What is the Cyber Kill Chain Process?
In the last few years, there has been an increase in Advanced Persistent Threat (APT) actors trained to perform MITRE intrusion campaigns aimed at stealing sensitive economic and national security data. Organizations require a method to safeguard systems or networks from APTs and other significant attacks. So, Lockheed Martin created a Cyber Kill Chain process for detecting and preventing cyber intrusion attacks from keeping track of such attacks. Many businesses employ the Cyber Kill Chain approach to protect themselves against data breaches and phishing attempts.

Table of Contents
What is a Cyber Kill Chain?
Phases of Cyber Kill Chain process
Cyber Kill Chain’s Importance in Cybersecurity
In this article, we will look at what a Cyber Kill Chain is and how Cyber Kill Chain works.
What is a Cyber Kill Chain?
Cyber Kill Chain is a concept that allows the organization to understand how an attacker intends to penetrate or destroy the target’s system or network. It also helps businesses understand how to protect, detect, respond to, and locate an attacker’s techniques or strategies for infiltrating target systems. The term “Kill Chain” comes from the military and refers to the method that an enemy uses to strike a target. The Kill Chain method identifies seven steps that an attacker goes through, each of which provides an opportunity to detect and react, that covers:
- Identification of the target
- Force dispatch toward the target
- Attacking the goal decision and order
- Destruction of the target
Phases of Cyber Kill Chain process
Phases of Cybersecurity Kill-Chain process is divided into seven parts, each of which is explained in detail below.
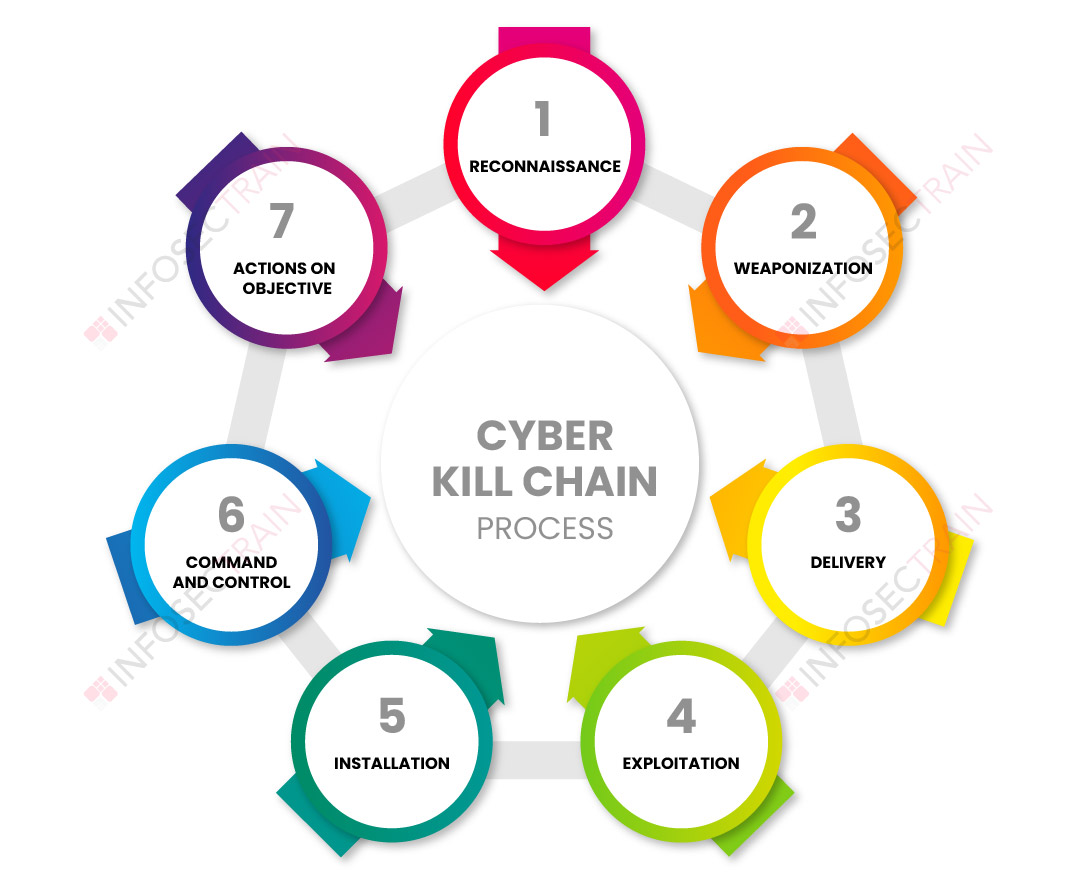
1. Reconnaissance
This phase is also known as observation. During this phase, the organization does research, crowdsourcing, and internet scanning for data and information about the target, such as harvesting email, confidential data, and so on. It then selects those targets whose networks may be compromised. The attacker also determines open ports, firewalls, honey ports, services, vulnerable operating systems, etc., before launching an attack on the target system. This phase is split into two sections:
Active Reconnaissance: It collects information on current security software finances, such as email addresses and social media account information, and uses tools like Nmap, vulnerabilities scanner, and port scanning to locate possible targets.
Passive Reconnaissance: It gathers information on a company’s IT infrastructure to uncover network weaknesses via websites, news articles, job postings, and social media activity, among other things.
Preventive measures:
- Create a web analytic strategy that works
- Prioritized defenses centered on a specific technology
- Invest in a security awareness program
2. Weaponization
In this phase, the attacker creates cyber weapons such as malware and payloads by employing sophisticated tactics to exploit the flaws. Payloads are developed based on vulnerabilities discovered during the reconnaissance phase. Metasploit, burp suite, sqlmap, and social engineering techniques like phishing are among the tools needed to create payloads and malware.
Preventive measures:
- Analyze malicious files and metadata to gather threat intelligence
- Detection systems for weapons are being built
- Discover weaponized artifacts
3. Delivery
In this phase, the attacker uses phishing emails, social media accounts, compromised websites, USB devices, and other methods to transfer weaponized malware and payloads produced in the previous stage to the target machine. The most cost-effective technique of delivering harmful files to the target has been through emails. The security personnel must intervene at this critical time to prevent the attack.
Preventive measures:
- Examination of the delivery medium for comprehending the effects of target systems
- Detecting new malicious payloads at the point of delivery using weaponized artifacts
4. Exploitation
In this phase, the intruder code is triggered and performed in each application on the target system or network after the malicious payload is successfully delivered to the target computer, allowing the attacker access. And the vulnerability can be exploited by SQL injection, brute force attacks, JavaScript, and other methods.
Preventive measures:
- Provide Web developers with secure coding training
- Scanning for weaknesses and penetration testing should be performed regularly
5. Installation
Once the target machine has been successfully exploited for vulnerabilities, another malware software is installed for higher privileges. Malware also establishes a new backdoor or remote access Trojan that performs malicious activity on target systems and grants access to the intruder.
Preventive measures:
- Changing or obstructing conventional installation routes
- Understanding how to detect if malware is old or new by looking at its compile time
6. Command and Control
When malware is installed, the attacker gains access to the compromised system, allowing them to command and control it. Attackers acquire access to privileged accounts and use brute force attacks, password searches, and permission changes to obtain control. After that, a channel is established between the attacker and the target, via which they can interact and exchange files. This phase is the security team’s last chance to stop the operation before the attacker begins to execute the commands.
Preventive measures:
- Prevent name server poisoning and DNS sink holding.
- Block uncategorized domains with technology such as DNS filtering.
7. Action on object
When attackers gain continued access to a target, they proceed to achieve goals and objectives such as data exfiltration, theft, and destruction and breach the system to steal user credentials, among other things.
Preventive measures:
- Detects data leakage, lateral movement, and the use of illegal credentials.
- All alerts receive immediate analyst attention.
Cyber Kill Chain’s Importance in Cybersecurity
- Threat intelligence techniques can detect attackers at any step of the threat lifecycle.
- Prevent unauthorized users from gaining access.
- Stop unauthorized users from sharing, saving, altering, exfiltrating, or encrypting sensitive data.
- Real-time response to attacks.
- Stopping an attacker’s lateral movement within the network.
How can InfosecTrain help you?
The Cyber Kill Chain is mainly utilized for defense purposes. Enroll in InfosecTrain‘s MITRE ATT&CK training and certification course to advance your cyber security knowledge and learn how to defend against various cyber threats. In the MITRE ATT&CK training course, you will learn the Cyber Kill Chain process in detail.




 1800-843-7890 (India)
1800-843-7890 (India) 
