Top 5 Ways To Defeat Cyberattacks

Table of Contents
Introduction
Ways to protect ourselves from cyberattacks
- Use strong passwords
- Use Multi-Factor Authentication (MFA) method for better security
- Manage your social media account settings
- Do not trust every message or email you receive
- Install antivirus software and update them regularly
Introduction
With the increased use of digital space in our day-to-day activities, cyberattacks and threats are also continually evolving. We share a lot of our personal information on digital platforms, and cybercriminals could steal this personal information, and you could lose your funds, identity, livelihood, or even your life. But the good news is that you may utilize a variety of strategies to outsmart cybercriminals.
As a result, whether you are tech-savvy or not, cybersecurity is an essential facet of everyone’s digital life. Although professionals can assist in the security of your digital environment, it is your job as a user to maintain yourself safe from cyberattacks.
In this article, we have discussed five ways you can protect yourself from cyberattacks.
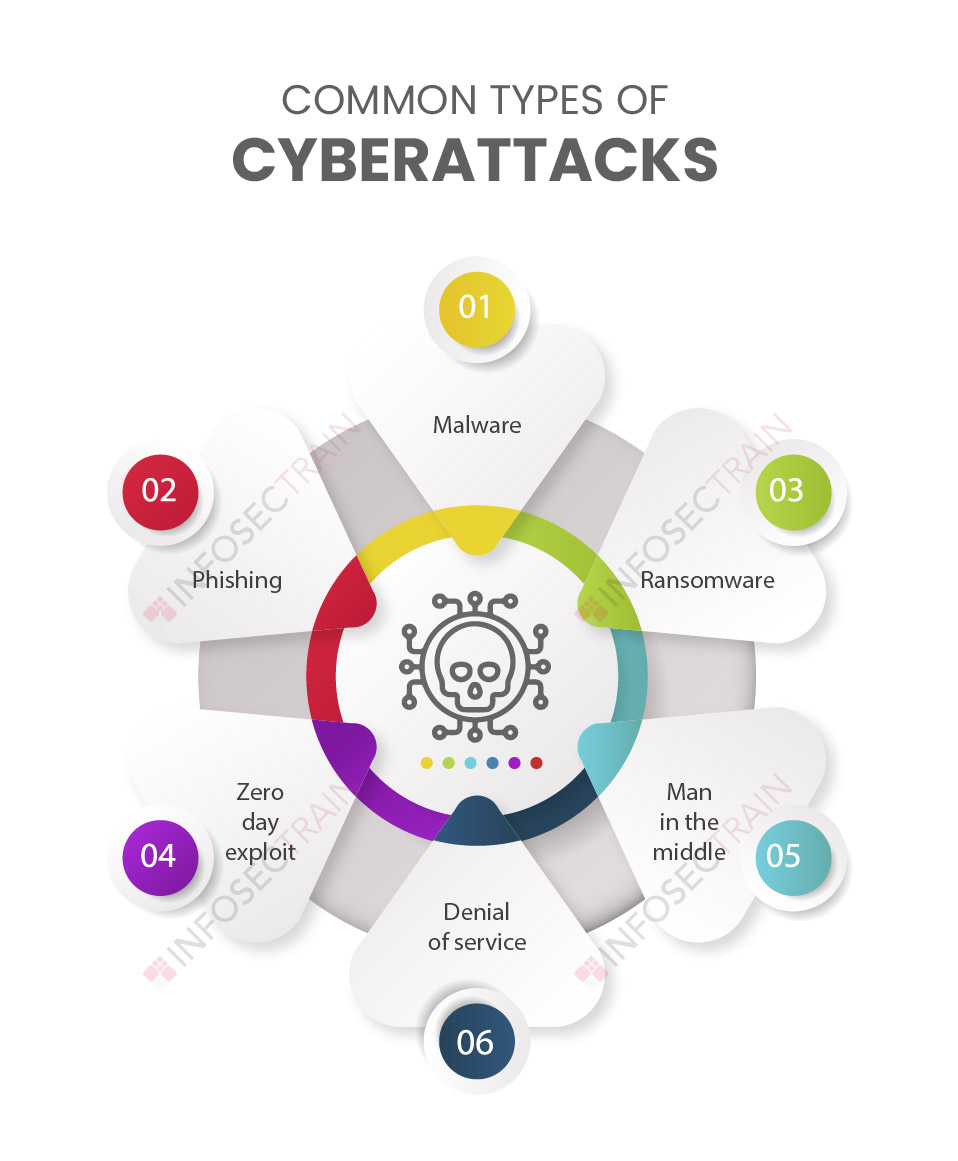
Ways to protect ourselves from cyberattacks
1. Use strong passwords: You should create a unique and strong password for your accounts and devices. When selecting a password, keep in mind that the longer it is, the more secure it is. A secure password is at least 12 characters long and difficult to guess. Everyone should use letters, special characters, and numbers to construct strong passwords. Passphrases are more difficult for hackers to crack because they are longer and more complicated, containing a mix of unrelated, capitalized, and lowercase words, digits, and special characters. To learn more about passwords, you can go through ‘The DOs and DON’Ts of Passwords’.
Tip 1: You can check the strength of your password by using “https://www.security.org/how-secure-is-my-password/”.
Tip 2: Avoid passwords like your date of birth, phone number, any chronological numbers, and others like 123123, QWERTY, and 111111, which are the most common and easiest to crack.
2.Use Multi-Factor Authentication (MFA) method for better security: You all know that having a strong password is essential. However, even passwords are not always sufficient to ensure security. As a result, you should use other secure methods like Multi-Factor Authentication (MFA), also known as Two-Factor Authentication (2FA), whenever possible. MFA defines security features in which getting into a system or app needs providing a password, but the user is subsequently sent a confirmation code to a mobile device or email, which they must enter as well. With this method, even if a password is stolen, a hacker would need access to another password or device to access your sensitive data.
3. Manage your social media account settings: Cybercriminals may scour social media posts for information typically used in security questions, such as a pet’s name or the maiden name of a mother. It would be best to make your accounts private or avoid posting important information on social media to mitigate this risk.
4. Do not trust every message or email you receive: Phishing attacks are prevalent, and they are becoming more sophisticated these days. Phishing is a deception used by cybercriminals to get you to divulge personal information such as passwords, credit card numbers, and other sensitive data. Always be on the watch for phishing emails and compromised websites, and interacting with them puts your data at risk and can lead to the download of malware.
If you are unsure about a link, trust your senses and ponder before you click. It could be a text message, phone call, or email.
5. Install antivirus software and update them regularly: You should use security software to secure all of your gadgets, including mobile phones, PCs, tablets, smartwatches, and more. On all networked devices, install and update antivirus software or firewall systems. It can protect you from malicious crooks and prevent you from visiting inappropriate websites. Set the software to automatically update so that it can handle any new security threats.
Bonus Tips:
- Update all of the software and applications of your device: All of your devices should have their operating systems updated. Also, update the software and applications on all of your devices, particularly the web browsers. It will make it more difficult for bad actors to take advantage of system vulnerabilities.
- Educate yourself: Educate yourself about the latest cybersecurity trends and best practices. You should educate yourself and your family on proper internet usage. You can enroll in a professional course to ensure that you acquire the appropriate amount of training and understand what you need to do to keep your data secure. There are various courses available for free or at pocket-friendly prices on platforms like YouTube, LinkedIn, and Udemy. Remember that the time you invest in acquiring the knowledge and skills required to secure your digital space and the little practices you adopt will help you save an enormous amount of damage. So go ahead and learn!
Final words
Nevertheless, we believe that if you can implement the ideas or procedures outlined in this article, you will see significant improvements in how you defend your digital environment and respond to cyberattacks.
We can minimize the burden we place on others to secure our digital environment if we collectively become mindful citizens of this digital world.
You may learn more about how to prevent cyberattacks by enrolling in one of InfosecTrain‘s several cybersecurity and IT security training courses. We are a significant provider of cybersecurity training all around the world. We also provide LMS courses that allow you to learn and upskill at your own pace, at your convenience, and at a minimal price. Choose as per your needs!




 1800-843-7890 (India)
1800-843-7890 (India) 
