injection and buffer overflows, cryptographic attacks such as downgrades and collisions, and password attacks like spraying and brute force.
This section also highlights the importance of recognizing indicators of such activities, which include account lockouts, concurrent session usage, blocked content, signs of impossible travel, unusual resource consumption, resource inaccessibility, out-of-cycle activities, anomalies in logging, published or documented vulnerabilities, and missing logs. This comprehensive overview serves as a crucial guide for professionals in identifying and responding to a wide array of security threats in various environments and their telltale signs to safeguard digital assets and information effectively.
2.5: Mitigation Techniques Used to Secure the Enterprise
Finally, this section focuses on various strategies and techniques to mitigate threats and secure an organization’s assets. This section covers segmentation, which involves dividing the network into smaller parts to limit attack spread and access control, including Access Control Lists (ACLs) and permissions, to regulate who can view or use resources. It involves application allow lists to restrict the software that can run, isolation to separate systems and limit interaction, regular patching to fix vulnerabilities, encryption for data security, continuous monitoring for unusual activity, and adherence to the principle of least privilege, ensuring minimal access rights.
This section also covers configuration enforcement to maintain security settings, decommissioning of outdated systems, and various hardening techniques such as installing endpoint protection, host-based firewalls, Host-Based Intrusion Prevention Systems (HIPS), etc. Understanding these measures can collectively enhance an enterprise’s security posture and help address various potential vulnerabilities and threats.
Conclusion
Domain 2 of the CompTIA Security+ SY0-701 exam is a crucial component for IT professionals. It not only covers the theoretical aspects of cybersecurity threats and vulnerabilities but also focuses on practical strategies for mitigating these risks. Mastery in this field is crucial for IT professionals seeking to secure and defend information systems against the ever-evolving landscape of cyber threats.
Our previous blog thoroughly covered Domain 1 and its subsections. Delve into our blog series to deepen your understanding of Security+.
Master CompTIA Security+ with InfosecTrain
For top-tier online training, consider InfosecTrain‘s CompTIA Security+ certification courses. Our experienced instructors offer rich industry insights, delivering engaging and interactive learning sessions tailored to each individual requirement. Enroll in our CompTIA Security+ certification training program to gear up for the exam. Through our program, participants will acquire valuable insights and practical expertise, empowering them to elevate their careers significantly.
TRAINING CALENDAR of Upcoming Batches For Security+ SY0-701
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 14-Feb-2026 | 29-Mar-2026 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 14-Mar-2026 | 19-Apr-2026 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |
