Why Choose Threat Hunting Course With InfosecTrain?

Table of Contents
What exactly is Threat Hunting?
What is Threat Hunting with InfosecTrain?
Threat Hunting Course content
Threat Hunting Career benefits
What exactly is Threat Hunting?
The process of “threat hunting” involves looking for cyberthreats that are hidden but present in the network, datasets, and endpoints. It is necessary to have a thorough investigation of the surroundings in order to find the malicious hackers.
Threat hunting is critical to avoid exploitation of digital assets. Attackers or hackers can stay within the network for months without being detected, silently collecting data login credentials and gathering your confidential information.
TRAINING CALENDAR of Upcoming Batches For Threat Hunting
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 27-Apr-2024 | 02-Jun-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |
In order to complete the threat hunting process successfully, you must follow the mentioned steps:
1. The Trigger: When sophisticated detection tools notice odd actions that could suggest malicious activity, a trigger directs threat hunters to a particular machine or network area for additional study. A concept about a new threat is frequently the catalyst for proactive hunting. For instance, a security team might look for emerging threats that evade existing protections using fileless malware technologies.
2. Investigation : During the investigative phase, the threat hunter uses technology like EDR (Endpoint Detection and Response) to thoroughly examine a system’s potential for malicious compromise. The inquiry will continue until the activity is determined to be non-malicious or a thorough understanding of the malicious behavior is created.
3. Resolution: Operations and security teams use malicious activity intelligence during the resolution phase to respond to the incident and mitigate threats. Data collected from both malicious and benign activities can be used to improve automation technology’s effectiveness without the need for further human intervention.
Cyber threat hunters perform this process to learn about attackers, methods, and goals. Also, they use collected data to learn about an organization’s security environment, make predictions to enhance security in the future, and eliminate current vulnerabilities.
What is Threat Hunting with InfosecTrain?
Grab the Threat Hunting Training at Infosectrain to gain a thorough understanding of Threat Hunting tactics and the role of Threat Hunters. Our course is designed to teach you the fundamentals of Threat Hunting procedures and prepare you to pass the Cyber Threat Hunting Professional examination.
Over time, threat hunting and incident response approaches have improved. Advanced methodologies are being used by organizations to identify risks by using professional threat hunters even before damage or loss occurs. Our Threat Hunting Professional Online Training Course enhances your abilities and assists you in comprehending threats and their goals.
Threat Hunting Professional is an online training course created by InfosecTrain that teaches you how to seek risks proactively and become a better-balanced penetration tester. Our skilled educators will teach you the fundamentals and procedure of threat hunting, as well as step-by-step instructions for hunting for threats across the network.
Threat Hunting Course content
With the Threat Hunting course at InfosecTrain, you will understand the following.
Threat Hunting Terminology
Here are a few common Threat Hunting Terminologies:
SOC (Security Operation Center)
A Security Operation Center inside an organization (or occasionally outsourced) typically runs 24 hours a day, seven days a week, to monitor security alerts and frequently respond to security events. Like Malware Analysts or Forensic Investigators, subject matter professionals may be included in advanced SOCs.
Managed Detection and Response
An MDR is a managed service that detects and responds to attacks and is delivered by a third party. MDR is sometimes compared to EDR, but while EDR is merely a software tool, MDR uses humans who may be using EDR and network sensors, log sources, and other data sources.
An Indicator Of Compromise (IOC)
An indicator with a high degree of certainty can indicate a breach or a piece of malware. Hashes, IP addresses, URLs, and filenames are examples of IOCs.
Threat Hunting Hypothesis
A threat search hypothesis is a hypothesis or proposed explanation based on minimal information from a secure environment, and it is then used as a jumping-off point for further inquiry. A threat hunt hypothesis is a statement of a notion or explanation to test against facts, similar to a scientific hypothesis.
Endpoint Hunting
Endpoint threat hunting entails using software (agents) placed on each endpoint to detect threats and collect data. Antivirus and more advanced endpoint detection and response software are examples of this.
Alongside you can also learn many interesting concepts like web hunting, malware hunting, hunting with ELK, and many more. Enroll in our course today to get the utmost knowledge.
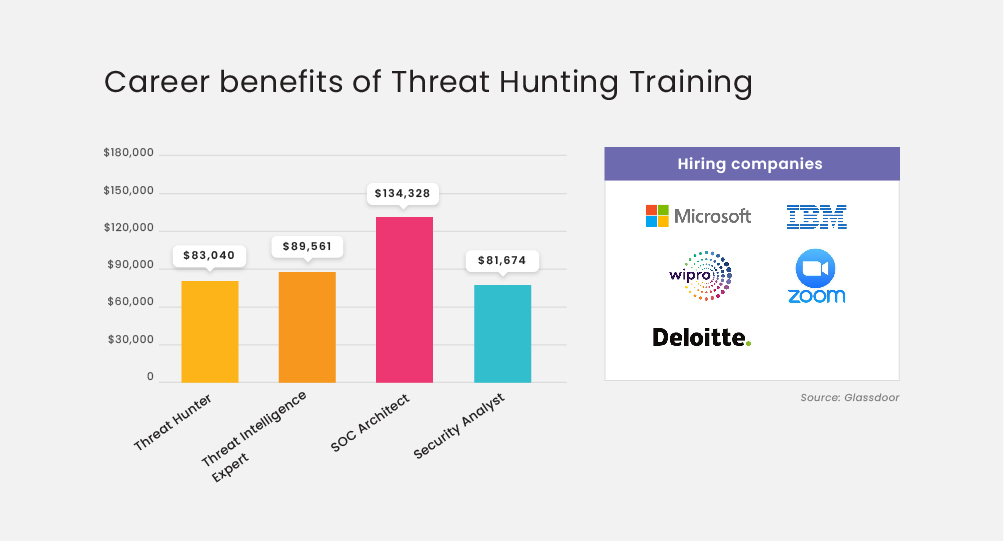
Threat Hunting Career benefits
Threat Hunter
A threat hunter is someone who is constantly looking for, analyzing, and combating advanced threats. Detecting vulnerabilities and reducing the related cybersecurity risk before they harm the organization is part of the job description. He also organizes and evaluates the data gathered to identify trends in the organization’s security environment.
Threat Intelligence Analyst
Threat intelligence Analysts will work for Cyber Intelligence Analysts to reduce potential data risks and defend data. They also generate reports that show how their companies can recognize and prepare for future dangers.
SOC Architect
The responsibilities of a SOC Architect include gathering requirements and needs, studying new features, conducting feasibility studies for those features, specifying SOC level requirements and use cases, defining content for different development steps, and setting priorities.
Security Analyst
Systems and networks are monitored by Security Analysts, whose responsibility is to install, manage, and update the software. These analysts ensure the network is protected from malicious software by installing adequate security measures. Depending on the strength of the network they work on, analysts may compile ongoing reports on its safety.
Why Choose InfosecTrain for Threat Hunting?
InfosecTrain is a leading security and technology training and consulting firm that specializes in a wide range of IT security and information security services. Customers all over the world benefit from InfosecTrain’s comprehensive training and consulting services. Whether technical services, certification, or bespoke training are required, InfosecTrain consistently provides the highest quality and highest success rate in the market.
- We provide comprehensive certification training.
- We have certified and highly competent trainers with in-depth subject expertise.
- Our training timetable is flexible, and we also offer lecture recordings.
- We provide post-training assistance.
- We also have an interactive Q&A session planned.
So if you are interested in learning Threat Hunting, do check out our website.
TRAINING CALENDAR of Upcoming Batches For Threat Hunting
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 27-Apr-2024 | 02-Jun-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |




 1800-843-7890 (India)
1800-843-7890 (India) 
