OWASP Top 10 Vulnerabilities 2021 Revealed
Open Web Application Security Project acronym OWASP is an online community that creates web application security articles, approaches, documentation, tools, and technologies. It is a non-profit organization designed to boost web application security.

What is the OWASP Top 10?
The OWASP Top 10 is a list of the top ten most prevalent web application vulnerabilities. It also depicts the threats, consequences, and countermeasures. The main goal is to increase awareness and provide a framework for prioritizing application security initiatives. The OWASP Top 10 can be used to address the most prevalent threats and vulnerabilities that put your company at risk. The most recent OWASP vulnerabilities list was produced in 2021, and it is updated every three to four years.
What is a vulnerability in cyber security?
Let us first understand what a vulnerability is in general to comprehend OWASP’s Top 10 vulnerabilities. Any flaw in an organization’s information systems, internal controls, or system processes that cybercriminals can exploit is referred to as a cybersecurity vulnerability.
Cybersecurity vulnerabilities are critical to monitor in terms of your organization’s overall security posture, as network weaknesses can lead to a full-scale system breach. Cyber adversaries might get access to your system and collect data by exploiting points of weakness.
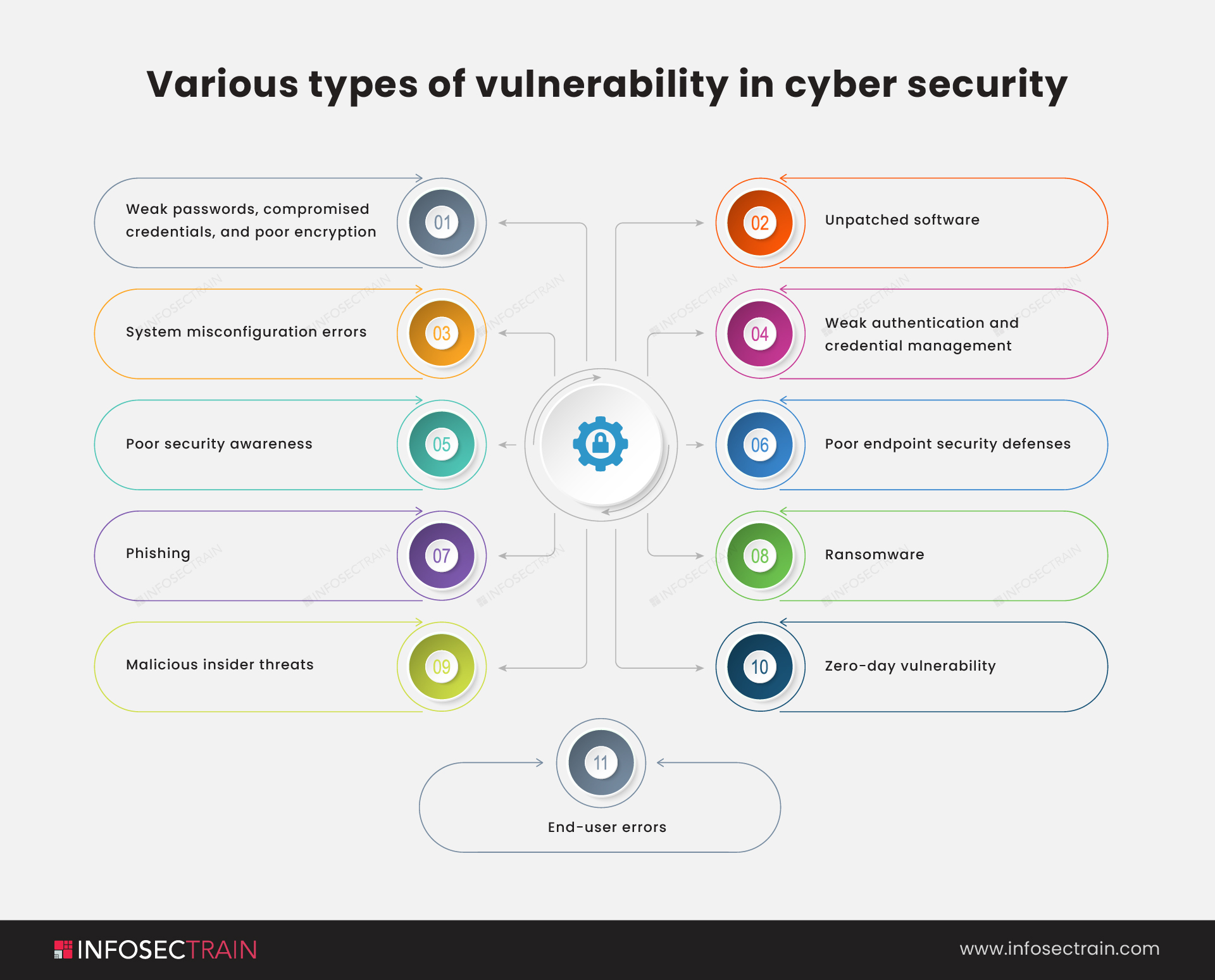
What are the OWASP Top 10 vulnerabilities for 2021?

1. Broken Access Control: In the OWASP Top 10 list for 2021, broken access control is one of the most hazardous web application vulnerabilities. It was previously thought to be a small risk. Access control is a security approach that regulates who or what can view or utilize IT resources. It is an essential security concept that reduces the risk to the company or organization. When users can access a resource or perform an action that they are not meant to do, they have a broken access control vulnerability. Broken access controls are a common and often severe security flaw. It had more occurrences in applications than any other category, as mapped by 34 CWEs.
2. Cryptographic Failures: Cryptographic Failure was formerly known as Sensitive Data Exposure, and it jumped from third to second place on the 2021 list. It focuses on cryptographic failures, which frequently result in the exposing of sensitive data or system compromise.
Cybersecurity specialists use cryptography to create algorithms, ciphertext, and other security measures that codify and secure company and consumer information. Cryptography, in simple terms, is the study of secure communications techniques that allow only the sender and intended recipient of a message to read its contents. It is used to keep private passwords and other sensitive information safe online.
3. Injection: Injection flaws occur when untrusted user data is sent to the web application as part of a command or query. Injection happens when a cyber attacker injects malicious data into a web application, handled in an unsafe way. The attacker’s malicious data can cause the web application to run unintended commands or access unauthorized information. Injection drops to third place on the OWASP Top 10 list. In this edition, cross-site scripting has been added to this category.
SQL injections, Cross-Site Scripting (XSS), NoSQL injection, code injection, OS command injection, host header injection, and other types of injection attacks are among the most prevalent ones. These injection attacks target the following functionality:
- Structured Query Language (SQL) query
- Operating System (OS) commands
- XML path language (XPATH) query
- Lightweight Directory Access Protocol (LDAP) query
4. Insecure Design: Insecure Design is a brand-new category for OWASP Top 10 2021, focusing on the risks of design faults. Insecure design occurs when a vendor adds documented “features” to a product that allow an attacker to undermine the application’s availability or integrity. Because appropriate security safeguards were never built to fight against specific threats, and a perfect implementation cannot repair unsafe design.
OWASP recommends, “We need more threat modeling, safe design patterns and principles, and reference architectures if we genuinely want to “move left” as an industry.”
5. Security Misconfiguration: Simply put, Security Misconfiguration is the failure to implement all of a web application’s security controls or the implementation of security controls with mistakes. The former category for XML External Entities (XXE) is now a part of this risk category, which rises from the sixth position in the previous edition.
6. Vulnerable and Outdated Components: Any software or code that is vulnerable, unsupported, or out of date falls into the Vulnerable and Outdated Components category. It has climbed up from the ninth place and was formerly named ‘Using Components with Known Vulnerabilities.’
7. Identification and Authentication Failures: The ability to uniquely identify a system user or application operating on the system is known as identification. Authentication refers to the capacity to establish that a user or application is who they claim to be. The Identification and Authentication Failure leads to the exploitation of user credentials and data breaches. When a user’s identification and authentication are not handled properly, attackers can leverage passwords, keys, session tokens, or implement vulnerabilities to temporarily or permanently assume users’ identities. It replaced Broken Authentication as the second most common CWE and now covers CWEs more closely tied to identification failures.
8. Software and Data Integrity Failures: In 2021, a new category called Software and Data Integrity Failures will focus on making assumptions about software updates, essential data, and CI/CD pipelines without validating integrity. This category now includes Insecure Deserialization.
9. Security Logging and Monitoring Failures: Security Logging and Monitoring Failures were formerly Insufficient Logging and Monitoring. It has been included in the OWASP Top 10 survey, going up from the tenth position. Errors in detecting, escalating, and responding to active breaches fall within this category. It is impossible to detect breaches without logging and monitoring. A website compromise might be significantly worse if you don’t have a good logging and monitoring system in place.
10. Server-Side Request Forgery: Server-Side Request Forgery or SSRF is a web security flaw that allows an attacker to force a server-side application to send HTTP requests to any domain the attacker chooses. This category depicts a scenario in which security community members tell us something is essential even though it isn’t depicted in the data.
What is the importance of the OWASP Top 10?
The OWASP Top 10 helps organizations understand, identify, mitigate, and correct vulnerabilities in their applications by giving them a priority over which risks to focus on. Each vulnerability is assigned a priority based on its prevalence, detectability, impact, and exploitability.
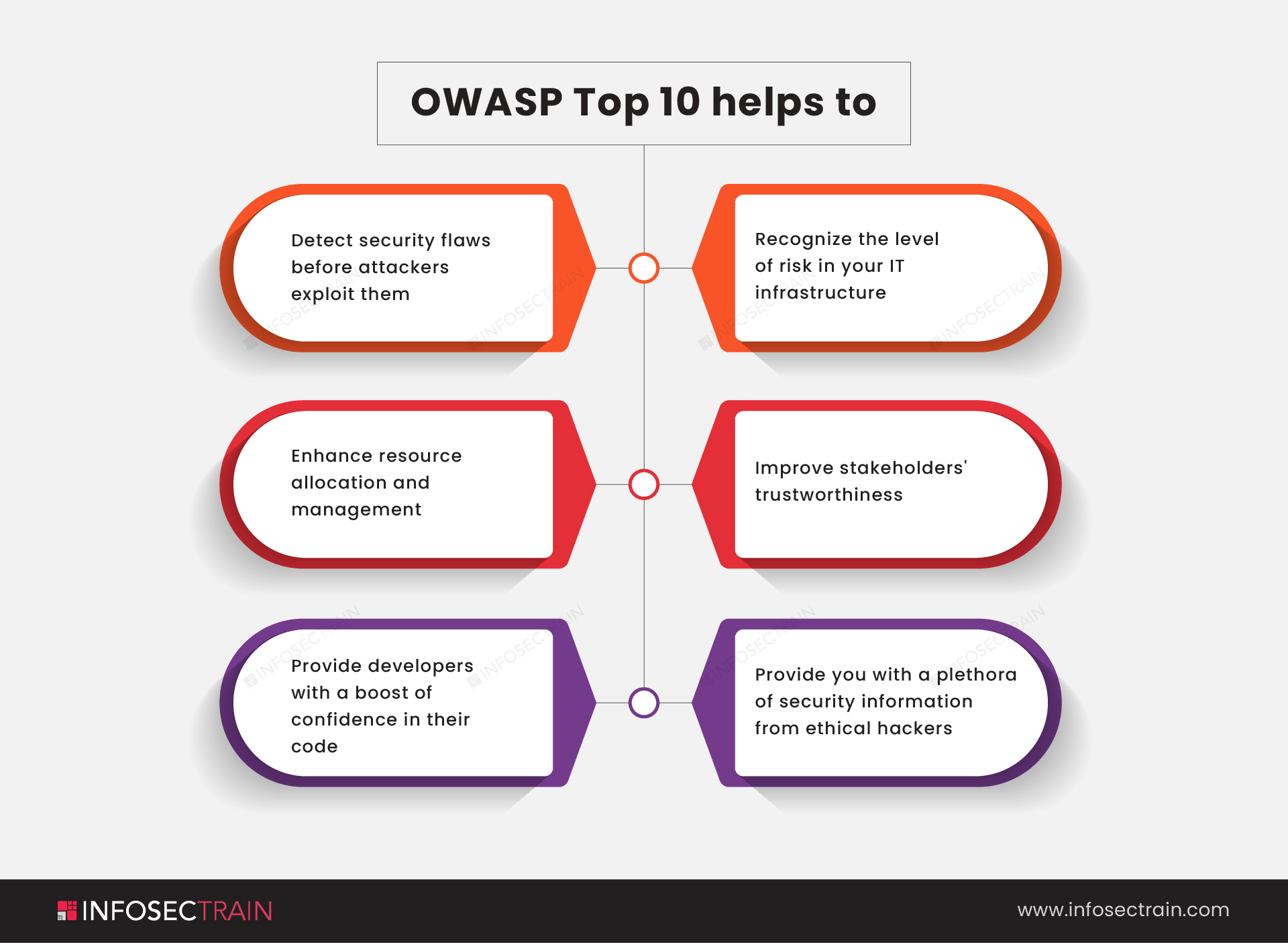
Final Words:
Over the last four years, the threats to application security have evolved. Three new categories: Insecure Design, Software, and Data Integrity Failures, and Server-Side Request Forgery, were added to the OWASP Top 10 list in 2021 and numerous categories combined with others.
We at InfosecTrain are dedicated to helping you detect and combat these vulnerabilities in your IT systems and application software, thus helping protect your organizations. Enroll in our CEHv11 online training and certification course or various other security training courses to learn more about cybersecurity vulnerabilities and multiple countermeasures. Learn with our qualified instructors.




 1800-843-7890 (India)
1800-843-7890 (India) 
