NIST Approach to Zero Trust
Zero Trust is a modern cybersecurity strategy that operates on the fundamental principle of “never trust, always verify.” It assumes no user, device, or system is inherently trustworthy, regardless of its location within or outside the network. The National Institute of Standards and Technology (NIST) has played a pivotal role in formalizing this approach, particularly through NIST SP 800-207, “Zero Trust Architecture,” which provides a comprehensive framework. Further practical guidance for implementation is provided in NIST SP 1800-35, “Implementing a Zero Trust Architecture,” which guides organizations in adopting this robust security model.

Core Principles/Tenets of NIST Zero Trust
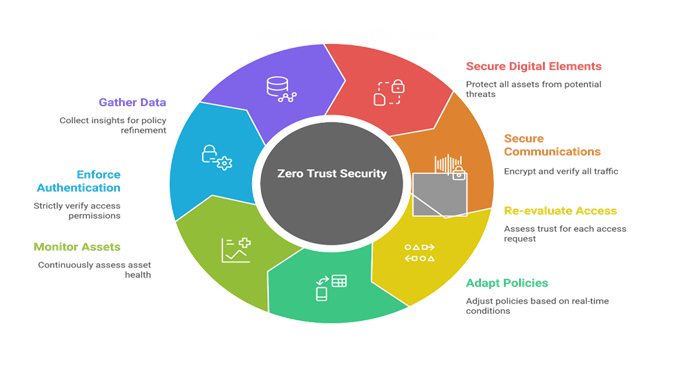
- Every digital element, from user devices to applications and data, is treated as a resource requiring protection. A comprehensive security strategy must cover all these assets, as nothing is trusted by default; everything must be secured and managed.
- All communications are secured, regardless of their location on the network, because network boundaries no longer define trust. Whether traffic is internal or external, it’s considered potentially hostile. Therefore, every single communication must be encrypted and verified, thereby eliminating the concept of implicit trust based on network segments. This approach makes sure security is enforced consistently across your entire IT environment.
- Access to company resources is always temporary and re-evaluated for every new request. Each time a user or device seeks access, a fresh trust assessment is performed, ensuring permissions are tightly controlled and minimizing unauthorized access.
- Resource access is governed by dynamic policies that constantly adapt to real-time conditions. These policies consider factors like user identity, application details, device health, and environmental signals to make granular, adaptive access control decisions.
- Organizations must continuously monitor all their devices, applications, and infrastructure to maintain a strong security posture. It’s vital to constantly assess the health and integrity of assets to spot any potential compromises. This ongoing vigilance is key to a proactive defense.
- All resource authentication and authorization are dynamically and strictly enforced before access is allowed. Before any access is granted, authentication and authorization are rigorously enforced, relying heavily on robust ICAM systems and MFA. No access is permitted without explicit, verified permission.
- Organizations must gather extensive data on the current state of their assets, network infrastructure, and communications. This rich information fuels dynamic policy decisions, helps detect anomalies, and continuously refines the overall security posture. Ultimately, data-driven insights are crucial for evolving defenses.
Components of a NIST-Based Zero Trust Architecture
- Policy Engine (PE): Often referred to as the Policy Decision Point (PDP), this is the central brain of the architecture. The Policy Engine’s sole purpose is to make the access decision—to grant, deny, or revoke access to a resource. It doesn’t enforce the decision itself. Instead, it leverages a dynamic set of policies, user identity, device posture, environmental factors, and threat intelligence to make real-time, context-aware choices.
- Policy Administrator (PA): The Policy Administrator acts as the executor of the Policy Engine’s decisions. It is the crucial communication link that establishes and terminates the path between a user and a resource. The PA’s job is to translate the Policy Engine’s decisions into actionable commands for the relevant Policy Enforcement Points.
- Policy Enforcement Point (PEP): This is the gatekeeper. The PEP serves as the gateway that mediates all access to enterprise resources. It enforces the access decisions made by the Policy Engine, allowing or denying connections based on instructions it receives. The PEP makes sure all traffic to a resource is authenticated and authorized, creating a secure boundary where trust must be continuously verified.
- Identity Management System: Manages user and device identities, credentials, and attributes, providing foundational data for authentication.
- Continuous Diagnostics and Mitigation (CDM) System: Provides real-time, up-to-date information on the security posture and integrity of all enterprise devices and assets.
- Threat Intelligence Feeds: Delivers real-time information on known threats and vulnerabilities, allowing the Policy Engine to make informed risk assessments.
- SIEM System: Aggregates and analyzes security logs and events, helping to identify anomalies and policy violations that could trigger a change in access.
- Data Access Policies: These are the specific, detailed rules and attributes that define what resources a user can access under what conditions.
- Public Key Infrastructure (PKI): Manages digital certificates for secure communication and robust authentication between all components in the architecture.
Steps to Implement Zero Trust with NIST Guidelines
Phase 1: Preparation and Planning
- Define the Protect Surface (Identify Critical Assets): Pinpoint your most crucial data, applications, and services. These “crown jewels” are your primary focus for protection. This helps prioritize what needs the strongest Zero Trust enforcement.
- Understand Current Environment and Map Transaction Flows: Document how users, devices, and applications interact with your critical assets. This mapping reveals existing trust relationships and potential vulnerabilities.
- Establish a Zero Trust Strategy and Roadmap: Outline your Zero Trust vision, goals, and a phased implementation plan. Identify initial, high-impact use cases to start your journey.
Phase 2: Design and Policy Modeling
- Design the Zero Trust Architecture (ZTA): Map out your Policy Engine, Policy Administrator, and Policy Enforcement Points. Integrate existing security tools to support these core components.
- Develop Dynamic, Granular Policies: Create specific, adaptive access policies for each resource. These policies must consider multiple factors beyond just network location.
- Implement Identity and Access Management (IAM) Enhancements: Strengthen identity verification using strong MFA for all critical resource access. Ensure robust identity governance and administration.
Phase 3: Implementation and Enforcement
- Deploy Policy Enforcement Points (PEPs) and Microsegmentation: Implement technologies to control access to resources and segment your network. This limits lateral movement within your infrastructure.
- Enable Continuous Monitoring and Analytics: Deploy tools to constantly monitor user behavior, network traffic, and asset health. Use this data to detect anomalies and policy deviations.
Phase 4: Optimization and Evolution
- Iterate, Pilot, and Expand: Begin with small pilot projects, gather feedback, and gradually scale Zero Trust across your entire enterprise. This allows for continuous learning and refinement.
- Automate and Orchestrate: Integrate your security tools to automate policy enforcement and incident response. Streamline workflows to improve efficiency.
- Continuous Improvement and Adaptation: Regularly review and update Zero Trust policies as threats evolve and your environment changes. Zero Trust is an ongoing process of refinement and improvement.
CCZT Training with InfosecTrain
NIST’s Zero Trust Architecture (ZTA) is a vital, flexible framework for securing today’s digital world. It defends critical assets by emphasizing continuous verification, least privilege, and micro-segmentation, making it a cybersecurity must-have. InfosecTrain’s CCZT Training directly supports this, providing vendor-neutral expertise in Zero Trust concepts and deployment. This course gives professionals practical skills for managing risks and prepares them for the CCZT exam, launching careers aligned with top security standards.
