ISC2 CC Domain 5.5.1: Data Security: Data Handling and Monitoring (Part-2)
Data has become one of the most valuable assets for organizations, driving decisions, innovation, and growth. However, with this increasing reliance on data comes the critical responsibility of ensuring its security. Protecting sensitive information from breaches, leaks, and unauthorized access isn’t just a regulatory necessity—it’s a fundamental aspect of maintaining trust and safeguarding organizational reputation. In this article, we’ll delve into best practices for data handling and monitoring, emphasizing strategies to enhance protection and mitigate risks.

The Data Lifecycle: Creation to Destruction
Data security begins with understanding the data lifecycle—a framework outlining the journey of data within an organization. This lifecycle comprises six key stages: creation, storage, use, sharing, archiving, and destruction. Each stage demands careful consideration of security measures to ensure data remains protected.
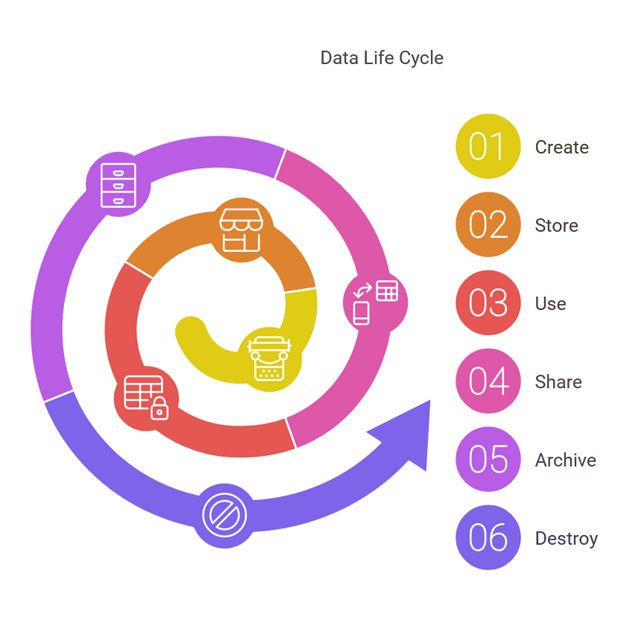
1. Creation: Data creation is the first step in the lifecycle, involving the generation of new information or modifications to existing data. This can occur within on-premises systems, cloud platforms, or hybrid environments. Ensuring secure creation involves:
- Employing robust access controls to limit who can create or modify data.
- Implementing data validation processes to ensure accuracy and integrity during creation.
- Encrypting data at the point of creation to secure it from the outset.
2. Storage: Once created, data moves to the storage stage, where it is retained in one or more storage systems. Whether stored on physical servers, cloud platforms, or external devices, organizations must prioritize secure storage by:
- Encrypting data at rest to prevent unauthorized access.
- Using redundancy and backup systems to protect against data loss.
- Classifying stored data based on sensitivity to determine appropriate security measures.
3. Use: During the use phase, data is actively accessed and processed by users or systems. This stage poses significant security challenges as data is most vulnerable during active use. Best practices include:
- Implementing least privilege access principles to restrict data usage to authorized personnel.
- Monitoring data access logs for unusual patterns.
- Securing endpoints with firewalls, antivirus software, and intrusion detection systems.
4. Sharing: Data sharing allows organizations to disseminate information to stakeholders, whether internally or externally. Secure sharing practices are essential to avoid leaks or breaches:
- Utilizing secure file-sharing platforms with end-to-end encryption.
- Establishing clear data-sharing policies and permissions.
- Employing digital watermarks and access expiration to limit data misuse.
5. Archiving: Data that is no longer in active use transitions to the archive stage. Archiving ensures that data is retained for legal, regulatory, or historical purposes while reducing the risk of unnecessary exposure:
- Developing a data retention policy outlining how long various data types are stored.
- Encrypting archived data and storing it in tamper-proof systems.
- Periodically reviewing archives to ensure compliance with retention policies.
6. Destruction: When data reaches the end of its lifecycle, secure destruction becomes critical. Proper data destruction prevents unauthorized recovery and minimizes the risk of breaches:
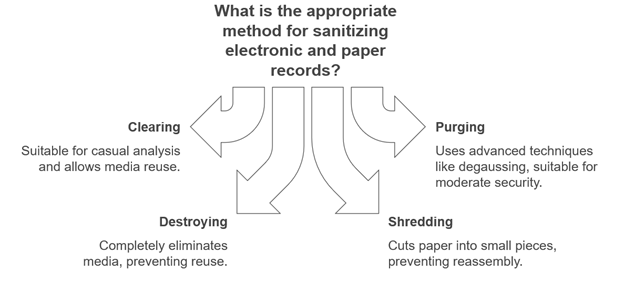
- Following NIST Special Publication 800-88 guidelines for electronic media sanitization.
- Employing methods such as clearing, purging, and destroying based on data sensitivity.
- Shredding or pulping paper records to prevent reconstruction.
Data Destruction Process:
Data Classification: Understanding Sensitivity and Impact
Effective data handling requires a robust classification framework to categorize information based on its sensitivity and criticality. This classification not only determines the security measures applied but also ensures that sensitive data is handled appropriately.
Classification Levels
Organizations may adopt classification schemes tailored to their needs. Common examples include:
- Highly Sensitive: Critical business data, Personally Identifiable Information (PII), and financial or health records.
- Sensitive: Internal communications, proprietary research, and customer information.
- Internal: Operational data that is not intended for public consumption.
- Public: Non-sensitive data available for public use.
Labeling and Awareness: Labeling classified data ensures that users recognize its sensitivity and handle it accordingly. Organizations should implement standardized labeling systems, such as digital tags or metadata, to indicate data classification levels. This practice mitigates accidental exposure or misuse.
Monitoring and Logging
Monitoring activities across data systems is essential for detecting and responding to security incidents. By leveraging robust logging and monitoring mechanisms, organizations can maintain a comprehensive view of data activity and quickly address potential threats.
Logging: Logs serve as detailed records of system activities, providing critical insights into user actions and system events. Effective logging ensures:
- Accountability: Logs attribute actions to specific users, systems, or devices.
- Traceability: Administrators can track related events to understand the full scope of an incident.
- Auditability: Logs serve as evidence for compliance audits or forensic investigations.
Log Monitoring and Analysis: Manual log reviews are often impractical due to the sheer volume of entries. Instead, organizations utilize Security Information and Event Management (SIEM) systems to streamline the process. SIEM systems provide:
- A centralized repository for log entries, ensuring data integrity.
- Artificial intelligence-driven analysis to detect patterns indicative of malicious activity.
- Real-time alerts for immediate response to security events.
By correlating data across multiple systems, SIEMs offer a holistic view of security incidents. For instance, a SIEM might identify a coordinated attack by combining data from intrusion detection systems, firewalls, web servers, and routers.
Building a Secure Data Ecosystem
To maintain robust data security, organizations must adopt a proactive and layered approach that integrates handling and monitoring practices. Key recommendations include:
- Enforce Comprehensive Data Policies: Organizations should develop and enforce policies covering data handling, retention, classification, and destruction. These policies must align with regulatory requirements and industry standards.
- Train Employees: Employee awareness is vital for effective data security. Regular training ensures that staff understand their roles in safeguarding data, recognizing threats, and adhering to best practices.
- Leverage Automation: Automation enhances efficiency and reduces human error in data security processes. From automated data classification tools to AI-powered log analysis, technology can bolster security efforts.
- Conduct Regular Audits: Periodic security audits help identify vulnerabilities and ensure compliance with policies. Audits should evaluate both technical controls and procedural practices.
- Partner with Experts: Organizations lacking internal expertise can collaborate with third-party vendors for secure data destruction, log analysis, and incident response.
CC Training with InfosecTrain
Data security is a continuous effort that demands strategic planning, robust monitoring, and a thorough understanding of the data lifecycle. By securing data from creation to destruction and employing advanced tools like SIEM systems for monitoring, organizations can effectively safeguard their assets and maintain stakeholder trust. Investing in comprehensive cybersecurity training ensures that professionals stay equipped to address evolving threats, fostering a secure and resilient environment.
Elevate your cybersecurity expertise with InfoSecTrain’s Certified Cybersecurity (CC) training. Gain practical skills in data handling, monitoring, and risk management to become a leader in securing organizational data. Enroll today to build your defense against tomorrow’s cyber threats!
TRAINING CALENDAR of Upcoming Batches For
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 09-Feb-2026 | 19-Feb-2026 | 20:00 - 22:00 IST | Weekday | Online | [ Open ] | |
| 09-Mar-2026 | 19-Mar-2026 | 20:00 - 22:00 IST | Weekday | Online | [ Open ] |
