MITRE ATT&CK for Red Teaming
Attack simulation can strengthen the organization’s security to handle real-world attacks and reduce a breach’s detection time. Security experts can perform simulations of real-world attacks by observing and investigating the attacker’s behavior and intention of attack. In this comprehensive blog, we will discuss how the MITRE ATT&CK framework is used in Red Teaming.

What is MITRE ATT&CK Framework?
The MITRE ATT&CK framework was curated in 2013, an accessible document including attacker’s tactics and techniques used in real-time attacks. This index would continue to include the threats and has turned out to be a handy record for organizations to understand an attacker’s methodologies, models, and mitigation.
Comprehensive threat detection requires understanding the adversary techniques and how to detect and mitigate the attacks. It is nearly impossible for a single organization to understand and monitor every attack. To help the organization understand the attack, MITRE has developed the Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) framework.
MITRE ATT&CK includes three matrices, Pre-ATT&CK, Enterprise ATT&CK, and Mobile ATT&CK. These matrices comprise an end-to-end attack chain that helps understand the adversaries’ actions and accelerates the detection and response of an attack.
| Pre-ATT&CK | Enterprise ATT&CK | Mobile ATT&CK |
| A set of techniques, tactics, and common knowledge focuses on attacker’s behavior outside an enterprise. | A set of techniques, tactics and common knowledge focuses on attacker’s behavior inside an enterprise. | A set of techniques, tactics and common knowledge focuses on attacker’s behavior inside an enterprise, particularly in the mobile environment. |
It includes three stages:
|
It includes four stages:
|
It also includes the same four stages of Enterprise ATT&CK:
|
How does the Red Team use the MITRE ATT&CK framework for an effective simulation?
Using the MITRE ATT&CK framework, the red team can identify the behavior of adversary groups and can take effective action for the simulation and detection process.
The Red Teaming simulation process includes two stages:
- Stage one: Breach the organization from the outside and simulate the damage.
- Stage two: Identify the attacker who carried out the breach inside the organization.
The “Pyramid of Pain” defined by David Bianco describes how easy it is for an attacker to modify the behavior of an attack. Let’s look at some of the most prevalent methods and how attackers would render them ineffective.
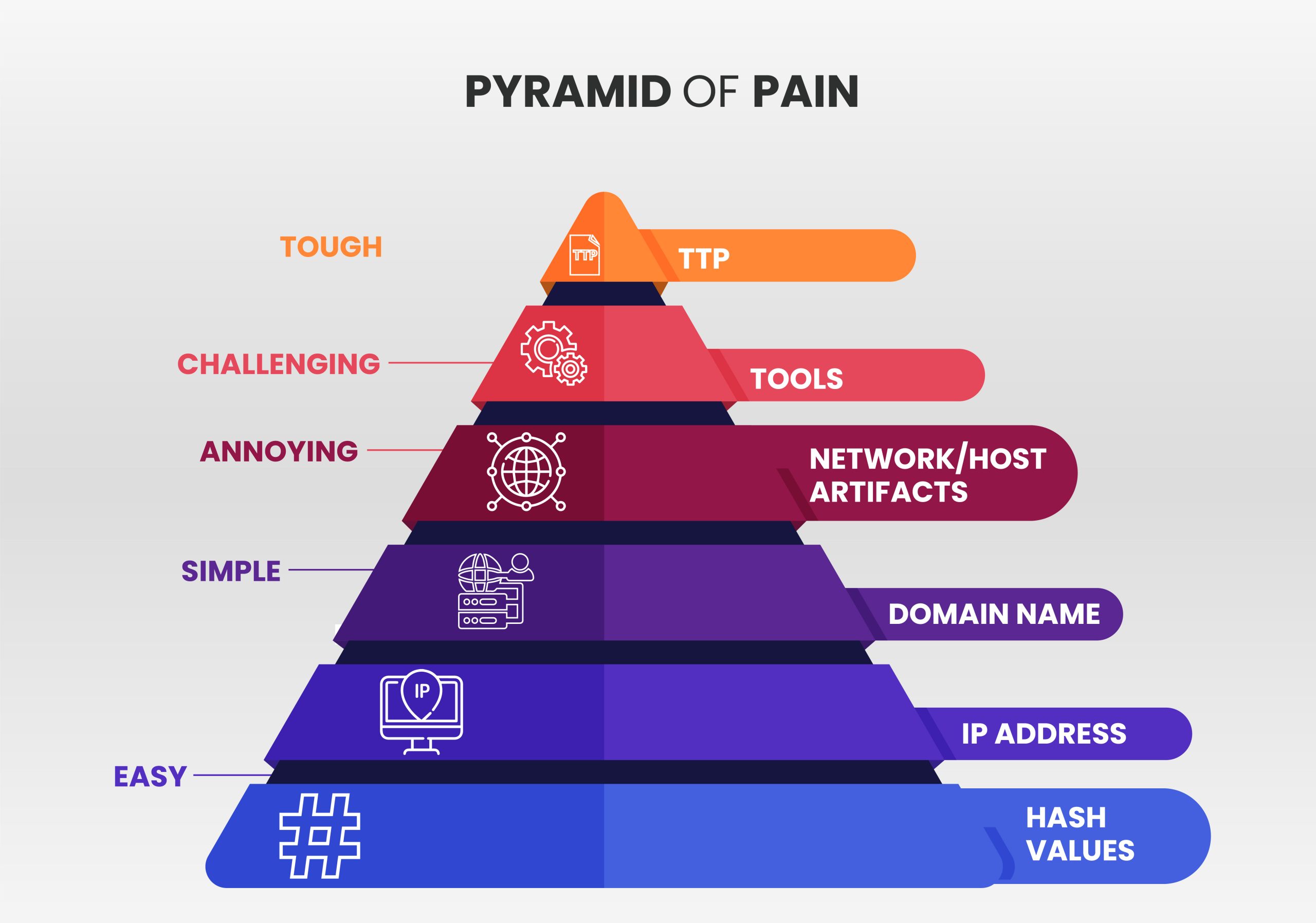
The pyramid of pain represents six types of attack indicators that are arranged in ascending order based on the impact and effort of the security analyst.
Hash Values
Cryptographic hashes such as SHA1, SHA256, and MD5 are the most frequently used Indicators of Compromise (IOCs) in cybersecurity defense systems: IDS/IPS, antimalware, and others. Adversaries can modify Hash values and readily overcome defense systems using polymorphic or metamorphic methods.
IP addresses
Script clowns use their IP addresses, although IP addresses are the most common indicators of attack. Adversaries use Tor, VPNs, and anonymous proxies to modify their IP addresses. Cybercriminals can perform an attack effortlessly by navigating around defensive systems with IP address restrictions.
Domain Names
Domain names are difficult to modify since they need pre-registration. Threat actors can use APIs to change domain names automatically using Domain Generated Algorithms (DGA) and Dynamic Domain Name System (DDNS) services.
Network / Host Artifacts
In a network or host, artifacts are the components of an action that distinguish between malicious and legitimate actions. Command and control (C2) information, URL patterns, directories, files, registry objects, and other networks/host artifacts are examples.
Tools
Attackers enhance their tools, making them more complex. These tools are often designed to scan for bugs, create and execute malicious code, set up C2 connections, break passwords, and perform other tasks.
Tactics, Techniques, and Procedures (TTP)
TTPs are the methods used by an attacker, and it is the toughest challenge for cybersecurity professionals. An attack’s behavior helps security professionals understand, investigate, and respond to the attack. When attacks are addressed using TTPs, attackers struggle to achieve their objectives.
Each level of the pyramid of pain provides a scope to prevent various IOCs and obtains optimal value for cybersecurity defense and threat intelligence investments.
MITRE ATT&CK framework helps to strengthen the measures and prepares for an adversary attack. This framework has maintained a list of groups along with targeted group records. Connect them to the attack simulator in various layers. The attack framework has the advantage of correlating the TTPs over multiple layers.
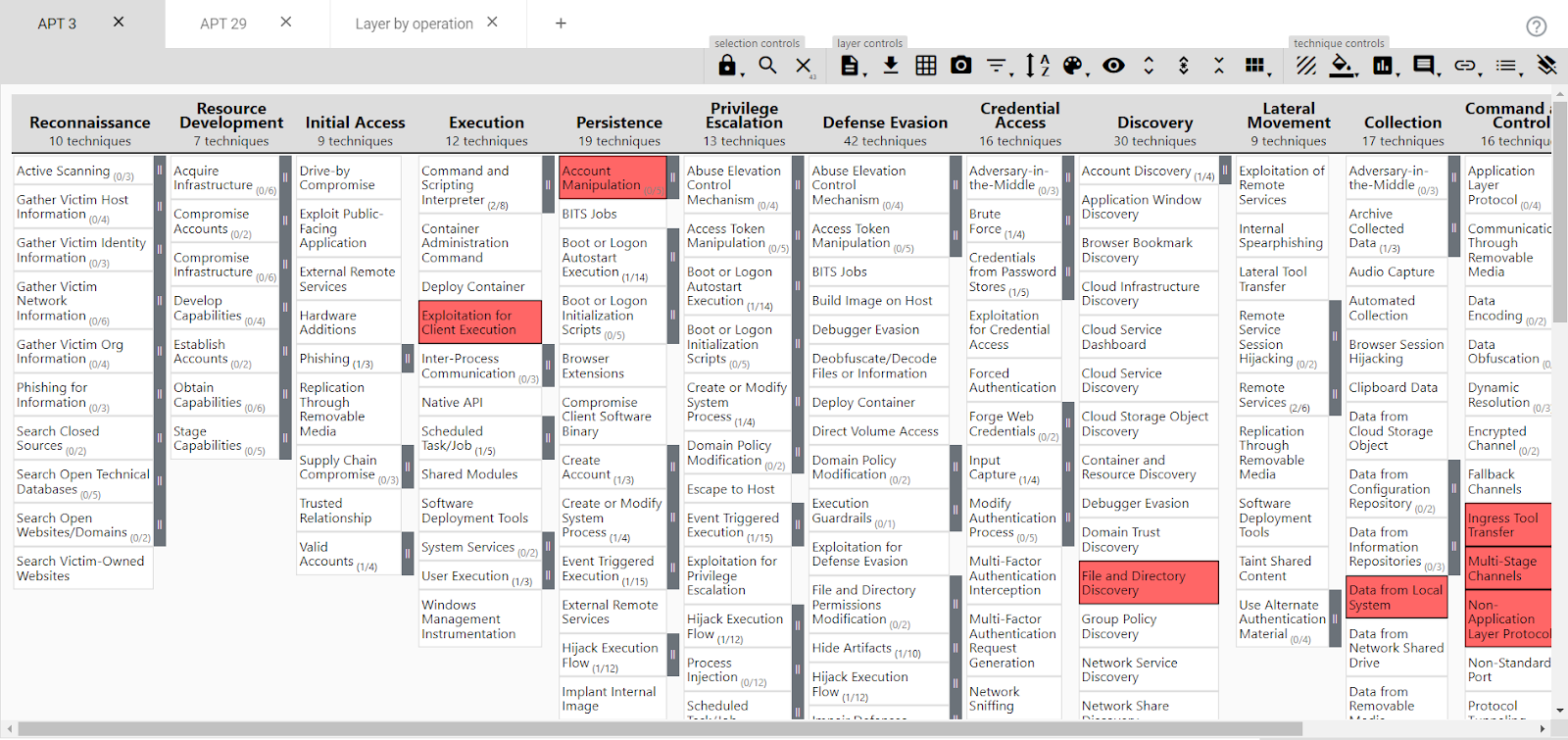
Let’s check an example of two adversaries, APT 3 and APT 29
APT 3: Highlighted in Red are the TTPs
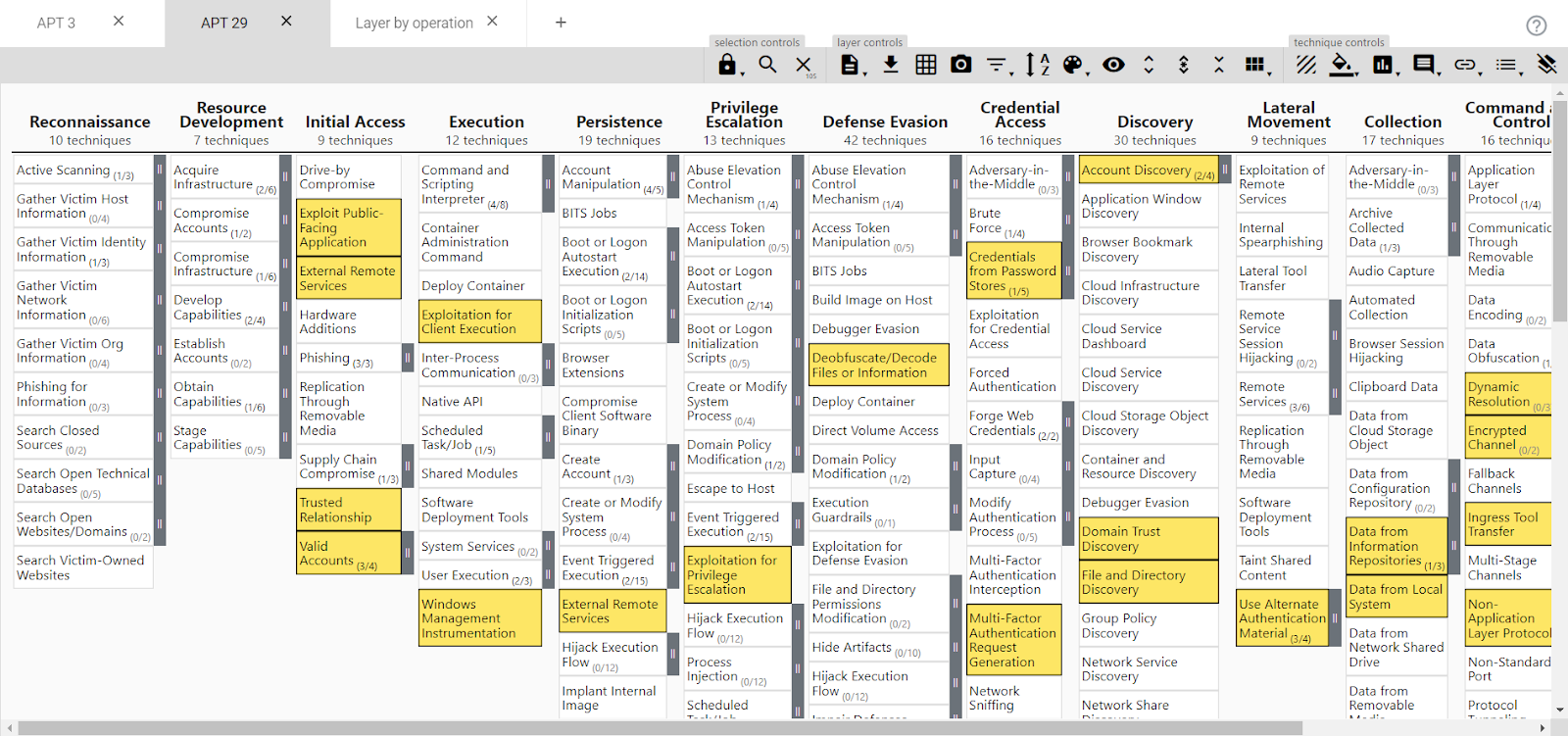
APT 29: Highlighted in Yellow are the TTPs
This framework also allows users to create a new layer to locate the common techniques of two other APT TTP layers based on the score expression.
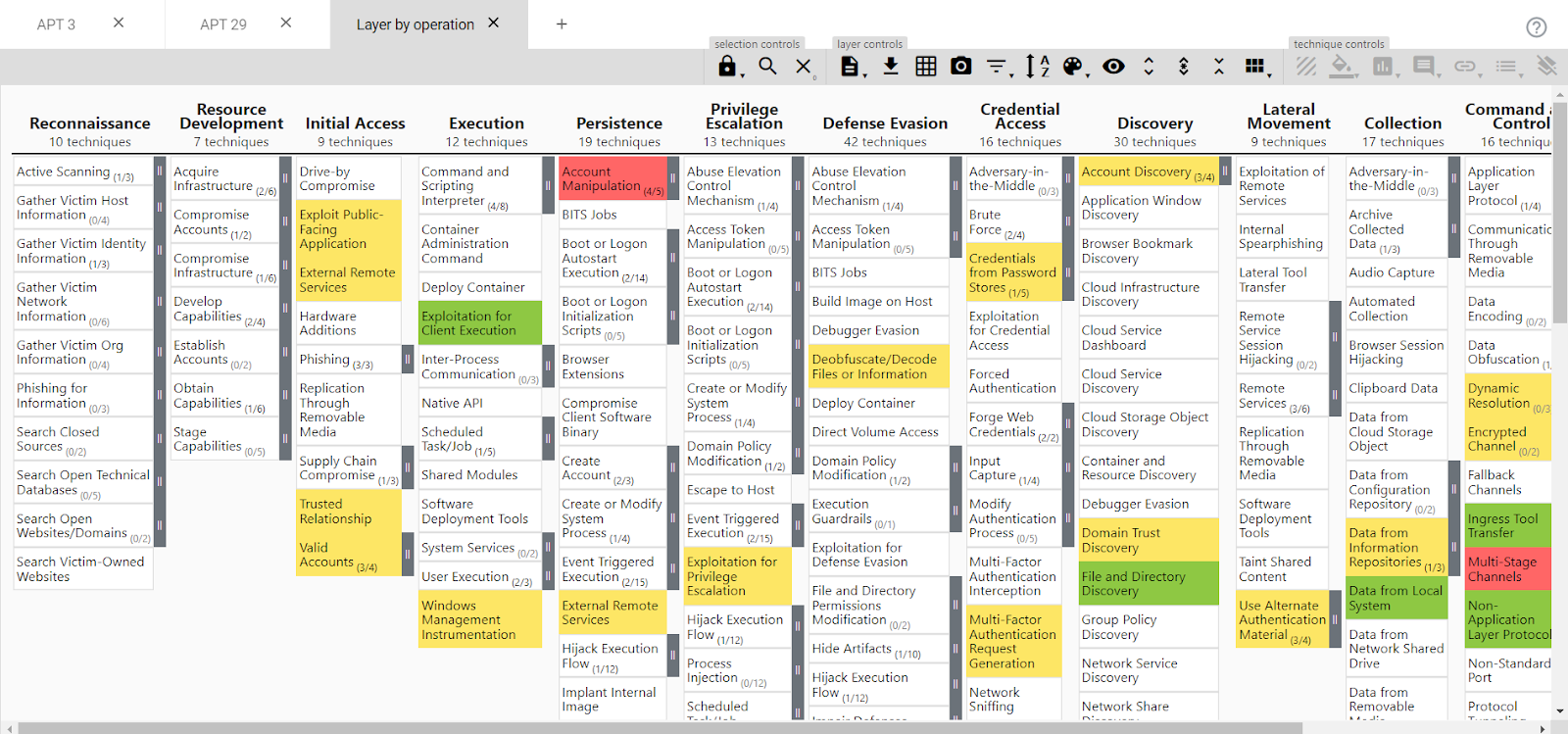
APT 3 and APT 29: Highlighted in Green are the common techniques used for both APT layers.
From a red team perspective, there are several use cases. For instance, a red team can use ATT&CK to label activities in a report for reference and map their gaps to ensure the products in the environment can be turned to address the detection gap.
The red team tracks the TTP coverage over campaigns by creating a metric, mainly when targets are repeating and checking how many TTPs get covered during a rolling period. It is known as MITRE ATT&CK Bingo or bingo card. Red team professionals aim to add 3-5 new TTPs to ensure the Blue team can identify varied attacks in each campaign.
Also, the MITRE framework has developed an online interactive navigator, a web-based tool for annotating and exploring ATT&CK matrices. It visualizes defensive coverage, frequency of detected techniques, red team planning, and many more.
MITRE ATT&CK with InfosecTrain
InfosecTrain offers instructor-led training on MITRE ATT&CK online training and certification course. It helps you get in-depth knowledge of the various adversary tactics and techniques to defend a network based on real-world cyberattacks. If you wish to become a security expert, check out and register for MITRE ATT&CK online training course.




 1800-843-7890 (India)
1800-843-7890 (India) 
