What is Vulnerability and Control Deficiency Analysis?
Did you know that 92% of malware attacks in 2024 exploited known, preventable vulnerabilities? Or that companies with weak control frameworks face 3x higher breach costs than their proactive peers? Cybersecurity isn’t just about firewalls and antivirus software; it’s a relentless game of cat and mouse where one overlooked flaw can cost millions. Vulnerabilities are the unlocked doors hackers waltz through, while control deficiencies are the broken alarms that fail to sound.

What is Vulnerability?
A vulnerability is any gap in your systems, software, or processes that attackers exploit. These aren’t just technical flaws; human behavior is the #1 vulnerability. For example:
- Software Flaws: These are the classic bugs or errors in code, often cataloged as Common Vulnerabilities and Exposures (CVEs). New CVEs are published at an alarming rate, sometimes every 17 minutes.
- Misconfigurations: Incorrect settings on systems, applications, or network devices. Cloud misconfigurations, for instance, have led to a 75% increase in cloud intrusions. Examples include using default passwords or failing to implement proper access restrictions.
- Design Weaknesses: Flaws inherent in the design of a system or process, such as using weak encryption algorithms or inadequate password security practices. Missing validation checks in web application input fields represent a serious design flaw.
- Process Gaps: Weaknesses in operational procedures. A prime example is letting an essential insurance policy lapse, which can create a financial vulnerability if a related threat occurs. Expired domain names that hackers can purchase also fall into this category.
- Human Error: Actions or inactions by personnel, such as falling for phishing scams, using weak passwords, or failing to apply necessary patches.
Vulnerability Analysis is the systematic method of uncovering these weaknesses before they can be exploited. It’s the proactive reconnaissance mission within an organization’s environment. Key methods employed in vulnerability analysis include:
- Penetration Testing: Simulating real-world attacks to identify exploitable weaknesses, particularly effective for internet-facing systems. This involves Ethical Hackers attempting to breach defenses using techniques similar to those of malicious actors.
- Vulnerability Scanning: Utilizing automated tools (e.g., Nessus) to scan networks, systems, and applications for known vulnerabilities (CVEs), misconfigurations, and missing patches. This provides broad coverage but requires validation to eliminate false positives.
- Continuous Monitoring: Implement systems that constantly track key performance and security metrics on critical servers and applications. This enables the early detection of anomalies or performance degradation that might indicate a security issue, providing highly reliable assessment results for essential systems.
- Code Review/Analysis: Directly examine application source code or binaries to identify security flaws that might not be detected through external scanning or testing.
Not all vulnerabilities are critical. A forgotten test server might rank low risk, while an unsecured database storing credit card data is a ticking time bomb.
What are Control Deficiencies?
While vulnerability analysis identifies the ‘what’ and the specific weakness, control deficiency analysis focuses on the ‘why’. It investigates failures of security controls and the policies, procedures, practices, and technologies designed to mitigate risk. A control deficiency exists when a control is missing, designed improperly, or not operating effectively. It’s the security camera that was never installed, the malfunctioning alarm system, or the security policy everyone ignores. These gaps often fly under the radar until disaster strikes:
- Lack of Multi-Factor Authentication (MFA): 80% of cloud breaches involve compromised credentials (IBM).
- Outdated Access Policies: Employees retain access to systems they no longer use (a goldmine for insider threats).
- Poor Encryption Practices: Storing sensitive data in plaintext, like the 2023 T-Mobile breach, exposing 37 million records.
Control deficiencies are typically categorized based on their origin :
1. Deficiencies of Design: The control is inherently flawed or missing from the outset. Even if implemented perfectly, it wouldn’t effectively prevent or detect a misstatement or security event.
Example: Implementing an access control system that lacks a mechanism for periodic review of access rights, or designing a network segmentation strategy that fails to isolate critical systems adequately.
2. Deficiencies of Operating Effectiveness: A well-designed control exists, but doesn’t function as intended. This often involves human factors, such as personnel not following procedures, a lack of training, or incorrect implementation.
Example: A robust incident response plan (good design), but failing to test it regularly or staff responding too slowly during an actual incident (operating deficiency). Or having a policy for strong passwords, but not effectively enforcing them.
While Design vs. Operating effectiveness are the primary categories based on origin, deficiencies can also be viewed through other lenses, such as :
- Technical: Issues with IT controls (e.g., firewall misconfiguration, backup failures).
- Administrative: Problems with policies, procedures, or management practices (e.g., failing to communicate policy updates).
- Architectural: Flaws in the security infrastructure design (e.g., integration issues).
- Operational: Improper execution of control processes (e.g., delayed incident response).
How to Analyze Control Deficiencies?
The objective of Control Deficiency Analysis goes beyond simply identifying that a control failed; it aims to uncover why it failed. This requires delving into the root cause, preventing organizations from merely treating symptoms while the underlying problem persists. A primary technique for this is Gap Analysis, which systematically compares the current state of controls against the desired or required state.
- Define Control Objectives: Clearly articulate what each specific control is intended to achieve. What outcome signifies success? (e.g., “Ensure timely patching of critical vulnerabilities,” “prevent unauthorized access to sensitive customer data”). This provides a benchmark for evaluation.
- Review Control Design: Examine the documented control design (policies, procedures, system configurations). Does the design, either independently or in conjunction with other controls, appear capable of meeting the defined objective? Could it theoretically prevent or detect the targeted risk? Simulation exercises are employed here.
- Test Control Effectiveness: Assess whether the control operates as intended over a defined period. This involves examining evidence such as system logs, change management records, access request tickets, training completion records, and incident reports. Interviews, surveys, and direct observation of control activity personnel are valuable techniques.
- Analyze Deficiencies: Evaluate any identified gaps between the control’s objective/design and its actual operating effectiveness. Determine the severity and potential impact of the deficiency. Risk matrices can help quantify and categorize the associated risks. Deficiencies might be classified based on their potential impact (e.g., significant deficiency, material weakness) to guide prioritization.
- Document and Communicate: Record all findings, including the controls tested, objectives, methods used, evidence gathered, identified deficiencies, and potential impact. This documentation is crucial for transparency and accountability. Communicate these findings clearly and concisely to relevant stakeholders, particularly senior management, highlighting the criticality of each deficiency.
- Develop Corrective Action Plan: Based on the analysis and communication, management, involving relevant stakeholders, must create a remediation plan. This plan outlines specific steps, assigns responsibilities, identifies necessary resources and budgets, and sets implementation timelines. This step transitions directly into the remediation phase.
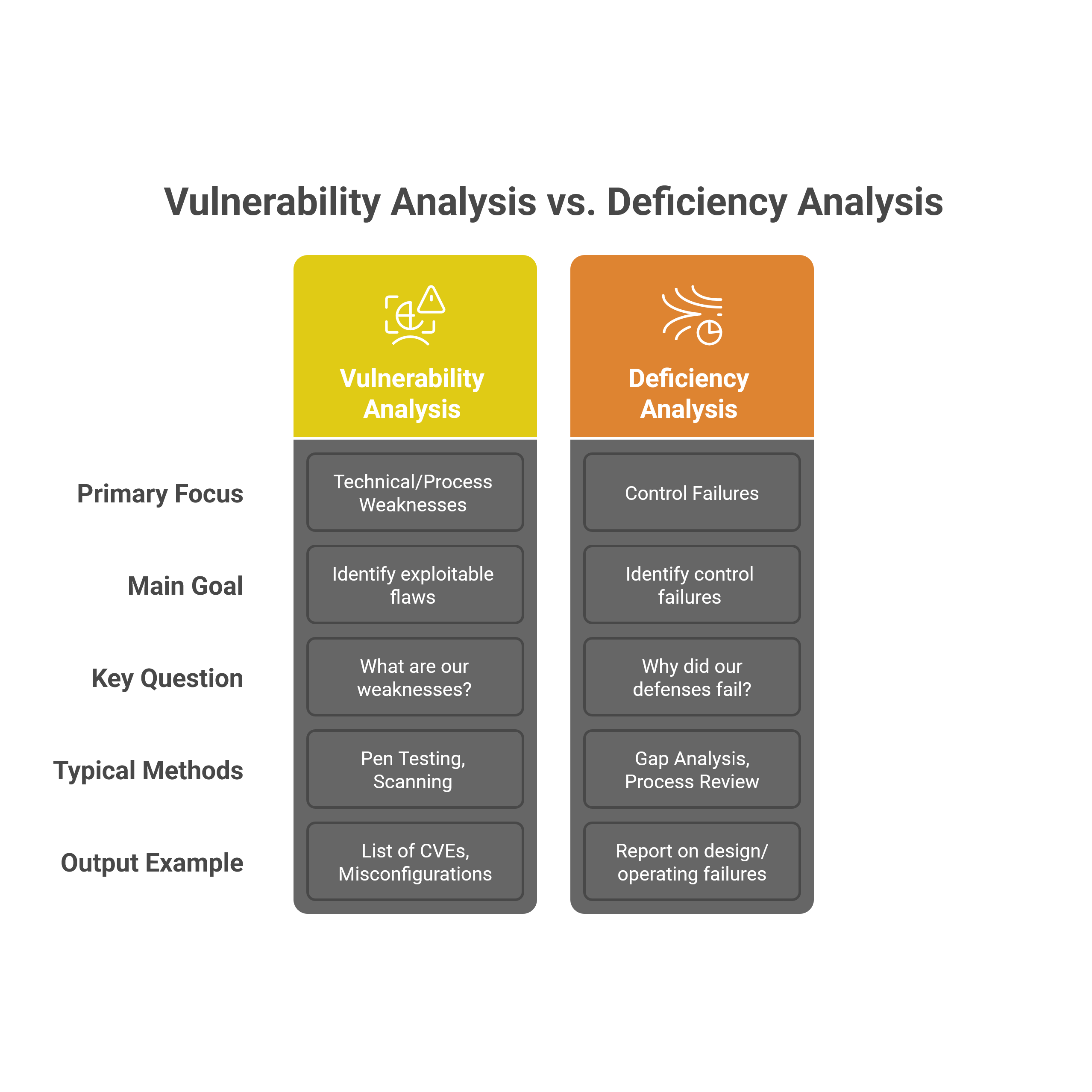
Vulnerability Analysis vs. Deficiency Analysis
CISM Training with InfosecTrain
The key takeaway is clear: Vulnerability Analysis (finding the ‘what’) and Control Deficiency Analysis (understanding the ‘why’) aren’t isolated tasks, but the essential duo for effective risk management. Simply patching vulnerabilities without fixing the flawed controls that allowed them is like bailing water without plugging the leak, a temporary fix at best. Mastering both analyses is fundamental to building lasting security resilience. This strategic insight, moving beyond finding flaws to understanding their root causes, is exactly what InfosecTrain’s CISM Training is designed to instill, equipping you with the skills covered in Domain 2, including Vulnerability and Control Deficiency Analysis.
Ready to shift from reactive fixes to strategic defense? Build the expertise to lead your organization’s security posture. Explore InfosecTrain’s CISM Training today and learn to turn vulnerability insights into fortified defenses!
TRAINING CALENDAR of Upcoming Batches For CISM
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 28-Feb-2026 | 22-Mar-2026 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 28-Mar-2026 | 19-Apr-2026 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 25-Apr-2026 | 17-May-2026 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |

