ISC2 ISSAP Domain 1.1.2: Architecting for Governance, Risk, and Compliance (GRC)
Risk is the language of business, and as a Cybersecurity Architect, you must speak it fluently. ISSAP Domain 1 dedicates a whole subdomain (1.2) to managing risk. Recognizing that technical savvy alone is insufficient, you need to quantify and navigate uncertainties in pursuit of business objectives. This section of ISC2 ISSAP Domain 1.1.2: Architecting for governance, risk, and compliance (GRC) carries a hefty weight in the exam and even more in real-world impact. As the global average data breach cost hit $4.88 million in 2024, it was the highest ever. Ransomware, supply chain attacks, and zero-day exploits are evolving, and organizations are under pressure to proactively anticipate and mitigate these risks. So, how does a Security Architect approach risk?

Identify Key Assets, Business Objectives, and Stakeholders
Why Risk Management Matters for ISSAP Candidates?
The ISSAP is not just about encryption protocols or network zones. It is about aligning security with business goals. Domain 1.2 dives deep into how Security Architects manage risk, not just technically, but strategically.
Risk is not a one-time checklist. It is a continuous cycle:
- Identify the risks
- Assess their impact and likelihood
- Treat them effectively
- Monitor and report continuously
This framework is echoed by NIST’s Risk Management Framework (RMF) and ISO 31000. You would not need to memorize every step, but you should absolutely demonstrate a systematic, business-aligned mindset.
Exam Tip: Expect scenario-based questions. You may be asked to assess a risk situation and recommend the most appropriate treatment (mitigate, transfer, accept, avoid). Know the differences and when each makes sense.
Identifying and Classifying Risk
The ultimate truth about the risk is that you can not manage what you do not see. Risk identification is the first step in turning chaos into clarity. As a Security Architect, this is not something you do alone. You will collaborate across teams, study system diagrams, comb through incident logs, and uncover blind spots others missed. Look at it holistically:
- Natural risks: floods, fires, earthquakes
- Human threats: hackers, insider abuse, human error
- Technical failures: crashes, misconfigurations
- Strategic risks: reliance on third-party vendors
- Regulatory risks: new laws, compliance changes
Ask: “What could threaten the confidentiality, integrity, or availability of our critical assets?” That one question alone can lead to a goldmine of insights.
Classification helps bring order to your list. You might group risks by:
- Type (operational, compliance, reputational)
- Source (internal vs. external)
- Affected asset (data, uptime, customer trust)
Assessing Risk
After you identify risks, it is time to assess them. This is where you prioritize. Not every risk deserves equal attention; as an Architect, your job is to spotlight what matters most.
1. Qualitative Assessment
This is your bread and butter for most organizations. You assign values like High/Medium/Low for:
- Likelihood: How likely is it to occur?
- Impact: What damage would it cause?
Then, you plot them on a risk matrix (a heatmap). Those in the top right (high impact, high likelihood)? Deal with them first.
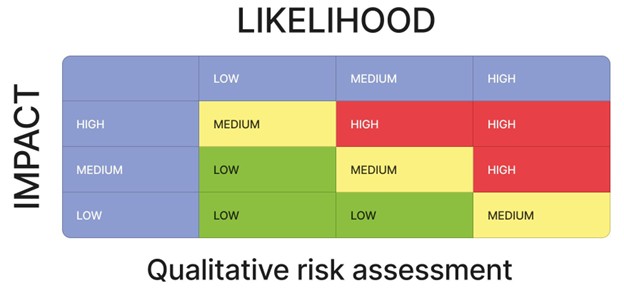
Exam Tip: Understand what a risk matrix, risk appetite, and risk register are. These terms may come up directly in questions or scenario prompts.
2. Quantitative Assessment
Here is where you use numbers. For example:
ALE (Annualized Loss Expectancy) = SLE × ARO
- SLE = Single Loss Expectancy (e.g., $1M)
- ARO = Annual Rate of Occurrence (e.g., 0.5 times/year)
- So ALE = $500K
Quantitative assessments shine when making big-dollar decisions, like buying cyber insurance or investing in disaster recovery systems.
Advise Risk Treatment (e.g., Mitigate, Transfer, Accept, Avoid)
Now comes the decision point. What do you do about each risk? The exam (and the boardroom) expects you to know the four core options:
Mitigate
This is the most common strategy. Reduce either the likelihood or impact using controls like:
- Firewalls
- Encryption
- MFA
- User training
- Incident response planning
Exam Scenario: If the risk is “unauthorized access to data,” a strong mitigation might be “Implement RBAC (Role-Based Access Control) and audit logging.”
Transfer
Shift the financial burden to another party. Like:
- Cyber insurance
- Cloud service providers
Remember: you can transfer responsibility, not accountability.
Accept
Sometimes, you accept a risk if:
- It is within your organization’s risk appetite
- Mitigation is not cost-effective
Always document and justify this.
Pro Tip: If the cost of fixing a $20K risk is $100K, acceptance may be the smartest play.
Avoid
Stop the risky activity altogether. Example:
- Do not collect sensitive data that you can not protect
- Retire vulnerable legacy systems
Avoidance is bold, but sometimes necessary when risks are too big to bear.
Monitoring and Reporting
Risk management does not end with treatment. If you are not monitoring, you are drifting blind.
Here is what continuous monitoring looks like:
- Track Key Risk Indicators (KRIs) (e.g., number of phishing clicks, login failures)
- Regular audits and vulnerability scans
- Access reviews to prevent privilege creep
- Real-time incident response dashboards
And do not forget: reporting matters. CISOs and execs need updates, especially on high-impact risks.
Exam Insight: Expect to be asked how you’d monitor a specific risk. Example: “We mitigated phishing risk with user training. How will you track its effectiveness?” A good answer? “Monitor click rates on simulated phishing tests.”
Design for Auditability
Being compliant means proving compliance. Systems must be audit-ready, producing traceable, tamper-evident records accessible during audits or investigations. Key Design Considerations:
- Centralized logging of critical events: logins, data access, changes, transactions
- Use a SIEM to aggregate, retain, and analyze logs
- Implement role-based access control and segregation of duties
- Use immutable audit trails or append-only logs
- Enable compliance reporting: e.g., access reviews, key rotations, backup tests
- Prepare documentation: network diagrams, data flows, and incident records
In high-assurance environments, consider hardware security modules or formal verification for critical functions.
Coordinating with External Entities and Stakeholders
Security is not managed in isolation; effective external coordination is essential during incidents, audits, or compliance checks.
- Law Enforcement and Regulators
- Incident response plans should define when/how to notify authorities
- Ensure systems preserve logs and evidence for investigations
- Align with breach notification laws (e.g., GDPR’s 72-hour rule
- Public Relations (PR)
- PR manages breach communication; Architects must enable transparency
- Provide plain-language technical explanations for public statements
- Avoid disclosing sensitive data, but assure stakeholders with facts
- Independent Assessors
- Support audits, pen tests, and certification processes
- Grant read-only access to evidence and scope engagements responsibly
- Schedule regular third-party reviews to identify gaps and boost maturity
Explore Domain 1 Articles Here:
ISSAP Training with InfosecTrain
Mastering Domain 1.2 is not just about acing an exam; it is about future-proofing your role as a Cybersecurity Architect. You’ve now learned how to identify, assess, treat, and monitor risk in ways that influence real business decisions. That is not just technical expertise; it is leadership.
And here is the good news: you do not have to navigate this journey alone.
InfoSecTrain’s ISSAP Training Course is built for professionals like you
Led by industry veterans, our ISSAP course goes beyond theory to help you:
- Break down complex risk frameworks into actionable strategies
- Analyze real-world case studies aligned with exam scenarios
- Build confidence in applying concepts like risk appetite, ALE, and continuous monitoring
- Prepare for the exam with expert guidance, mock questions, and study plans
- Elevate your career by thinking like a strategic security leader, not just an implementer
Whether you are planning to sit for the ISSAP exam or want to become your organization’s go-to risk expert, our course is your launchpad.
Ready to think like a risk-savvy Architect and stand out in your field?
Join InfoSecTrain’s ISSAP Online Training & Certification Course today and start building secure, resilient systems that align with real business needs.
TRAINING CALENDAR of Upcoming Batches For
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 07-Feb-2026 | 21-Mar-2026 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |
