CERTIFIED SOC ANALYST (CSA) Certification Training in Delhi
 Read Reviews
Read Reviews
Certified Security Analyst Certification will help you to start your journey towards joining a security operations centre (SOC).SOC Analyst Certification aims at offering proficiency in performing entry-level and intermediate-level operations and therefore, it is helpful for both already existing as well as aspiring Tier I and Tier II SOC analysts.
Enroll now for this course! We are offering access to Cyber Security Fundamentals (19hrs on-demand video) & Microsoft AZ-900 (6hrs on-demand video) Self-Paced Online Programs for ABSOLUTELY FREE



 5th Sep: Weekend
5th Sep: Weekend 


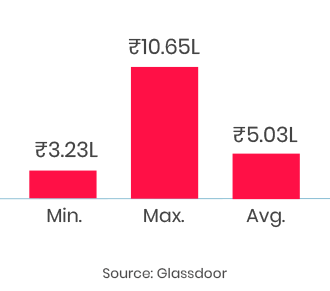

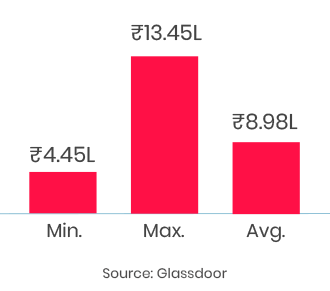


 Quality training sessions. very engaging and challenging for new learns like me. I appreciate Mr. Karan Srivastava for his patience and support throughout the Workshop.
Quality training sessions. very engaging and challenging for new learns like me. I appreciate Mr. Karan Srivastava for his patience and support throughout the Workshop. 






