What are the Essential Pillars of Cyber Security?
Cyber security is a significant concern for everyone, regardless of a business, an organization, or an association. Cyber security has become a major concern for businesses to protect their sensitive and confidential information from attackers. We became more reliant on technology to leverage hassle-free services online, such as AI, IoT, and cloud services, which resulted in many new security vulnerabilities that didn’t exist earlier. Many security principles, protocols, and guidelines are defined to protect the organization from cyber-attacks.

Organizations have their inbuilt strategies to combat cyber attacks. The Australian Cyber Security Center (ACSC) has recommended the most effective mitigation strategy, known as the ‘Essential Eight.’ This article is focused on providing comprehensive details of the Essential Eight pillars of cybersecurity that helps to protect your business.
What is the Essential Eight?
Essential Eight is an effective mitigation strategy introduced by the Australian Signals Directorate (ASD), which aims to protect organizations from cyberattacks. It is a multi-layer approach considering the maturity level to customize the Essential Eight strategy in the organization’s risk profile.
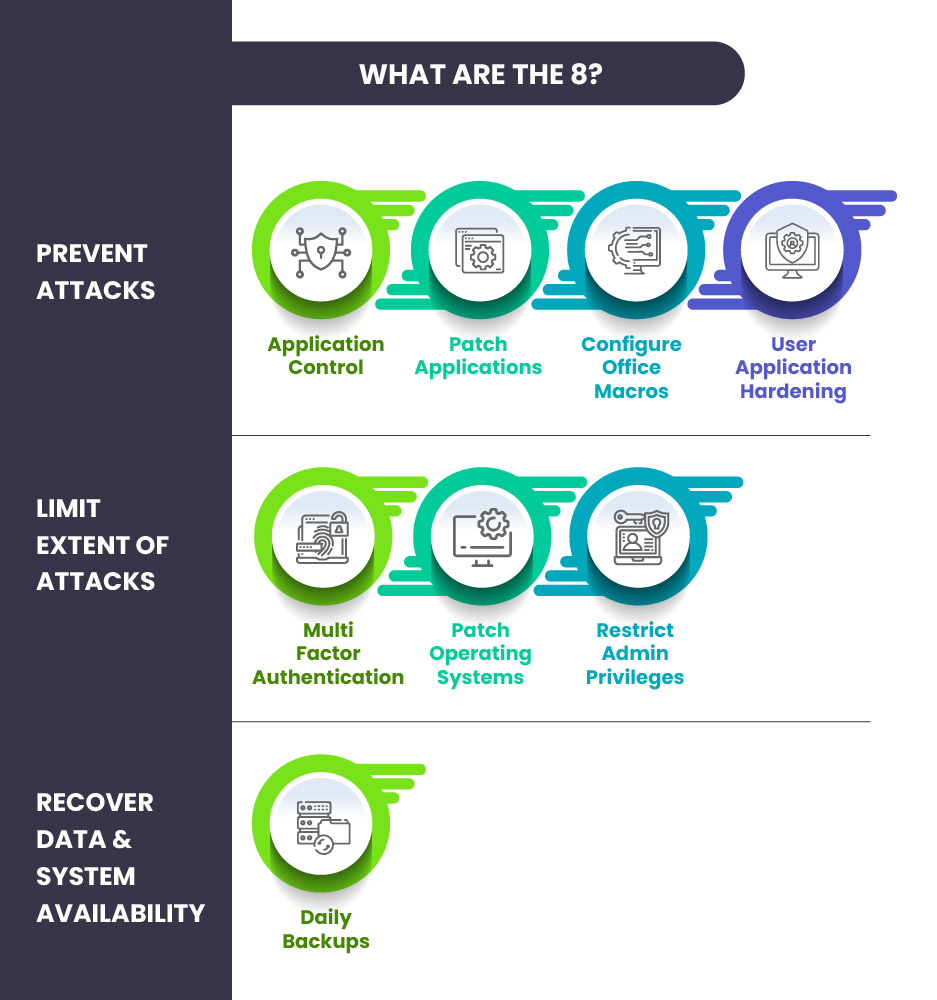
The Essential Eight uses the maturity model as a measurement base to compare the organization’s maturity over eight controls. These eight security controls are categorized into three objectives:
-
- Prevent Attacks
- Application Control
- Patch Applications
- Configure MS Office Macros
- User Application Hardening
- Prevent Attacks
- Limit Extent of Attacks
- Multi-Factor Authentication
- Patch Operating Systems
- Restrict Admin Privileges
- Recover Data & System Availability
- Daily Backups
Let’s discuss the eight essential pillars of cybersecurity in detail:
Application Control: Application Control allows the start of an application to be reviewed and approved by an IT administrator. It maintains control over applications to mitigate the chances of malware, viruses, or ransomware attacks that a hacker can install in the system.
Patch Applications: A patch Application is an essential element required to identify or fix the identified vulnerabilities in the applications because hackers can use security vulnerabilities in the application to run malicious code, which leads to exploitation. It is recommended to patch the extreme-risk application vulnerabilities within 48 hours. This process helps to secure and maintain the applications with the latest updates.
Configure Microsoft Office Macros Settings: ACSC recommended updating the default macros settings in Microsoft applications. Macros are the set of codes embedded into the document to automate tasks. It is essential to ensure that all unnecessary macros are blocked from the internet to avoid hacker-embedded macros in the Microsoft application.
User Application Hardening: Application Hardening blocks settings and content in web browsers and applications. It mitigates the flash ads and javascript that delivers and executes malicious codes in the system.
Multi-factor Authentication: Multi-factor Authentication is the most important element that helps to enhance security. It prevents the hacker from accessing the application and mitigates cyber attacks. MFA offers two pieces of evidence when logging into an account: six-digit secure codes, one time passwords, etc. It makes it difficult for adversaries to access confidential information to exploit. MFA includes SSH, VPNs, RDP, and other remote access.
Patch Operating Systems: It is essential to update the operating system to apply the latest patches. Maintaining maturity level 3 for this element is required to ensure that the latest operating system version is updated. When extreme risk vulnerabilities are identified, it is required to patch the computers, servers, and devices within 48 hours.
Restrict Administrative Privileges: Restrict Administrative Privileges is the best practice to maintain minimum permission for the admin users. It makes it challenging for the hacker to execute malicious code without having admin privileges. Not only in the primary applications, but it also applies restrictions for other services like web applications, HR accounting software, and CRM databases. A regular re-evaluation of privileges is essential to secure the data.
Daily Backups: Regular Backup is the essential pillar of cyber security. It is required to implement a backup plan that helps to recover from the security incident in no time.
Maturity Modeling
Essential Eight is based on the Maturity model that allows organizations to check and measure the essential eight pillars of cyber security. When implementing the following maturity model, an organization can evaluate the implementation of the cyber security principles on the above basic eight controls.
The four levels in the maturity model are:
- Maturity Level 0: The Cybersecurity principles are not aligned with the objectives of the mitigation strategy.
- Maturity Level 1: The Cybersecurity principles are partly aligned with the objectives of the mitigation strategy.
- Maturity Level 2: The Cybersecurity principles are primarily aligned with the objectives of the mitigation strategy.
- Maturity Level 3: Cybersecurity principles are fully aligned with the objectives of the mitigation strategy.
The cyber security principles are enforced, meeting the standard business practices, and robustly implemented throughout the organization. Every level (excluding Maturity Level 0) is designed based on the adversary’s tradecraft, such as tools, techniques, and procedures. It provides a systematic approach to implementing migration strategies. Maturity Level 1 determines the least secure, and Maturity Level 3 defines the most secure.
Become a Security Expert with InfosecTrain
InfosecTrain has a number of benefitted professionals who cleared their CompTIA Security+ certification seamlessly. It provides an expert-curated CompTIA Security+ online training course that covers the latest security trends, vulnerabilities, risk management, and incident response concepts. If you want to become a security expert, do check out and enroll.




 1800-843-7890 (India)
1800-843-7890 (India) 
